Episode 9: Opening the Five Eyes: Deciphering Britain’s JTRIG – Suzie Dawson, Nov. 17, 2019
NSA Global Spy Network aka NSA Global Information Grid
Webmaster Comment: The document being referred to in this critical video discussion between Suzie Dawson and clinical psychologist, Lissa K. Johnson on Nov. 17, 2019 is:
Epigraph Quotes:
From “Behavioral Science Support For JTRIG’s (Joint Threat Research Intelligence Group) Effects and Online HUMINT Operations (Mandeep K. Dhami, PhD) 10 March, 2011
The Measurement of Operational Success:
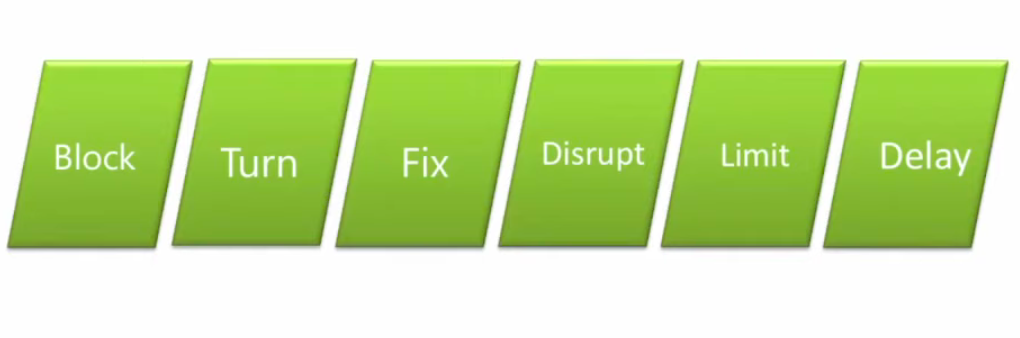
4.8 Measures of operational success should be directly or indirectly related to the specific aims of the operation (e.g., to “discredit,” promote “distrust”, “dissuade,” “deceive,” “disrupt,” “delay,” “deny,” “denigrate”/”degrade,” and “deter.”) (p. 24 of 42).
“To be a target, the most basic functions of living that everybody takes for granted, the use of the most basic services, becomes an emotional and financial liability to you. Because your engagement with those services presents an opportunity for harm to be done to you. And ultimately you start to exclude yourself from those spaces to save yourself that pain and headache.
… Anyone involved with you in any way, shape, or form will either also be smeared and also be targeted or will be pressured to take some action to break trust or break loyalty with you. Anybody who is involved with you will either get made an ally or they’ll be defaulted to being an enemy as well.
…. The top of the page is really key: “JTRIG (Joint Threat Research Intelligence Group) provides most of GCHQ’s cyber effects and online HUMINT capability.” That means that JTRIG is not just some minor component of the GCHQ (Britain’s NSA). That means that JTRIG extends across their targeting enterprise.
What I’ve seen is that the methods of the core players in what is known as the Global Network (aka NSA Global Spy Network) are replicated; the infrastructure, the human resources structures, even the funding structures. The architecture of the NSA is replicated across all the “partner agencies.” So without any shadow of a doubt, NSA obviously has their own version of JTRIG. All these intelligence agencies are homogenized. Right down to the same training. These online training sessions are open to all the “counterpart” intelligence agencies.
Suzie Dawson, TI, activist, researcher, former President of New Zealand’s Internet Party
This is the fourth session that we’re talking this through, but I still find it shocking that (reading) “social psychology (social cognition), attitudes, persuasive communications, interpersonal relationships, obedience, conformity, trust and distrust, psychological profiling” and all those (scholarly) literatures are being used to “deceive, discredit, disrupt, deny, degrade” and the fact that this is being used on domestic populations and activists for political reasons. (This is) really disturbing and alarming and horrifying. It’s deeply unethical for psychological research and knowledge to be used in this way.
.. .my professions’ tools are being used to abuse people and to attack very basic democratic rights and freedoms and humans rights, so it’s horrifying to me. As a therapist, you spend your career combating abuse not using psychological strategies to perpetrate it. This is antithetical to all psychological ethics and codes of professional practice. Instead of “do no harm,” this is all about doing harm.
… (Reading from 2011 JTRIG document) “Operation Targets could be specific individuals, groups, general populations, regimes.” So that’s a huge range of targets, from individuals to regimes.”
Lissa K. Johnson, clinical psychologist
“The Report on Thomson and Clark revealed seven government departments had engaged with a spy agency that acted unlawfully. It seems no one was safe from being spied on if they disagreed with government policy, and this should be a Watergate moment.
No on has been safe from unlawful spying in New Zealand over the past decade, and it’s all been supported by the state.”
Russell Norman, former New Zealand Cabinet Minister
Webmaster Introduction: “The Global Network” (aka “NSA Global Spy Network”) IS “the architecture of oppression” that rules and shapes the world. Drawing on her experience as a TI and a journalist-researcher, Suzie Dawson exposes this “architecture of oppression” in her 10-part series: “Opening the Five Eyes: Exposing the Spies.” The system is comprised of covert SIGINT (Signals Intelligence) and HUMINT (Human Intelligence) ops carried out by the NSA, CIA, DOD, FBI, DHS, and NATO, etc., in the US, the UK Ministry of Defense GCHQ, JTRIG, MI6, MI5, etc., in Britain, the IDF, Unit 8200, Mossad, Shin Bet, etc., in Israel, and their equivalents in over 100 other nations. Cooperating private security and intelligence contractors and their hired thugs (aka “surveillance role players,” “counterterrorism specialists”) execute street level operations and psychological attacks. The Global Network secretly surveilles, targets, and destroys honest, incorruptible activists, journalists, “dissidents,” scientists, truth-tellers, and innumerable others who have been secretly watchlisted and flagged as “potential terrorist threats” or considered “enemies of the state,” “enemy non-combatants,” “extremists,” “radicals,” or “persons of interest,” etc.
This horrific, reprehensible, and criminal “social engineering” system, aka “The National Security Racketeering Network,” is a “growth industry.” It is the largest black and black-market op AND “Crime Against Humanity” in human history. It radically ramped up after 9/11 and continues to expand across the globe today as a for-profit enterprise.
In episodes 6 through 9, Dawson and guests analyze documents from JTRIG (Joint Threat Response Intelligence Group), a part of GCHQ (Government Communications Headquarters; the British equivalent of the NSA) and expose the manuals, psychological tricks, methodologies, and protocols deployed in these nefarious operations. My opinion is that these psychological warfare techniques derive mainly from government-military-intelligence agencies’ weaponization of psychology and other sciences conducted by Britain’s Tavistock Institute (1921 onward) and the US governments’ Macy Conferences-CIA MKULTRA+ mind control programs (1947 onward).
The satanic nature of these programs cannot be dismissed. The Christian ethos of “love thy neighbor,” the very underpinning of Western Christian civilization, is hereby replaced by a comprehensive system of psychological abuse, trauma, and torture which, in effect, is the overt expression of “hate, degrade, deceive, and destroy thy neighbor.”
‘Cursed is anyone who attacks (kills, strikes, smites down, smites) a neighbor in secret.’ And all the people will reply, ‘Amen.’
Deuteronomy 27:24
I believe this curse now extends to the agencies, police units, businesses, nations, scientists, academics, populations, and individuals that participate in, financially support, and/or tacitly acquiesce to this (beyond) despicable torture-murder system. Apparently, hell is now expanding exponentially both in this world and the next.
Suzi 3D
Courageous Kiwi journalist Suzie Dawson and a special guest take us to school on the GCHQ’s (UK NSA) infamous JTRIG – Joint Threat Response Intelligence Group that smears, infiltrates and sabotages the lives of targets online!
The existence of JTRIG was revealed in the Snowden documents and a 50 slide set was published by The Intercept in 2013. This Sunday we break down each of those slides and decipher the methodology employed within.
Watch the full first episode here: https://www.pscp.tv/1vs5i/1djxXRzPRBLGZ
This is a #1vs5i campaign event. Donate to support Suzie’s fight for justice and accountability at: https://gogetfunding.com/help-a-kiwi-…
Spread the word:
Movement hashtag: #1vs5i
Official website: http://1vs5i.com/
Official Twitter: @1vs5i
Official Facebook: https://www.facebook.com/1vs5i
Short #1vs5i Promo Vid: https://youtu.be/0-IlSOrVaiM
MEDIA INQUIRIES: [email protected]
GENERAL INQUIRIES: [email protected]
Other Twitter accounts to follow: @Suzi3D
@HelpSuzi3D
Multistreaming with https://restream.io/
Webmaster’s Transcription of Video Highlights:
Suzie Dawson: Hi. I’m Suzie Dawson. I’m an activist, a journalist, and president of the Internet Party in New Zealand. Tonight is the 9th episode of my series: Opening the 5 Eyes: Exposing th Spies. This is the 4th episode in which clinical psychologist, Lissa K. Johnson, and I are examining documents from JTRIG (Joint Threat Response Intelligence Group) which is a part of Edward Snowden’s leaks. JTRIG is a sub-section of GCHQ (Government Communications General Headquarters), which is the United Kingdom’s equivalent of the NSA in America..
