On Sun, Nov 6, 2022 at 11:16 AM Eric Karlstrom
I. Bobbi Peitsch’s email message (1) to Eric Karlstrom on Nov. 7, 2022:
Eric, your message was:
Eric: Hi Bobbi, Your computer forensic abilities far surpass the rest of us, probably.
When you say we are hacked- you mean biohacked as in they can see through our eyes, hear through our ears, plant subliminal thoughts, I suppose?
Bobbi: Eric, your computer is hacked and your body. They use the remote ability of the wifi to assault you. While I do not experience V2k, I have multiple spots in my body that produce frequency that is detectable, and when there is screen disruption, I get a body shot in those spots (because my TV is wifi enabled including my PC- which is connected to it.
In one spot, I have confirmation of an artefact in my shoulder, I asked for it to be removed, and my doctor told me no one in Canada would remove it. If it does not belong there, it is elective surgery and I should have the right to have it removed from my body, I guess I do not.
Eric: When you say a geofencing system, I assume you mean our locations are constantly monitored and known with GEOINT type equipment? And that this information system is called geofencing?
Bobbi: Geofencing is a system used in surveillance, advertising (with UUIDs (Universal Unique Idenitier)/BLE (Bluetooth Low Energy), etc) and property surveying and for anything you want to use it for, including setting up alarms for a “tagged” person or object such as an expensive piece of equipment that has a BLE device attached to it. All victims are routed to the OFAC (Office of Foreign Assets Control)- which in turn routes directed to the USA Treasury Department, ask yourself why.
Geofencing I found in my computer system, which was registered to a small company several thousand km away.
The BLE/ Transmitters are used in sending and receiving information, the greater the range of the system using specific bands, means people can access them remotely or belt out a specific signal using bands (17, 5, 29, etc) that are used in Wideband Code Division Multiple Access (WCDMA) networks (which I have found to be in use) which are also used by the Military.
The reason no one can “block” the frequencies is because they are using frequency hopping. With frequency hopping you can use multiple bands/ 2,3,4,5 g networks making it harder to block.
Do not forget, VOICE can be transmitted including images over networks with Wifi, and Wifi has been around for a couple of decades now. Also do not forget ARPA/ Darpa actually were the first ones using the internet. You also have the Neurophone, which is still in use today. Anyone can build them, it is a BCI- computer brain interface system– this is a clip from 2010- NeuroPhone: Brain to Mobile Phone Interface – YouTube
All of the system is network-based communications systems using masking, IP addresses, BLE, masking systems — I DID NOT come up with this factor, the whistle blower on it was Mr. Binney informing the world they were using network switches which are ASNs.
Now, I can tell you that Karen Stewart was correct… on the Fusion centers and the CIA…
I finally resolved them on myWHo are they:
computer this morning.
see the highlighted IP address? Well, they are all equal to a phone number resulting in a GPS location (which can be spoofed and or masked in a reversal of the IP, or in a blast of multiple dummy sites)
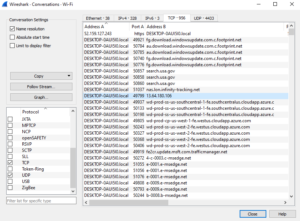

who are they
IPv4: 13.64.180.106 – AlienVault – Open Threat Exchange
lcia-projects (Louisiana Cyber Investigators Alliance) / October 2022 (github.com)
Louisiana State Analytical and Fusion Exchange (la-safe.org)
What I find most disturbing is how Bunny.net is always coming through on the network, they are connected.
Charlie is a brilliant man, and I told him a couple of years ago to start writing it out and to stick it in a book.
Combined, with the networks, using applications such as Wigle.net and electrosmart and other network wardriving BLE detection tools you can get answers when you also combine it with your physical network.
The way I believe this can end for victims:
Frequency hop jamming
and ending recursive query into the computers.
Removal of the RFID tracking implants, because they exist, they are part of the body area network systems.
WIPO has thousands of documents on them. For example, WO2021011297 BODY AREA NETWORK FACILITATED AUTHENTICATION OR PAYMENT AUTHORIZATION (wipo.int)
It is what mainstream media will not discuss, body area network implants, how much money is made from them and who is making the money, which is all about research and development grants, and remote sensing with bioinformatics.