JTRIG is a military online digital unit that specializes in targeting activists or dissidents or people around the world with really comprehensive, nasty smear campaigns to infiltrate their lives and to sabotage them.
Please remember this is a promotional stream for the 1 vs. 5 Eye campaign to hold the intelligence agencies that have targeted me over the last 9 years to account and I have lawyers who are working with me to build a legal campaign to sue them. So we are fund raising. I would really appreciate you donating to this cause. At 1v5i.com/donate.
Thank you Lissa for coming back again. Please take it away.
Lissa K. Johnson: We got up to Strand 4: Disruption and Computer Network Attack, and you were previously talking about ways an online alias can befriend somebody by using the Maslow’s hierarchy of human needs to meet their needs. These green boxes seem to have to do with computer attacks:
Suzie: CNA (Computer Network Attack) is where they are actually penetrating your device. This is a pretty key part of all the other stuff that they do. The Signals Intelligence and Human Intelligence work together. JTRIG is about human intelligence; because you physically have a human operative who is inserting themselves into your life and meddling in it, which is what Human Intelligence is. To empower them to be able do that they need the Signals Intelligence.
This is where they are collecting data about you, from your devices, your communications, public data, commercial, police, government data and data obtained by hacking. CNA is the actual hacking. This is where they are getting information that should be illegal.
This is where they are attempting to block your digital actions. This has happened to me in many ways. This is a way to disrupt. I got very used to my digital publishing being disrupted in real time. So I started publishing in real time. I would type one sentence, publish, and then archive the page. And I had people mirror my work. I had to live blog my blogs to do it all. Otherwise, they’d delete it from existence before anybody saw it.
They coupled these operations with actual physical intrusions, break-ins, etc. You learn to adapt to find a way around it.
They stole a very popular domain from me to shut it down. Delay, disrupt, etc. They are trying to waste your time, slow you down. Sometimes my computer just shuts off when I’m using it. With articles and files removed. This is digital interference.
My phone would perform various activities- apparently on its own. They would remap my keyboard- so I couldn’t use it…. Just crazy, insane stuff. This would happen when I was texting. And my phone would radically overheat- so hot I couldn’t hold it. Meanwhile, it was being accessed by multiple parties in multiple locations.
Lissa: The operational playbook of disruption.
Some of these concepts about pulling groups apart. Causing groups to fracture does all this too.
Suzie: I would consider a ruse operation to be like the example I gave earlier of a group of saboteurs that infiltrated our group and created fake business cards, fake fliers, leading to false addresses, to re-route people away from the official channels.
Set piece operation: Not sure about that one. I could speculate.
Lissa: They talk about fake blog posts. Fake victim blog posts.
Suzie: In terms of the fake victims, they do things to you and then they accuse you of having done that to them.
Lissa: This is one of Machiavelli’s tactics. Russia-gate was that. Russia was accused of attacking America when it was the other way around.
False rescue is related to the false victim operation. There’s a role for an online alias to rescue someone who is posing as a victim.
Suzie: I think the false rescue is where they set you up in a situation and then they rescue you from it. It’s very conniving what these people do.
Disruption is multi-layered. Social disruption, disruption of your work. Sting operations I’ve got some tales about.
I had somebody who appeared to be another member of the Occupy movement and they came to me and said they were a hacker and had access to police data bases, and they gave me names and numbers of police supervisors who they said were targeting me. And they gave them to me and said I needed to publish them.
I found out after the fact that if I had published this stuff, I could have been arrested. So that was a sting operation. They would have been able to take me down.
Another example. They tried to convince me to get physically violent- I didn’t touch that one either. They want you to commit an illegal act. A third example in 2013, I got a message telling me that Kim Dotcom wanted to meet me at a motel that was close to the Prime Minister’s mansion. As soon as I saw the address I realized this was another sting.
A fourth one: They tried to get me to go out in the middle of the night to meet someone in the middle of nowhere by myself. I had a sixth sense it was an entrapment, a set up, a sting, a ruse. It wreaked.
A fifth one. Occupy around the world set up their own newspapers around the world. I learned from the mishaps from other Occupy groups. Look at how others are taken down and learn some great lessons.
One we fell for was when a group gave us some quotes from Adolf Hitler to get us to use them. They had cherry-picked these reasonable sounding statements from Hitler’s writing. Then when we publish it they out us for quoting Hitler’s work.
So we learned to really vet anything that is sent to us.
Lissa: So be really careful. Fact check.
Suzie: They’ll also do it just to pump your for information. One guy told me he was a web developer, who had a blog site. I really want to have a Skype meeting with you… As soon we do that, he starts hitting us with 20 questions. It was obvious, it was just a fishing exercise to profile us. So this was another ruse.
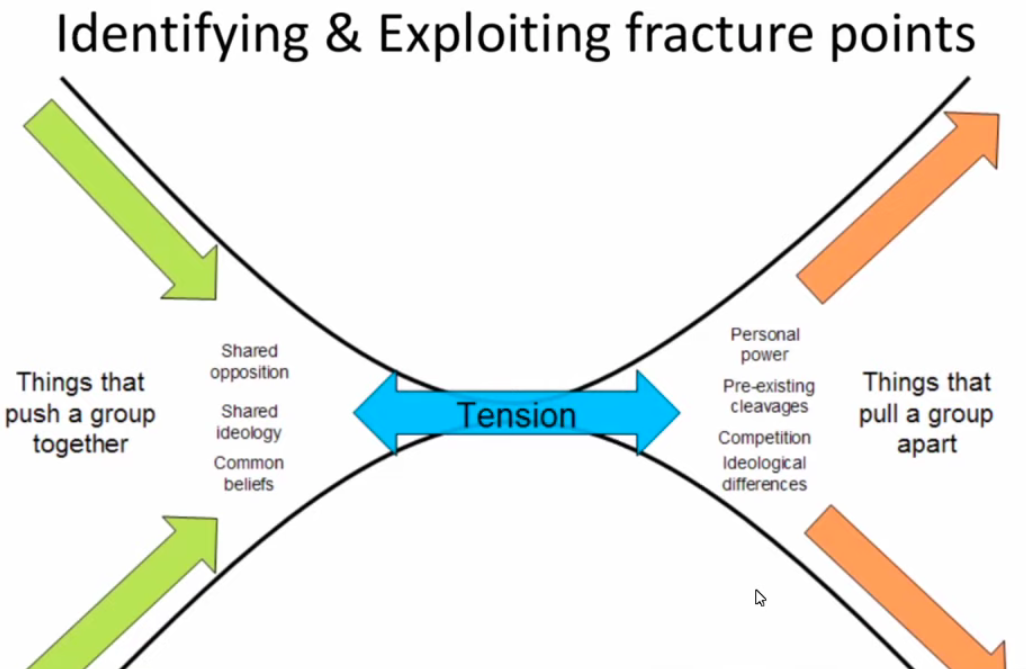
Lissa: This is one of the most easily exploitable aspect of being human. It’s easy to take a movement any movement and break it up into smaller groups. And that’s a very good way to reduce the effectiveness of any group. The more groups can be split along left-right, men-women, etc., the easier to fracture the group.
The factors that pull groups apart are useful for splintering.
Things that bring groups together (shared opposition, shared ideology, common beliefs), things that pull groups apart (personal power, ambition, ideological differences, pre-existing cleavages, competition).
It’s really easy to pit small groups against each other and prevent the efficacy of people working together. All you have to do is accentuate differences, cast the groups as working against each others’ needs and people will really go to war with each other. Even over small differences. We are really wired to go into combat with what we perceive as out-groups that have a different agenda to us. Long-term vs. newcomers, people vs. lawyers, different levels of leadership in groups, competition, all of these get manipulated).
Suzie: I think this is the single most important slide that has ever been published in relation to group dynamics and activism and the way that they are disrupted by intelligence agencies.
The things that push a group together are the enemy to the intelligence agencies. These are the things they want to destroy. Ideological differences is the number one factor…
They go after people one by one; they go after the opportunists and lure them away from the group… They create division and divide. These are the ones that want to hold positions of power and are enticed by opportunities that will increase their personal power.
Pre-existing cleavages are usually personality conflicts. They will exploit any naturally occurring dissension. You see this a lot in Wikileaks. Anything that smells like drama attracts these operatives like flies. They will try to create dramas and will gravitate toward pre-existing dramas. They will try to amplify and exaggerate it and feed the flames of any feuding.
In terms of ideological differences, this is the easiest way they can fracture groups. It can be the feminists vs. the radical feminists. They can tun the left against the far left, they can take degrees of it. They don’t need there to be a big difference they just need a difference.
In “Unity For J” (Julian), we set up from the very foundation of the group that any ideological difference and personal politics of members was irrelevant to us. All personal politics were to be left at the door. The only things that matter was if people supported the core values of the group. We enforced this severely. What that meant was that they had to try to pull the group apart on ideological lines from outside the movement. It was fascinating to see. Always, I’d seen these fissures created from within a movement. This time they came from the outside. This had the effect of: 1) actually galvanizing everybody on the inside.
This really showed that this tiny minority of fringe people outside the movement had a problem. AND 2) we didn’t splinter.
Incredible pressure was applied to the leaders of the group. They were inundated to get them break with us on ideological grounds. But not one of the 90 participants bowed to that pressure and broke ranks.
I think that because this movement was in support of Julian and Assange and Wikileaks, this played in our favor. We already expected saboteurs and dirty tricks. Another part was we got our messaging right. It was on the website. .. It was discussed. Tight, consistent messaging based on unity meant that ideological grounds could not be used to fracture us.
Lissa: You blocked off ideological differences as a mechanism to splinter the group. In “social identity theory,” psychologists talk about this in terms of “in-groups” and “out-groups” – we are all vulnerable to this stuff. We are all wired to get our sense of who we are by our group identifications. Be aware of which groups you strongly identify with.
One psychological antidote is to be conscious of where you are directing your energy and attention. Is the fight you fighting at the moment- is it any way delaying or blocking the progress of the movement as a whole. Keep your goal in mind. Is it a small group. Are you psychologically aligning yourself with the larger movement.
Suzie: In terms of competition and personal power, I was constantly told that Suzie has too much power. In reality, I distributed all the power in “Unity For J” from the outset.
Whenever you get centralization of an organization that’s when you get the most vulnerable to being targeted by these techniques. So de-centralize power is the lesson. Everybody had their own specialization. We had something very close to a day-to-day horizontal structure. Occupy had working groups- 25 in all. And the most anyone could be part of was 2. This worked very well at the beginning.
The trolls and nay-sayers would still keep spreading the standard smear stuff anyway.
In “Unity for J,” we were never trying to be monolith. We always wanted to inspire other groups to join us. “Action for Assange” is a great example. We need there to be Free Assange groups all over the world and we need them to be de-centralized. This changed the culture of the support groups for Julian Assange. It brought high profile voices together in the post-2016 environment.
Social pressure is a terrible tool for preventing people from expressing solidarity.
Lissa: De-centralization uses the natural tendency of people to form into small groups. The issue of being ostracized from a group- people will usually go to great lengths not to be ostracized from groups. Even a trivial ostracism can have a huge impact.
Suzie: The wider result was that we showed we could work with and achieve things by working with people who don’t believe what we believe. Many of the fantastic people in the group- I completely disagreed with them on many issues. That was a revolutionary aspect of Unity for J.
Sometimes the intel agencies will put people in the position where they had to either choose their career or their support for Julian. Or their ideology or their support for Julian. This was a deliberate enterprise- a very calculated move.
These slides are talking about the exploitation of trauma.
The exploiters of this are the military-industrial complex- who are the greatest perpetrators and perpetuators of rape and sexual assault- the largest numbers of which occur during war.
Social pressure comes into play. Next slide:
Lissa: The slide says their goals in 2011 were: “Full roll-out complete by early in 2013 with 150+ JTRIG and GCHQ Ops staffers fully trained.”
(Webmaster comment: Interestingly, my aggressive and destructive targeting began in Crestone, Colorado, in 2013).
“Mainstreaming work to level 1 tradecraft to 500 GCHQ analysts- relentlessly optimize training and tradecraft”…
So who knows what other training sessions they’ve had.
Suzie: I can say that this means they intended to have all their GCHQ analysts trained in this program. I can guarantee that this program would also roll out across all the 5 Eyes. So with Level 1 tradecraft, there would thousands if not 10s of thousands of agents trained in that ultimately.
And that ties in with the CIA’s Denial and Deception awards to NSA staffers that are awarded to NSA staff members for provably engaging in denial and deception activities against targets. They get a certificate and a bonus.
Lissa: There is also the GCHQ Initiative, the Joint Cyber Command, they are saying will be an online SAS with ever increasing numbers of operatives being trained in these tactics. Apparently led by one of Britain’s top female spies. It’s soon to be launched. So we can expect more of this and more sophisticated versions of this will be happening. That’s it, that’s the end.
Suzie: We’ve reached the end of the slides. Really?…. Conjuring with Information; and we’re not allowed to know who their name is.
Lissa: The idea of the magician.
Suzie: So let’s see this document.
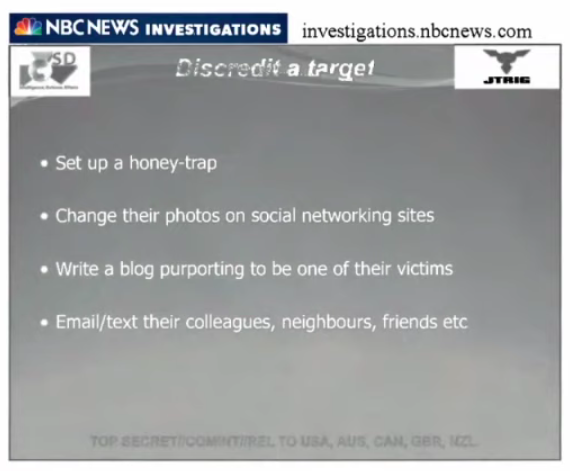
Lissa: So we were talking about the various operations they use in which they draw on all these psychological tactics. This is another group of JTRIG slides (2012) called “The Art of the Possible.” The other earlier JTRIG slide group was “the Art of Deception: (2011).
Suzie: Oh my God, this is textbook.
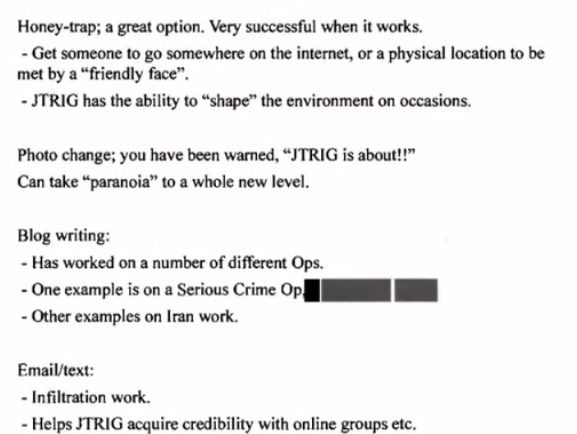
Lissa: This is about how to discredit a person. Set up a honey trap. They describe it as “a great option. Very successful when it works.” Luring someone into a fake intimate relationship. “JTRIG has the ability to shape the environment on occasion.” Perhaps by liaising with on the ground police forces.
Suzie: I can shed light on the “shaping the environment.” In the Snowden files, there are multiple files where the analyst expressed they need to have the same digital experience as the target. That means they read what the target reads, etc. Previously, they access to pieces of the target’s environment
Previously, they had said what they want to do is recreate the target’s environment. Once they can do they can begin to seed things into that environment and to influence what the target sees. What information they are fed, articles they are sent, etc.
They are trying to recreate, experience and then manipulate all the (digital) environment of the target.
Suzie: I saw a documentary about a Chinese activist living in America. She talked about her experiences of being targeted as an activist- and she was talking about all the JTRIG stuff. She had fake victim, she had electronic interference. Was it really the Chinese doing this stuff? Or maybe they targeted her in order to make her feel unsafe in China so she would go to America.
This other woman activist in New Zealand was being targeted, not by the Chinese, but by these New Zealand security agencies. She got the whole treatment and thought it was the Chinese. So often they lead you to believe that the ones targeting you are other than who really is targeting you.
They are obsessed with covering their tracks and fooling their targets into believing some other group is targeting them.
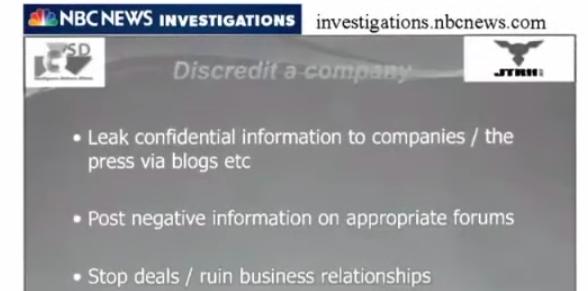
Lissa: Here they talk about discrediting a company. Leaking confidential information…
Suzie: This happened in 2014. There was a constant stream of leaks of internal Internet Party documents to the mainstream media. In 2017, our tech manager, Joe Booth, discovered there was a back door in the Internet Party email server that was carbon copying all the email lists to a security company in Wellington (NZ). That’s where espionage activities are laundered into the press and falsely attributed and falsely sourcing to the target and not to the people targeting them.