Today, alternative media is discussing everything about injectable self-assembling nano tech that generates a Blue Tooth address, but none of them are talking about Charles Lieber, or tracing the BLE signals on Shodan, they can all be traced, and they always trace to Germany-Austria, Switzerland, Ireland (automation of research projects as I recall).
I will email you from a new email address soon, this email is full.
II. 2nd Email from Bobbi Peitsch to Eric Karlstrom, Nov. 7, 2022
Before I get into my response, I would ask you and all others to spare a few moments for our beautiful friend Juliet (Targeted International) twitter.com/TargetedInt she is going through radical major surgeries for cancer right now.
(My research- I never stop I am trying my best for my family and others).
Ending it:
Removing the Wi-Fi from your environment will help, but it will not eliminate the problem if you are part of a research project with WEF/ Military whomever, they will continue to collect the data and add BLE/ Antennas and systems into the environment, especially if you are on a watch list. I personally believe they expanded the watch list programs and made secret orders in multiple countries for the purpose of generating income through research and development, it is not an industry if you are robbing your population, it is also not innovative if you are stealing data and torturing another and taking their tax dollars to fund the research, that is economic suicide. Many countries specialize in specific research– cybernetics- robotics, biological integration, digital convergence/ singularity (Archons) I have a list of some that fund it -AI, etc.
Ending it includes: HScada scanning at every single hospital, after all their connected foundations work within Body Area Network- BioInformatics remote data collection (all the time not everyone but many).
Ending Private Military contracts, including examination of all income through pension funds and block chain and offshore accounts.
Policing of the backbone of the internet, human trafficking including biosignal data- it is intellectual property).
Examination of Project25 and its use (policing the police with signal trackers) https://en.wikipedia.org/wiki/Project_25 since Medical Home and Automotive are all under unlicensed bands.
Jammers using frequency hopping (but that is illegal), removing your Wi-Fi and getting hard wired including creating paint shielding with a combination of layered materials and grounding each one– lead paint (lead oxide much cheaper)/high temperature paint/tungsten, including your electrical lines/wiring. And eliminating the invisible mesh network in your environment or reducing it as much as you can– toaster, fridge stove, clocks, etc all have those little networks including LIFI– Lightbulbs and LED bulbs, everything is Wi-Fi mesh now, it is a thing, but just because you cant see it does not mean it is not hurting you. I Love this guy, he breaks it down for you.
Rob Braxman Tech
Hey Bluetooth, What’s New? : Oh, We Want to Chip You
Victims with part Body area networks, or a single tracking chip/ etc have to be removed, investigated.
All victims speak of recompense’, that only happens if you have done something wrong, when you are a slave, your body is owned and is deemed as intellectual property of someone else, especially if they have taken out a related patent on it– nice eh, that is a global law.
Victims will be lucky to end the torture and survive with any quality of life.
We can speak, beg to have the ear of one leader or someone who realizes this is going to happen to them, but none care, victims are blacklisted hacked, used and abused.
The value of a human today-
Soylent Green – we will recycle you and eat your drippings through the vegetables
Suicide is an option
Abortion is recycling parts and growing parts for others
Adults shall be not seen and not be heard – six feet under is the theme
If you rise up, they will beat you back, into a hole where you become afraid, so afraid the only thing you can do is type through this squawk box, and now even the squawk box can hurt you in every single way imagined.
—–
To my understanding WEF is researching cochlear implants and Alzheimer’s research and others, I guess everyone needs onto that global borderless research train where others are funding the research and intellectual property thief’s just take DNA and BioSignal data as their own, way worse than pirating a video they are pirating a person’s total identity– the self). Pepper in some property theft, and block chain and everyone gets paid while the victim is mocked and dies and called crazy, until there is evidence– based in FACT), but then again, they all make the rules so none can we all turn to.
I often wonder how they define a terrorist or international terrorist; I always thought it was about destabilizing an entire nation, causing economic destruction, planning on killing several etc … but what do I know right, clearly little old ladies with brain damage, and truckers are on the menu.