Lissa: In one of the documents, they talk about fake book chapters with the target as the author.
Suzie: In New Zealand, I web-searched my own name. And all of a sudden there is some porn star named Suzie Dawson. People just assume it’s the same Suzie Dawson.
It’s quite literally fake content that can be attributed to you.
Lissa: They talk about Iran and the Taliban as well.
Suzie: “Stop and divert the flow of funding.” There was massive interference with our Internet Party finances once I became president. Deal after deal fell through and we were deprived of any ability to finance the campaign. it was complex the way they handled Occupy Auckland funds. They started planting mainstream media articles about all the money we were receiving… the message to the public was that we had lots of money- and at the same time, they were bleeding our accounts.
And this is exactly what has been done to me. There have been reports that I have lots of money- just as I’m trying to fund the legal team… And there has been great interference with my bank accounts. It has cost my net worth up until the time I became an activist.
Lissa: So it combines smear and discreditation to help disrupt finances.
Suzie: And you’ll see the same thing with Wikileaks. Paypal literally kept all the funds in my account and didn’t return them to the donors.
Lissa: This is a 42-page document written by a psychologist. I believe this led to the slides we’ve been talking through. It talks about a lot of the psychological terms that we’ve just been through. And it talks more broadly about how those strategies are used in JTRIG operations. There’s even a survey of JTRIG staff to see how they feel about using these strategies.
They really corroborate what you’ve been talking about Suzie. Here it is in writing. I’ve highlighted a few bits.
“All of JTRIGs operations are conducted using cyber technology.” Staff described a range of methods and techniques for conducting “effects operations.” Uploading Youtube videos containing persuasive communications… to pass along misinformation to discredit, delay, deter, disrupt, etc. Setting up Facebook groups that encourage discussion on a topic- to promote distrust.
Suzie: For example, @wlswampcleaner is a twitter account that exists for no other reason than to monitor supporters’ discussions about Wikileaks and troll the hell out of them. At wlforum and associated blog site it has hundreds of articles attempting to discredit Wikileaks.
Obviously, it’s one thing if someone writes one critical tweet about somebody. It’s another thing to have someone spend 40 hours a week discrediting one or two websites, etc. These people are doing full-time discrediting operations. That is unjustifiable behavior.
Lissa: In a smaller way, there is an activist group, and then a smaller group appears with a similar name, and starts doing and sharing things that disrupt the first group, etc.
Suzie: Elizabeth Mueller and I had a situation where a guy made a documentary… actually, it was just video footage we had taken… I actually watched it. And he actually he had me talking and then it would merge into Donald Trump and then I appear again. So it was an attempt to apply political messaging to my non-political messaging and then have me send it out through my accounts.
Lissa: In one of the other slides they talked about using multiple senses. Sound and visuals. Establishing other aliases.
Suzie: This is exactly what you see. They are constantly cross-posting and cross-referencing each other to reinforce each other- and they are engaging only with each other in a group. But the focus of the all the conversation is to smear a single target.
Lissa: It’s really hard to know who is a real person and who isn’t. I don’t even try. I just think, does this help the cause or not?
Suzie: The proof is in the pudding. They create these groups of aliases and attempt to suck gullible people into the vortex. If they succeed, they revolve around that person So the focus shifts from the alias group as the core to the alias group supporting the real individual. You can literally see the massaging going on. There is a real grooming process that is quite openly done.
Lissa: Which is one of the psychological strategies we have talked about. A. Establish a credible online alias. B. Drawing other people into it by establishing the relationships.
Suzie: The theme about it is always about chipping away at the group.
Lissa: And fracturing the group. Sending spoof emails from a fake person or mimicking a real person. I’ve heard about that happening. Providing spoof online.
Suzie: People will send me a DM and I will never see it. A month later I will see the DM- one way or another, my account is being accessed.
And your emails disappear or you don’t hear from someone who actually emailed you. This is sabotage of your personal relationships. This can have a real impact on your relationships.
I invited very significant person to do something very key in support of Julian this year, and they never got back to me. Then I received an email from them 3 months later saying absolutely, yes, count me in. I was saying, “WHAT?” By that time we had given up hope of them doing it.
Lissa: Reading on: “Setting up spoof trade sites or sellers that might take a customers money or send customers degraded or spoof products.”
Suzie: AHHH! Elizabeth Mueller (in Virginia) and I (New Zealand) were having this same parallel problem at the same time, although we didn’t even know each other at the time. In New Zealand, I listed something for sale on Trade-Me. Instantly, they’d be purchased. Then the purchaser give me absolutely hell on earth, would show up my house, would be openly abusive, horrible, claiming I had ripped them off, just a nightmare, and then left terrible feedback about me on my Trade-Me page. But this happened so consistently to the point where I felt I couldn’t use the service anymore. It was so clearly being used as an “in,” as a way to get into my physical space and to create problems for me and upset me.
Unbeknownst to me the same time, Elizabeth was having the same problem on Ebay. She would order goods, they would be defective every time. She would have to go through the returns process every time. She would have people purchase things from her and show up at her house and be abusive and make problems for her and leave negative feedback. Same thing.
These are the types of things that people don’t understand about what it means to be a target.
To be a target, the most basic functions of living that everybody takes for granted, the use of the most basic services, becomes an emotional and financial liability to you. Because your employment of those services or your engagement with them presents an opportunity for harm to be done to you. And ultimately you start to exclude yourself from those spaces to save yourself that pain and headache.
Back to reading page: Contacting host websites and asking them to remove material.
(Webmaster Comment: After I posted material that supposed TI, Dr. Millicent Black, had sent me, she asked me to remove it.)
A lot of this stuff seems to tie in with CNA methods. One of the things they love to do.
Anyone that you that you associate as being involved with you in any way shape or form will either also be smeared and also be targeted or will be pressured to take some action to break trust or break loyalty with you. (For example), they started smearing my accountant just because she was listed as my accountant on the website. Anyone you associate with will either get made an ally or they’ll be defaulted to being an enemy as well.
Lissa: Hmmm, yeah. The power of authority, the authority principle is that people will go along with a credible knowledgeable expert. People will find it believable on face value. Going to top of the March 2011, JTRIG online operations document:
Suzie: The top of the page is really key, where it says: “JTRIG provides most of GCHQ’s cyber effects and online HUMINT capability.” That means that JTRIG is not just some minor component of the GCHQ. That means that JTRIG extends across their targeting enterprise and it also ties into what we just learned before which was that they wanted 150+ JTRIG specialists but they wanted to train all 500 GCHQ analysts in it.
Based on the Snowden files, what I’ve seen is that the methods of the core players in what is known as the Global Network, are replicated; the infrastructure, the human resources structures, even the funding structures. The architecture of the NSA is replicated across all the partner agencies and that would include this stuff. So without any shadow of a doubt, GCSB (New Zealand’s version of the NSA) will have a JTRIG counterpart. And NSA obviously has their own version of JTRIG, etc., etc. All these intelligence agencies are homogenized. They end up being little replicas of each other around the world. Right down to the same training.
That’s one of the things you see always in the Snowden files. The Snowden are forever containing training notices and it will show the list of people being trained and it will be a whole slew of partner agencies from all around the world these online training sessions are open to multiple agencies. So I can guarantee you that JTRIG will be doing the same thing. They will be holding these open day training sessions and inviting their “counterparts” from around the world. Counterparts is the word they always use.
Lissa: In this paragraph they talk about how they support these operations with theories and principles of behavioral science and social psychology. Saying JTRIG’s work can be grounded in scientific theory and evidence from social psychology, etc.
Suzie: Chapter 2 will be really interesting because it’s based on actual interviews with JTRIG staff. In the Snowden files there was the same concept, there were interviews with NSA senior executives and that presented some of the most fascinating findings. Because they tend to give away a lot, because the people being interviewed try to impress with their knowledge and tend to regurgitate a lot of information. So you end up learning a lot from them. It will be very, very juicy.
Lissa: This is the fourth session that we’re talking this through, but I still find it shocking that (reading) “social psychology (social cognition), attitudes, persuasive communications, interpersonal relationships, obedience, conformity, obedience, trust and distrust, psychologoical profiling” and all those literatures are being used to do this. I mean they are constantly talking about “deceive, discredit, disrupt, deny, degrade” and the fact that this is being used on domestic populations and activists for political reasons. Even after four sessions of talking about it, it’s still really disturbing and alarming and horrifying. It’s deeply unethical for psychological research and knowledge to be used in this way.
Suzie: It makes perfect sense that that’s your reaction. But I had the opposite reaction. For me, reading this stuff was a big relief. If I had experienced this and not learned this, I would be in a constant state of confusion. I was be in a constant state of: was this real?, was this not real? But to see all this written down, I’m just like “YESSSSSS, this is what they are doing.” It was a signiicant source of mental relief to me to read this. Because I understand this business language. I understand this format. It makes perfect sense to me. It’s like they are putting all the puzzle pieces in place. In my real life experiences, I get this puzzle piece and I get that puzzle piece and there are always these big gaps and I’m always trying to fill in the gaps.
And then I see something like this and I say: “Thanks guys you’ve laid it all out.” Everything makes sense now.
Lissa: It’s crazy making if you are being abused. This is a way to compound the trauma.
Suzie: The big problem I had was how to explain these things to people. How to I explain to people that I left my bedroom and there was a pair of clean socks on my dresser and when I come home in the evening those socks are gone and there are a pair of dirty men’s socks and there are no men in the home. But what I can explain is this entire document where they explain…. They actually have an official term for these break-ins- “surrpetitious entry.”
So to me it’s like a great gift from God that these documents have been leaked. So I’m so grateful to the whistleblowers who provided it. It’s like being given your sanity. This is the “how to” book of the magic tricks. If you read the book, you lose the shock and awe of the magic tricks because you know how it’s done.
Lissa: And it’s my professions’ tools that are being used to abuse people and to attack very basic democratic rights and freedoms and humans rights, so it’s horrifying to me.
As a therapist, you spend our career combating abuse not using psychological strategies to perpetrate it. This is antithetical to all psychological ethics and codes of professional practice. Instead of “do no harm,” this is all about doing harm.
Suzie: How can a document like this talk about ethics and retain any credibility at all? Ethical disruption?
Lissa: There is a report called Still Targeting Dissent about FBI targeting civilian activists. It’s worth having a look at.
Suzie: Chapter 4 paragraph can be summarized as “How to Cover Our Asses.” They are obsessed with risk management and getting caught. First, it would show them up for what they are doing. And two, there is also a risk that people might be able to get some redress.
Lissa: Dstl is Defense Science Technology Laboratory. It’s part of the Ministry of Defense and it’s about using behavioral science in military operations. They talk about the OCEAN model of personality. This is all very relevant to what Cambridge Analytica is doing with behavioral micro-targeting and target audience analysis. It’s become so advanced since these documents were written.
SCL, the parent company for Cambridge Analytica, did this in a very advanced way using AI to run constant experimentation by using people’s digital footprint to asses their personality profiles.. And refining it and refining it and refining it. Working out who was most persuadable and just targeting those persuadable. In 2011 it looks like this wasn’t that advanced, and here we are in 2019 and it’s extremely advanced. 2016 was basically a mass online experiment in recommendation 3. Interestingly, SCL has done quite a few contracts with the British government, which Dstl obviously works for, and it speaks to that sharing you were talking about.
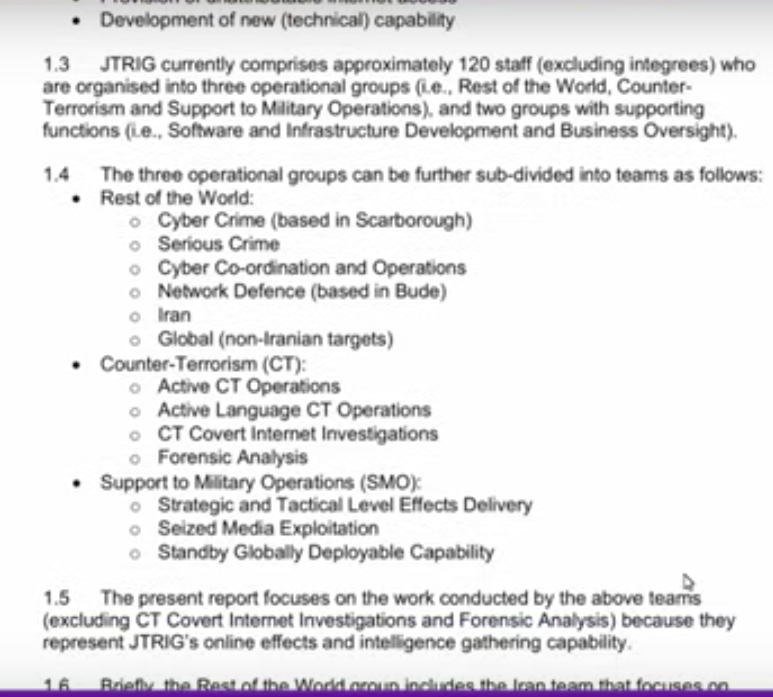
Page 5: This just talks about who they (the “cyber crime team”) are targeting. Targets…. overseas, and at home, the rest of the world group, counterterrorism group, a very broad range of targets, including “domestic extremists,” which relates to FBI targeting in the US. “The Cyber Co-ordination and Operations team works on individual websites and state cyber attacks.” So we have converging lines of evidence that this is used against activists, especially post-9/11, not just to target crime and violent terrorism over seas.
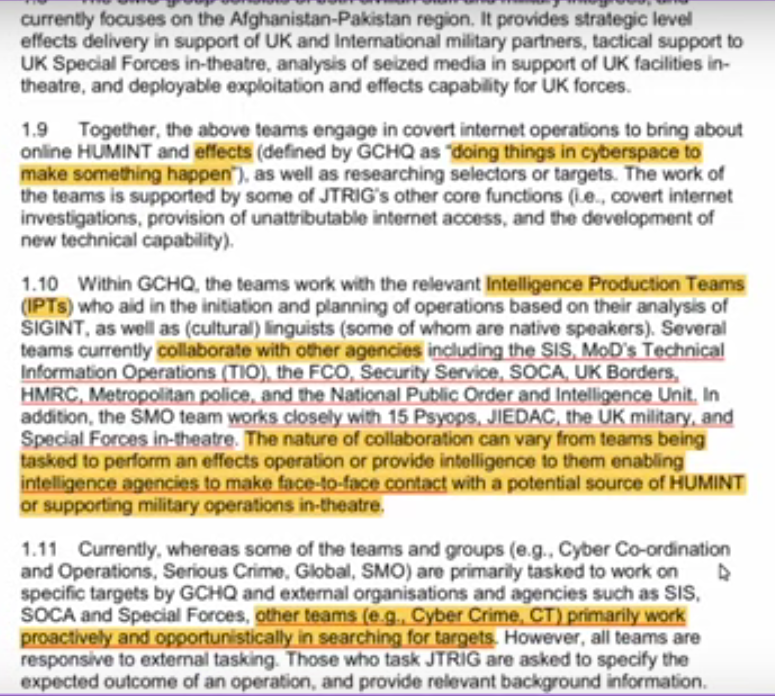
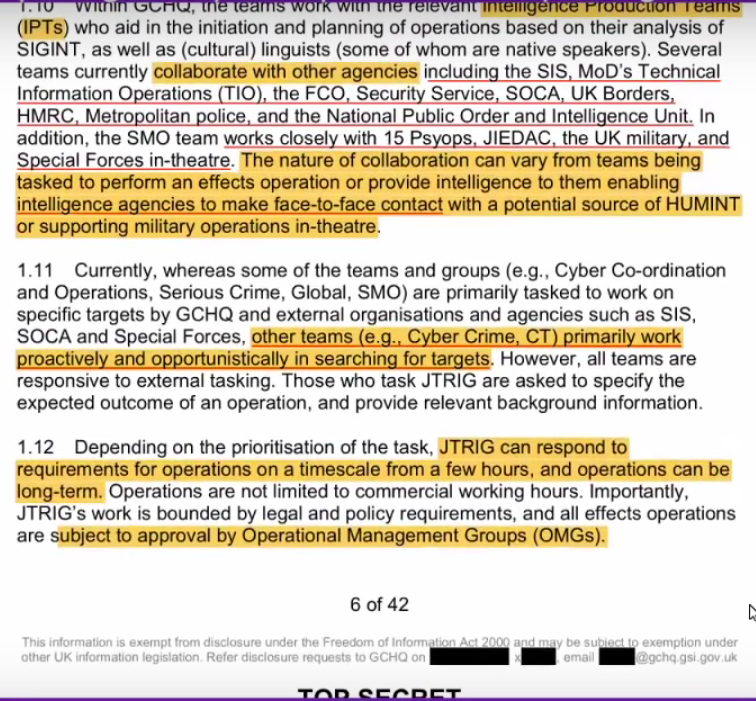
So their aim is to do things in cyber space to “make something happen.” They work with intelligence production teams, SIS, (which I understand is MI6), Ministry of Defense, technical information operations, borders, metropolitan police, National Public Intelligence Unit. Alo, SMO (support to military operations) team; works with 15 psyops teams, special forces in theater, to provide intelligence to them enabling Human Intelligence teams to better do their on-the-ground and face-to-face contact operations. So JTRIG, while it works with cyber operations, works with on-the-ground operatives suh as special operations forces (SOF).