Of special note- Klaus Schwab-
“We penetrate the cabinets” https://www.youtube.com/watch?v=SjxJ1wPnkk4
In Canada, the definition of terrorist activity includes an act or omission undertaken, inside or outside Canada, for a political, religious or ideological purpose that is intended to intimidate the public with respect to its security, including its economic security, or to compel a person, government or organization (whether inside or outside Canada) from doing or refraining from doing any act, and that intentionally causes one of a number of specified forms of serious harm.
https://www.publicsafety.gc.ca/cnt/rsrcs/pblctns/rslnc-gnst-trrrsm/index-en.aspx
This is a nice example:
The Canada-China Promotion and Reciprocal Protection of Investments Agreement or Canada China FIPA is a bilateral investment treaty between Canada and China which came into force on 1 October 2014.
https://www.international.gc.ca/trade-commerce/trade-agreements-accords-commerciaux/agr-acc/fipa-apie/index.aspx?lang=eng
MEANING THIS: If one interferes with the trade and investment under these Foreign investment protection acts, Canada gets sued.
Jun 1, 2022 — Prime Minister Justin Trudeau’s government has adopted 72 secret orders-in-council — hidden from Parliament and Canadians —
https://www.cbc.ca/news/politics/secret-orders-in-council-1.6467450
——
A woman emailed me and Stew Peters, she had an blacklisted scan that confirmed IMPLANTS (multiple tiny rice sized), and she was able to confirm that it was the Patent 06 06 06. Here it is on the World Intellectual Properties Office:
1. WO2020060606 – CRYPTOCURRENCY SYSTEM USING BODY ACTIVITY DATA
https://patentscope.wipo.int/search/en/detail.jsf?docId=WO2020060606
She noted in her email that the patent disclosed that the implants are in people all over the world, some with informed consent, others had no idea, meaning they/ whomever have broken the International Criminal Court on human experimentation.
You have bafoons online making claims it is not inserted, it is explicit. Now, for currency and data to be generated there has to be an UPLINK and a DOWNLINK… two-way communications, making it a fully capable wireless communication system.
Method and apparatus for sending feedback for a downlink shared service transmitted to a plurality of wireless transmit/receive units
https://testpubchem.ncbi.nlm.nih.gov/patent/US-8509076-B2
If it is a two-way communication system IEEE https://ieeexplore.ieee.org/document/8244985 they approved, it with the FCC.
It requires to be powered… so it is WIRELESSLY CHARGING
https://ieeexplore.ieee.org/document/7914600/
With wireless charging, it introduces electricity which is radio frequency (AC/DC current same thing, can convert between the two as you already know).
Energy Harvesting for Self-Sustainable Wireless Body Area Networks
https://ieeexplore.ieee.org/document/7914600
Wireless body area networks are a part of IEEE Sustainable Develpment goals, I sent that to you awhile back.. so it is in the future, which is tomorrow, lol.
If you have “nodes/ piconets” (implants) communicating in the human body and wirelessly charging, that is assault with a deadly weapon depending on how many have been placed into the human body — especially without informed consent and a VICTIM is called delusional when they experience pain going near electricity — Wires/ plugs, anything generating energy.
There are loads of disorders from exposure, Wi-Fi is electromagnetic radiation – nonionizing radiation is still radiation.
Neurological cognitive disorders, such as headache, tremor, dizziness, loss of memory, loss of concentration and sleep disturbance due to RF-EMF have also been reported by several epidemiological studies (Kolodynski and Kolodynska, 1996; Santini et al., 2002; Hutter et al., 2006; Abdel-Rassoul et al., 2007).
https://www.ncbi.nlm.nih.gov/pmc/articles/PMC6513191/#:~:text=Neurological%20cognitive%20disorders%2C%20such%20as,et%20al.%2C%202007).
There are exposure limits in Canada for workers which alls unders safety code 26:
https://laws-lois.justice.gc.ca/eng/regulations/SOR-86-304/section-10.26.html
Limiting exposure to 150 mV for a short period of time.