“Whereas some teams and groups are primarily tasked to work on specific targets other groups work opportunistically to search for targets. They can work short-term (within a few hours) and long-term (days/weeks/months) operations.
This is the reference to the interviews with 22 staff.
Suzie: “Operations are not limited to commercial working hours.”
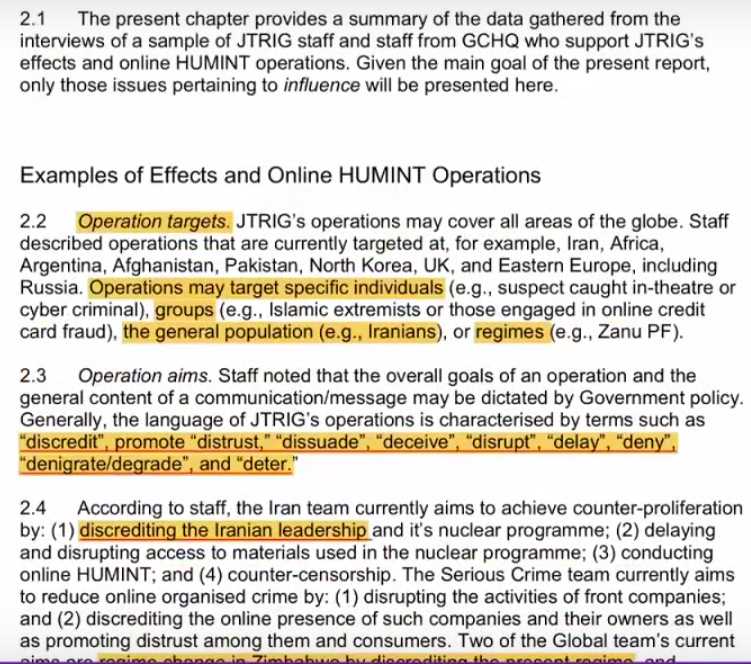
Lissa: It reads: “Operation Targets could be specific individuals, groups, general populations, or whole regimes.” So that’s a huge range of targets, individuals to regimes.”
Suzie: The constant references to credit card fraud and online financial whatever rings so many alarm bells for me for a number of reasons. Primarily because the anti-money laundering legislation is what empowers a lot of this activity. And the anti-money laundering teams that are set up in every single banking institution are the ones that have repeatedly been found to be supplying information to security agencies without a warrant or production orders and without any legal process. Specifically, the known cases against both Nicky Hagar and Martin Bradbury in New Zealand were proven to have been done under the guise of computer fraud.
And think about the CFAA, the Computer Fraud and Abuse Act, the legislation that keeps being used against the “hactivists” in America. That’s the cover they use and the legislation they are using to use these counterterrorism teams and resources against activists and journalists. They are bundling it into computer fraud.
Lissa: Just like activists are targeted under the mantle of national security since 9/11.
Suzie: Correct. Just like on one of these pages we target people who are terrorism and security threats. What is security? Every time they refer to computer fraud I know that is involved.
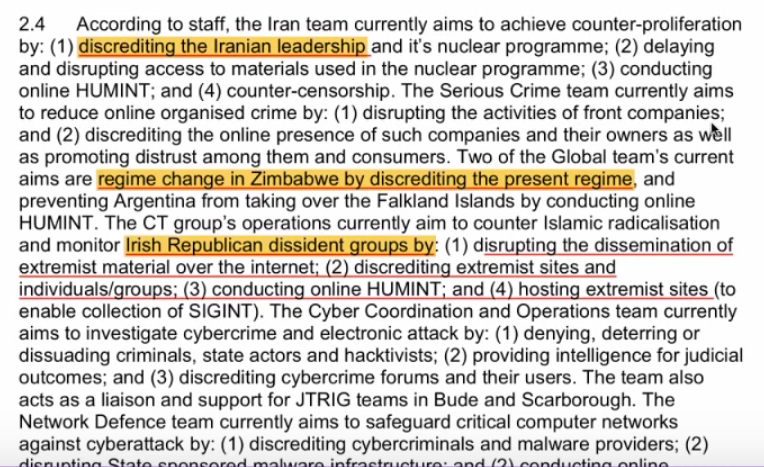
Lissa: It goes (these techniques) as high up to discredit a country’s leadership, such as Iran’s leadership. The techniques have been used in Zimbabwe, against Irish Republican dissident groups.
Suzie: The target has been “befriended” ….
interactions with target may be informed by analysis by SIGINT. That’s what I mean when I say they use the information they get about you from your online activities to do their Method of Entry or setups.
As far as tips for activists, you should never say, unless you are doing it fully aware for your own reasons, things like… if they do this then I’m going to do that. Or I’m scared that this will happen. It’s as good as making it happen. If you say, if they do X, they I will do Y, you are teaching them about your reactions.
Lissa: Better to not offer up too much information about your likes and dislikes in your online activities. All of this can be used in these ways too.
Suzie: This is a really difficult thing to teach because very few people can actually get to this level. But you can actually get to the point where you control the information you give them, so you creating reactions and outcomes you want. You do that by lying to and manipulating the matrix. By matrix I mean any digital space in which they are collecting and gathering data on you and acting on it. They want to control and understand your environment. You can go the other way with it. You can control this environment by consciously choosing what that data is going to be. You can actually take the power back. This would be the advanced activist self-protection course.
The most basic example: I would call my very savvy long-time activist friends in Occupy Auckland. And I’d say there’s no way I’m going to be able to make the demonstration on Saturday morning at 9:00 am. And they knew that meant that I would be there at 9:00 am. So it’s possible to lie to the matrix. Not in a malicious way. It’s doing it for self-protection.
Lissa:
Suzie: The only thing I can say is if the person who is perpetrating it is assessing what the risks are, what kind of oversight is going on? None. The first cost they mention is being discovered (as a GCHQ operation), another is that the target does not trust in them anymore, another is no longer being able to access the messages of the target.
The displacement is really, really, really interesting to me. They don’t want people moving out of their jurisdiction.
“Target changes or adapts to the tactic”- is another of their risk factors. So adaptablity is a risk factor. This is a very important list. This is a list of their fears. This is a list of what they are afraid of. So this gives us a priority list of things we want to achieve in order to protect ourselves.
“Unexpected adverse effects,” is something I see time an time again. This tends to be their undoing, time and time again. There’s always some real world thing that botches up their plans.
Lissa: Psychology is good at averages. But there’s a lot of variation around those averages. We’re not good at predicting things. There are too many variables. So it’s a very, very approximate science.
Suzie: And I love that under being discovered, they put (as a GCHQ operation). They don’t care if they can falsely attribute to the Russians or whatever.
Lissa: In 2.10, they’ve got solution to that, they produce a spoof alias as a fake fall guy.
Suzie: Which would be the shadow brokers. As in: “We are a shadowy group of hackers who just want bitcoin and here are all the NSA’s hacking tools.”
Lissa: These are just different ways to measure their effectiveness.
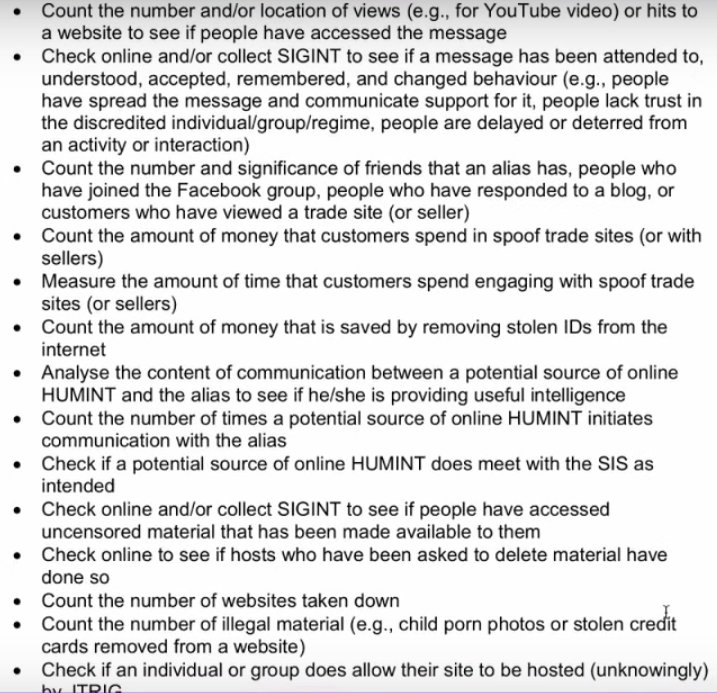
Suzie: It’s difficult to measure effectiveness. They say that in the first paragraph- 2.11. They have no metrics for what they are doing. Reads document. So much of this is so illegal. I think because their goal is so non-specific.
Degrade, deny, disrupt, deceive, and destroy are not very specific objectives.
A specific goal would be to cause X to do Y action. Instead their objective is to sew chaos and then how do you measure chaos? They default to digital statistics- count whatever you can count.
Lissa: External agencies such as MI6 may need to get involved in operations. Things that might threaten an operation: (2:13 and 2:14.) “Lack of continuity, maintaining an alias, difficulty communicating in a fashion representative of the demographics”….
Suzie: We’ve got to read this backward. Staff suggested that these are threats to their operation. Lack of continuity… maintaining an alias difficulty… We have to turn this around. If we are a target and we are trying to find out who is real and who is fake, these are things we can look for. Lack of photographs or visual images of their online aliases. Lack of time or staff to maintain their blogs and their aliases. “Difficulty in communicating in the social context-demographic of the alias.” But in my experience they are quite good at this.
Lack of continuity in maintaining an alias: These guys like holidays. They have fixed holidays, they have significant amounts holidays. These people don’t work 24/7. Their office is open 24/7. But they don’t work 24/7. And it is very, very, very difficult for them to have another employee step in and attempt to maintain a human intelligence relationship that they themselves have afforded. Because it only takes the target references one prior conversation or some prior thing or in-joke – that the newcomer agent can’t understand. It’s because it’s literally not the same person. That is one of the biggest red flags…. They might not be able to understand a past event… T
One of the consistent holes in these spy-cops and the online intelligence is that at the end of the day, they are going home to a wife and a family. They always have to have that away time. How do I explain that? Because the aliases are usually constructed in a way that is postured as being close in lifestyle to the target as possible.
(Webmaster Comment: This last statement might explain the extremely expensive, new Ram Promaster white panel van I recently observed parked in front of and then in the drive-way of the dilapidated house immediately behind mine in the very small community I live in in southern Baja, Mexico? (White solid panel Dodge Ram Promaster with California plates 68550S1 purchased at Don’s Auto Center, Fontana 829-1900; I’ve noticed spies and perps everywhere love to drive these panel white vans. They are well funded!!!!) The other cars at the residence are old w/ some on blocks. I had long ago “cessed” that house as a “safe house”/base of operations for my assailants. The Ram Promaster stayed at this residence for two to three weeks before disappearing.)
Suzie: But it’s impossible for that to be the reality when one is a spy and one is a genuine person. That’s the biggest give-away in my experience.
You think you are talking to one person, actually you are talking to 5, 6, 7, 8, 9, 10.
Lissa: So here are the backgrounds of people who do this sort of work for JTRIG: (reading) “IT, computing, politics, languages, law, maths, chemistry, sociology, journalism, publishing, police, and military/defense.” I’m glad to see they’re not psychologists actually.
Suzie: Laughs. Yeah, they reserve those spots for the torture programs (Guantanamo Bay, etc.).
Lissa: Many staff have worked in other areas of GCHQ before coming to JTRIG. Therefore, they’re not green.
Lissa: Staff said they had trained themselves on the ground or shadowed more experienced employees. It sounds like before these materials were put together people were just winging it without a formal psychological input.
Webmaster comment: This is not correct. The Tavistock Institute, which grew out of the Psychological Warfare Division of the British Army during World War I was always about using weaponized psychology to control and injure populations.)
Being the deceiver comes at a moral cost too that can be very traumatizing and destabilizing. There is a thing called moral injury, that occurs when people behave contrary to people to their moral compass. It’s a horrible thing to ask people to do these things. Looks like not everybody is comfortable with it.
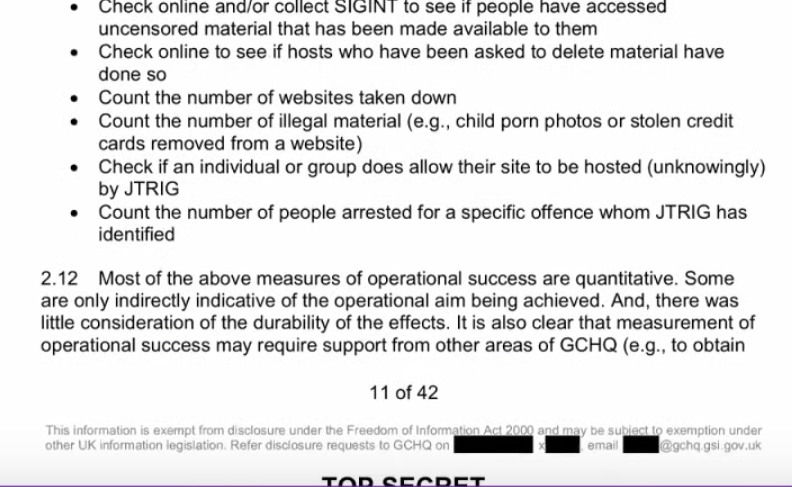
Suzie: I am not worried out JTRIG’s PTSD problems. These people should be in prison. Then they’ll have real PTSD problems. What is your position on the architects of this?
Lissa: When it was revealed that psychologists helped the CIA design their torture programs, members lobbied their professional bodies to alter codes of ethics to keep that from happening again. This is crying out for a a very serious investigation. Especially if it is clear it is being used against people for their politial views. It’s not just being used for national security and to keep us safe.
(Webmaster comment: Again, this comment shows that Lissa has no understanding of the extraordinary extent of these weaponized psychology programs over the past 100 + years.)
Suzie: And redress for victims. Acknowledgement.
Lissa: Yes. This document makes it very clear that this is a real thing. And victims need support services just like any other victims.
Suzie: There is not one single thing on these list that hasn’t been employed against Julian Assange.
Lissa: Yes, these tactics have been used against Jeremy Corbyn as well. Journalists smeared Jeremy Corbyn and Julian Assange. There are academics and scholars in Britain who have pushed back against the offical narrative on Syria have been smeared by these tactics as well. It’s kind of everywhere.
I found this stuff on the law to be interesting. So they have “legal advisors that ensure the operations comply with law.” If the operation doesn’t comply with UK law, then GCHQ and JTRIG need to obtain authorization from the Secretary of State.
Suzie: I want to point out that the torture program also had legal advisors. I would say that it’s not so much about whether they comply with the law, it’s whether the laws comply with them. And generally, where the laws don’t comply with them they introduce laws that will.
We also saw this in the Snowden files where they discovered that NSA officers were engaging in activities for which no NSA Executive Directive existed. They just went to the NSA Director, who issued retrospective dispensations/directives to the staff to cover the activities they had already engaged in. So once again, oversight exists only to cleanse the report.
Lissa: Going on: “With respect to international law,” determing if the operation complies with any applicable international law, and if it does, considering whether non-compliance would be acceptable to the Five Eyes Community.”
Suzie: Laughable
Lissa: Gobsmacking. Are we breaking international law… Yeah. Would the Five Eyes Be OK with it. Yeah.
JTRIG staff are provided mandatory legal training. But it is difficult to deal with ethical aspects. What they are doing is highly unethical, we should come up with our own code.
I highlighted propaganda techniques, it’s interesting to see what they consider key propaganda techniques. Humanitarian intervention v. bombing a country or a people.
An enormous amount of information is never reported.
Assertions without arguments.
Suzie: You see this all the time with the trolls. Julian Assange calls them “concerned trolls.”
Lissa: They are talking about preventing crime. This is the only healthy thing in these documents.
The risk assessment stuff, then
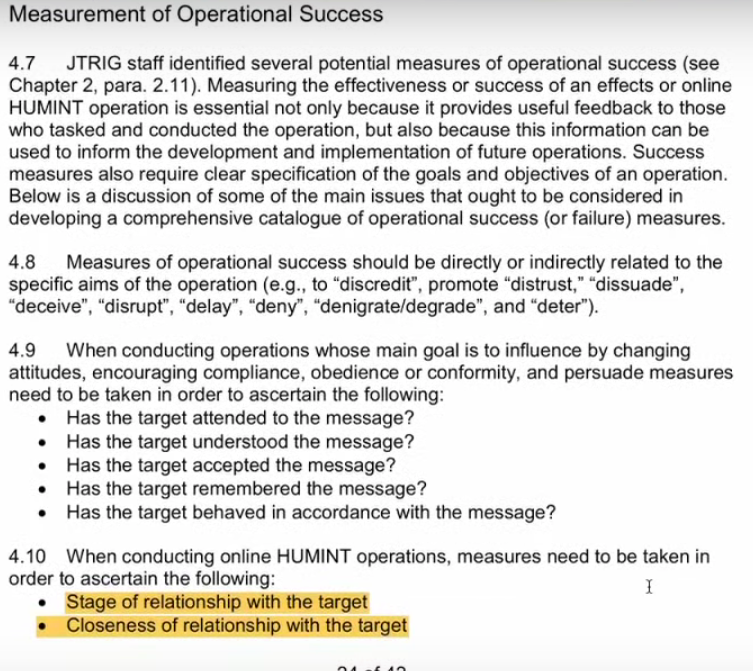
The measurement operational success.