There is no enforcment in the communites for electromagnetic radation exposure, none to complain to for measurement investigations. There are also no cancer research studies (which is international law according to Barry Trower) BEFORE a tower or major wifi system goes in, and one conducted two (2 years) after to see how the communities health is doing with the beastly abnormal- never existed in nature at these levels before — Radio Frequencies.
WHO defined limits of exposure to non ionizing radation exposure to 100mV for short periods of time. I am unsure if they have changed this, as I have not reviewed the data in a few years https://www.who.int/health-topics/electromagnetic-fields
(disappointed with the lack of performance by Nils Melzer on CyberTorture enforcement) https://gcils.org/author/nils/
Last interview I watched that he gave was by Useful Idiots https://usefulidiots.substack.com/p/reacting-to-assange-verdict-with#details
(I believe you mentioned useful idiots, too lazy to check back).
The current world Authority on exposure and frequencies is Barry Trower (I am confident in his disclosures), you should try to call him and do an interview, he is a lovely person, his wife took the time to spare a few moments for me. He knows all of the frequencies, and diseases generated from them. Contact data-
https://www.facebook.com/BarrieTrower/
I have made notes and will continue this a little later, as there are additional things you need to be made aware of, just aa wee bit tired and woorried about Juliet, she has not called me yet.
III. Eric Karlstrom’s email message to Bobbi Peitsche on Nov. 6, 2022:
Hi Bobbi,
Your computer forensic abilities far surpass the rest of us, probably.
When you say we are hacked- you mean biohacked as in they can see through our eyes, hear through our ears, plant subliminal thoughts, I suppose?
When you say a geofencing system, I assume you mean our locations are constantly monitored and known with GEOINT type equipment? And that this information system is called geofencing?
Would you please look this message and post I reference here over and see if you agree? ” Lookoutfa Charlie” has done some very insightful videos on this, I think, and seems to think there is one weaponized surveillance system everywhere and it runs off of AI. He maintains the voices are AI chatbots.
(Lookoutfa Charlie states: “this technology runs 24/7 365, everywhere. It’s not a bunch of different things. It’s one thing.” )
If you could look over my best efforts to understand what he is saying and let me (us) know if you agree, that would be great. Also, please let me know what you think needs to be added to my quasi-quantitative equation that tries to explain the targeting program.
Those of us with limited technical abilities in this area need some help to understand what is happening.
Below from the introduction to my latest post, which I have been revising as I come to grips with and try to summarize the information. Do you agree with this? If not, please tell me (us) why.
All best wishes,
Eric
WHAT, WHO, WHY, and HOW Of Weaponized Radio Frequency Surveillance System (partial transcriptions of 5 ‘Lookoutfa Charlie’ videos w/ BONUS videos On US Air Force’s “Chart of Coercion”)
Posted onOctober 31, 2022AuthorEric KarlstromLeave a commentEdit
1952 CIA Memo: “The aim is controlling an individual to the point where he will do our bidding against his will and even against such fundamental laws of nature as self-preservation.”
“This is all a plot. There are more “sons” out there. God help the world.” David Berkowitz (aka Son of (Uncle) Sam)
Contents:
I. Webmaster’s Introduction/Quasi-quantitative Equation-Description of the GEEEETTTTMO (Gangstalking Electronic-Experimentation, Enslavement, Execution, Targeting, Terrorism, Transhumanism & Torture-Murder Operations) civilian targeting system
II. Epigraph Quotes from Lookoutfa Charlie’s WEAPONIZED RF / ELF – “WHO’S DOING THIS?” video (Oct. 9, 2022)
IIIA. WHAT Is the Weaponized RF Surveillance System?: “C’MON..DO CRIMINAL STUFF” – 21ST CENTURY SURVEILLANCE – ITS WEAPONIZATION AND SUBVERSION (Lookoutfa Charlie, March 2022)
Partial Transcription
Comments
IIIB. WHAT Is the Weaponized RF Surveillance System?: OPEN AIR GUANTANAMO – RF TARGETING – V2K – ELECTRONIC TARGETING & Biderman’s “Chart of Coercion” “The RF Targeting-No-Touch Torture Playbook” (Lookoutfa Charlie video, 2 years ago)
Partial Transcription
Comments
IV. WHO Is Doing the Targeting? WEAPONIZED RF / ELF – “WHO’S DOING THIS?” (Oct. 9, 2022)
Partial Transcription
Comments
V. “WHY ARE THEY DOING THIS?” – WEAPONIZED RF / ELF (Oct. 28, 2022)
Partial Transcription
Comments
VI. HOW Are They Doing This? SMOKE SHOP VIDEO SHOWS MASS SURVEILLANCE WEAPON IN USE – NO ONE NOTICES – 2-WAY ELF COMMUNICATION
Partial Transcription
Comments
I. Webmaster’s Introduction and Quasi-quantitative Equation-Description (per A+B+C = D) of “The Targeted Individual (TI) Program” (GEEEETTTTMO) (Nov. 5, 2022):
‘Organized stalking/electronic harassment’ program (GEEEETTTTMO or Gangstalking Electronic-Experimentation, Enslavement, Execution, Targeting, Terrorism, Transhumanism & Torture-Murder Operations) =
– CIA’s MKULTRA (1953-), MHCHAOS (1967-) & Phoenix Program (1968-) + FBI Cointelpro (1956-) +
– 9/11 and “Global War On Terrorism” (battlespace is everywhere, everyone is potential target) +
– DHS-FBI Fusion Centers issue secret “kill contracts” on “TIs” (as “terrorists”/”dissidents”) +
– TIs stripped of civil liberties and targeted via gangstalking and “nonlethal” EM weapons +
– Involuntary test subjects required for EU’s Human Brain Project and DARPA’s BRAIN INITIATIVE (Brain Research Through Advancing Innovative Neurotechnologies) (2013-) +
– “Whole of nation” needed to target TIs’ brains (says neuroweaponologist, Dr. James Giordano) +
– US Air Force’s ‘Chart of Coercion’ (no-touch torture used at Guantanamo Bay) used against TIs +
– Psychologists/cognitive researchers/POGs (Psyop Groups) “tailor” & “monitor” torture of TIs +
– EM Frequencies from satellites, power grid, cell towers carry voices and images to TIs’ brains +
– DoD hybrid warfare/unconventional warfare deployed against TIs
– military-grade directed energy and neuroweapons (cognitive warfare) deployed against TIs +
– NSA Global (Five+ Eyes) Spy Network’s SIGINT (signals intelligence) spies track, stalk TIs +
– DoD-CIA-FBI-DHS-NASA-NATO and other agencies’ “counterterrorism” spies track, stalk TIs +
– NSA/Mossad Promis/Prism/Palantir software, metadata, & supercomputers track, stalk, & whack TIs +
– Private sector spy/security agencies (Infragard, Blackcube, etc.) stalk, whack TIs +
– Civilian-military perps on-the-ground and online (cyberstalkers) harass, abuse, stalk TIs +
– SIGREDUX, police, first responders, & Neighborhood Watch vigilantes abuse, stalk TIs +
– psychological trauma and manipulation can result in TIs becoming mass shooters and “assets” +
– legal system and the press aid in cover up
= State-Sponsored Terrorism, Torture, & Mass Murder Of Innocent Civilians
= HIGHEST TREASON
II. Epigraph Quotes from Lookoutfa Charlie’s WEAPONIZED RF / ELF – “WHO’S DOING THIS?” video (Oct. 9, 2022):
The tactics being used on people since 2001 are directly related to Guantanamo Bay-style interrogation and torture tactics. They are the same tactics.
… And coincidentally, every villain from pop culture history has been affected by these weapons.
Who would do this (use RF weapons to turn normal civilians such as Myron May into mass shooters)? The same people that did James Holmes, Nicolas Cruz, Seung-Hui Cho, Aaron Alexis, Nathan Gale, Mark David Chapman, David Berkowitz, Steven Paddock, and the others, the same people that don’t want guns around anymore. “The ends justify the means,” they believe, just like 9/11.
…. For the past 5, 6, 7 years, Mark Zuckerberg (of Facebook) is telling people that the future of communication is telepathy and what this entails is reading your sub-vocal speech and being able to make a cell phone call basically from one person to another without a phone. This is the exact same thing as what (TIs) are experiencing. Basically, these people are being put through a cell phone call, an artificial telepathy phone call that they can’t hang up on.