4.8 Measures of operational success should be directly or indirectly related to the specific aims of the operation (e.g., to “discredit,” promote “distrust”, “dissuade,” “deceive,” “disrupt,” “delay,” “deny,” “denigrate”/”degrade,” and “deter.”)
Lissa: This speaks to the degree of the deception and exploitation and how deep it’s trying to go. It gets back to how unethical and horrifying this is.
Suzie: This has to do with what I said earlier about lying to the matrix. They hate being burned by targets. They hate being told a piece of information that turns out to be inaccurate. They hate that because it costs them in resources and time and money. What they want is targets that provide reliable information that can be acted on with surety. They can’t stand to take actions based on false information. Because it makes them looks like idiots and it costs them. That’s why one of the most powerful things you can is feed them bullshit. And it makes you less desirable as a target.
The matrix is the behemoth network of all the different programs, it’s the data vacuum. Lying to them is very powerful.
Lissa: This is going directly against the code of ethics of the British Society of Criminology.
This is all about exploiting psychological vulnerabilities. It’s all about invading private physical and cyber space.
Suzie: This section reads like a disclaimer.
Lissa: I think it’s saying they’ll come up with their own code of ethics.
Suzie: That falls in line with what NSA is doing.
So we can have Q&A now. And Lissa do you have any final thoughts?
Lissa: I learned a lot doing this. I was blissfully ignorant about all this before. It’s probably moved on a lot since 2011. And I feel like apologizing for my profession. This is a very critical time for activists. Basic democratic and legal rights are very much in danger now. It’s more important than ever that people stand up for these things.
It’s an important time not to be complacent. People who are very effective, like you, need to know these things. You said it made you even more open to large numbers of people.
JTRIG files are a manual. The manuals within the Snowden files have by and large been released in the first half year. The Signals Intelligence Directorate files were releases later. I studied thousands of these Snowden files. It was a full picture of the way NSA operated. It gave a very in depth insight into how the NSA operated. In 2004 files they talked about the development of drone warfare. In 2005, it was focuses on Iraq. Etc. As the geopolitics shifted year by year, the narratives shifted. So it gave a wholistic view of how the intelligence agencies operated.
For me, the tragedy in the Snowden files no longer being published is not that specific information is being withheld from the public is that chronological stepping through the evolution of the agencies is halted. It published between 2004 and 2009. I would like to know what is the 2010 to 2013 time frame. That’s why I’d like to see those files continue to be published.
The Snowden files gave us documents that never would have been released. The Snowden files contained information on specific targets, which Snowden didn’t intend to release. And Greenwald stated from the outset he never would release these. The manual and technical information was published almost immediately.
They had a team of 10 people working on the files. There were literally thousands of pages. They said it was a research issue. Anyone can read and study these files. Snowden did say he would publish the rest. Glen Greenwald has been putting his life on the line, doing some of the most epoch and geo-politically significant work in his career. He has been publishing other data bases. He’s lost friends and paid a high price. Glen is benefitting humanity on a great scale.
Someone asks if there is any effort to educate psychologists/psychiatrists about these things so that they can factor these issues into their diagnoses. To prevent misdiagnoses.
Lissa: As far as I know the answer is no.
Suzie: Ozwhistles says that the Snowden docs didn’t tell us anything we didn’t know. There were 10 million things in the Snowden documents that none of us knew. For instance, did you know that it was NSA that supplied the weapons of mass destruction evidence and bragged about it that was referenced by Colin Powell and George W. Bush in their speeches to the UN. So Ozwhistle is banned from this channel as a troll. This is a very ignoranct comment.
Pierre Omdiyar is a billionaire. Billionaires don’t become billionaires unless they are approved by the system. The system has many ways to neurtralize millionaires so they don’t become billionaires. Billionaires in some ways serve empire.
Glen Greenwald has become a target because of his advocacy for Julian Assange and Wikileaks. And he never talks about it. He has put his life on the line over and over.
At the end of the day, I trust people who are targets. I trust those who the empire wants to shut down and get rid of one way or another. And Glen Greenwald is one of those people. His achievements are inspite of the pervasive targeting of him. He has been kicked down so many times.
Reporter, Laura Poitras, also is a target. She was detained many times at borders. She has had to deal with all these JTRIG tactics. She, Glen, Julian, and I have all faced all these tactics. And Jacob Applebaum is a known NSA target. He was an FBI target too. Everything he ever did is required viewing. Also, go watch the Jake Applebaum and Laura Poitress interview where they studied the NSA drone kill lists from the Snowden files.
Whenever you see a big takedown of an activist, look at what they were doing just beforehand. Go look at Trevor Fitzgibbon was working on before they took him down. Look at what Julian was doing before they took him down in Sweden. Look at what I was doing before I was taken down in New Zealand. Look at my articles from that time period. And everything falls into place.
Trolls are all about easy narratives (lies) that people will eat up and never do the research on. They are into “one liners.”
People take what they see on twitter as being the real world. They don’t understand that smart people will not broadcast their lives on twitter.
20 Comments
tvSquareEyes.
1 year ago
Thank goodness for replays. Work commitments and dam missed u live again. Thankyou for all you do.
Peace Love & Happiness for Suzi.
.Aotearoa.
Angel Tibbs
1 year ago (edited)
Brilliant as usual. Yes I’m still sharing your vids.
Suggestion to download your YouTube vids to Bitchute, which you can do at the same time. No censorship peer to peer network.
Tanya Bauer
1 year ago
Hi Autumn great show lv to your family from Australia
S.F. S.
1 year ago
I sincerely appreciate these meetings, and look forward to them each week. As it did for Suzi, it actually relieved stress by validating these horrendous actions. However, I have one request? Could the broadcasts be kept to 2 hours and spread over a long period? It will take me weeks or months to build up financial interest among those I know, and I would love to look forward to at least 52 weeks of continued networking and information. I would hate to see 10-20 packed episodes and then nothing. Also, I teach a little on the side and it is impossible to keep a class engaged after 2 hours. Just an idea.
Suzie Greer
1 year ago
I don’t sleep well at night, I can’t sleep with the light out, I have no balance also so when it’s dark I fall over I can’t get up but that doesn’t usually happen I avoid that I like to trace my info and by telling the information to the right places I hope to get my information out but it falls on deaf ears I have had experiences like I’m sure you’re explaining right now that the intell do not want you to know about the intell have their own language that you can’t type on a usual keyboard this is a discovered language this is a language I’m totally lost with it doesn’t translate for me I don’t know how you can possibly find this on a regular keyboard so this is why I will stick to my guns and say this is their own keyboard language.
Gardener
6 days ago
Sorry I’m late!
Michelle Spiritual
1 year ago
I’ll add things here as I hear them. I’m still only 2 hours in.
Re your lawyer’s e-mails, why not just create a different account just for them & do NOT use gmail which isn’t encrypted anyway. There are many other better e-mail servers that also encrypt.
Are you saying that you don’t just whitelist the e-mails, but create a filter to NOT be sent to spam & they still get sent to spam?
I assume this is in gmail right?
If you haven’t done that, you need to create a filter (I can do a video for you if you want on how to do it), but again, I don’t recommend you use toxic gmail.
HTH
Jane
1 year ago
Hi Susie I reached out to you a while ago can you please get in contact with me thankyou
Barbara Guillette
1 year ago
Giordano and his 3A program on youtube
peace peach
1 year ago
Where can we read/access the paper?
ozwhistles
1 year ago
Suzi .. learn to recognize your allies? Look, I know you have deep PTSD, but going after me is like sawing off your own leg. We all have harm – and we are all trying to heal. Poking each other’s wounds does not help. I ask you to consider compassion? Otherwise – you wil get lumped-in with all the harm-makers. And I KNOW that is not your intention?
I could be wrong – but if you ARE a harm-maker? We do not need you.
Barbara Guillette
1 year ago
Use all info for self.?? Values?
Claudia Perry
1 year ago
Roger Stone another did nothing wrong WAnt to put hime in prison for life

































One Reply to “TIs: Meet Your Cyberstalkers: Deciphering UK’s JTRIG (Joint Threat Research Intelligence Group of GCHQ)- Suzie Dawson, Opening The Five-Eyes Series, Episode 9; Nov. 17, 2019); Source Docs & Video Transcription”
Comments are closed.