Webmaster Summary: Herein, I have partly transcribed five insightful videos by Lookoutfa Charlie which purport to explain the “what,” “who,” “why,” and “how” of a weaponized radio frequency surveillance system which may form the technological basis of organized stalking-electronic torture/aka “the program.” Information in these videos and four related videos on “Biderman’s Chart of Coercion” suggest that modern “gangstalking” operations comprise an “open-air Guantanamo Bay” brainwashing-no-touch torture program that deploys surveillance, mind control, and torture techniques derived from the CIA’s MKULTRA and other government black projects, as described in Aaron and Melissa Dyke’s documentary, “The Minds of Men.”
Lookoutfa Charlie’s videos also provide a plausible description of “the technology” deployed and explains the objectives of this covert warfare system as well. The technologies explained in these videos can remotely sense, measure, and alter breathing patterns, stress levels, heart rate, brain activity, etc. and appear to be the basis for the “under-the-skin surveillance” now being rolled out globally in the World Economic Forum’s Great Reset.
Lookoutfa Charlie’s thesis is that “this technology runs 24/7 365, everywhere. It’s not a bunch of different things. It’s one thing.” While I find most of Charlie’s insights to be quite useful, I am not convinced that his audio analyses successfully expose “the Voice-To-Skull/synthetic telepathy voices” on the spectral audio clips he analyzes (see below) mainly because I can’t hear them on my laptop’s audio. However, his audio equipment could be far superior to mine.
Lookoutfa Charlie videos also do an excellent job of tracing the history of CIA-DoD mind-controlled Manchurian Candidate assassins over the past six decades, beginning with Beach Boy founder, Brian Wilson in 1965, and they connect these events with the technology with which “targets” are subject to V2K/synthetic telepathy today.
“The Minds of Men” documentary goes into greater detail about the development of these technologies. It relates the story of electronics engineer, Leonard Kille (aka “Thomas R”), who was psychologically destroyed in the 1960s by the CIA and their “spychiatrists,” Drs. Vernon Mark (Boston City Hospital) and Frank Ervin (UCLA), purportedly to cure his “violence in the brain.” Dr. Peter Breggin of the Center to Study Psychiatry investigated the Kille case and found Mark and Ervin’s psychiatric notes commanding attending nurses to “take away his pants.” Breggin proved that Kille had been subjected to brain implantation, electronic torture, psychological warfare, systematic abuse, and “cruel and unusual punishment” within Massachusetts General Hospital hospital and elsewhere. This case is also documented in Hearing “Voices”: The Hidden History of the CIA’s Electromagnetic Mind Control Experiments by Alex Constantine (1995).
Charlie also demonstrates that Dr. Albert D. Biderman’s “Chart of Coercion” (a 1956 US Air Force document) provides the basis not only of the covert psychological warfare and torture ops against TIs, but the Guantanamo Bay concentration camp itself.
This wholesale abrogation of the Hyppocratic Oath and weaponization/militarization of the medical and psychiatric professions has presaged an era of criminal medical conduct culminating in the mass murder of civilians under the auspices of the Covid plandemic/scamdemic. Furthermore, the UN-government “response” to the Covid plandemic/scamdemic, i.e., the “lockdowns,” are a perfect demonstration of, and 1-1 match with, the techniques outlined in Biderman’s “Chart of Coercion.”
Lockdowns vs Albert Biderman’s chart of coercion
(Wikipedia: In a 1973 report on torture, Amnesty International stated that Biderman’s Chart of Coercion contained the “universal tools of torture and coercion”.)
In sum, evidence presented in this post and on this website indicates that “organized stalking-electronic harassment” and the Covid “lockdowns” comprise state-sponsored terrorism and torture of civilians. This is why I now refer to “the program” as GEEETTTMO (for “Gangstalking-Electronic Experimentation, Enslavement, Extermination, Transhumanism, Terrorism, & Torture-Murder Operations”).
There can be no amnesty for the perpetrators of these crimes against humanity. They must be identified and prosecuted to the full extent of the law.
