(Interview with Amy Holem begins at 22:55 minutes in video (top) and 17:58 in audio clip (bottom))
Epigraph Quotes from Interview:
“(Sadly, it is) mainly the US Army (that) is behind it. (And) all of these different forms of weapons systems.… They (US Government, DoD, UN, NATO) are selling this (technology) to pedophiles and human sex traffickers; they are actually using these operating systems for them. That’s how they make their money back. All we (TIs) are is a little product to them.
… It’s human experimentation. (It’s) them working on virtualization systems, artificial intelligence, Cloud services, their network systems, VOIT services, robotics, neural link technology, neural print technology, BCI (Brain-to-Computer Interface) technology, HCI (Human-Computer Interaction), augmented reality.
… The DoD and the FBI have a list of targeted individuals (TIs) and who has been implanted and not implanted. We all have an ID number. I’ve actually identified some of these ID numbers for the victims. They give this ID number to law enforcement programs that are state and government funded. They are using different types of programs like the CP3, (Center for Prevention Programs and Partnerships) which Biden just passed in 2021. So law enforcement officers are using this pre-crime program in order to stalk, harass, and sexually assault and rape the victims. They are using their different types of technologies that they are testing. Like firearm management systems, their automated license plate readers, their facial recognition systems. And they are using biometrics along with the fingerprinting and the ID and their automated fingerprint identification systems.
NASA has access to the satellite systems. Many residents of Florida and Texas are victims because they are where NASA is located…. The criminals receive catalogues of the TIs and get to pick and choose the victims they want to sexually assault. And they get linked out to the location where the person is at via satellite. So they are using these satellite systems and radio frequencies to transmit them globally around the world. NASA has specific programs they are using- like the neuralink technology- (in cooperation with) Elon Musk.
The Obama and the Biden crowd are the main human-child sex traffickers behind this.”
Aimee Holem, ex US Army Military Police, of Aimee’s Audio Subliminal Acoustic Fingerprinting L.L.C.
Webmaster comment: This interview provides some of the most comprehensive information I have heard about how “the technology” works and what groups are using it to traffic, target, torture, and destroy innocent civilians. The concept of “songs of the spine” is new to me and I cannot verify it independently. However, it is very well established in the literature that particular frequencies affect particular organs, moods, diseases, etc. What’s more, this explanation of “the technology” helps explain why Dave Case’s “anti-tinnitus” CD works so well for me!!!!!
Incidentally, if we add to the information provided herein that the pedophiles and human sex traffickers are primarily Jewish-Masonic-satanists who pay the military-industrial complex for these technological services, then I believe we have pieced together the essential elements of this massive “Manhattan Project Crime Against Humanity.”
I transcribe highlights to the interview below.
US Army Military Police Veteran Targeted With Direct Energy Weapons Fights Back To Help Others & Bring Justice To Perpetrators
Amy Holem is a US Army veteran who served as a military police officer. However, she became a target of direct energy weapons. Though she is indeed a victim of that targeting, she chose to educate herself through college to understand what was going on and now she uses her education to help others who have been targeted by our government and local law enforcement with these weapons. This is an incredibly fascinating interview that demands the People stand up and deal with the criminals in our midst acting in places of authority. Stay tuned, on Monday, we’re bringing Amy back on for part two with even more shocking information that demands a response.
See more here: sonsoflibertymedia.com/us-army-milit…rators-video/
How To Protect Yourself From 5G, EMF & RF Radiation: dq271.isrefer.com/go/pendant/AUL2472/
Subscribe on Rumble: rumble.com/user/sonsofliberrtyradiolive
Follow us on Gettr: gettr.com/user/sonsoflibertyra
Grab our feed on Locals: thesonsoflibertyradio.locals.com/
Join us on Telegram: t.me/sonsoflibertymedia
sonsoflibertyradio.com
sonsoflibertymedia.com
Sons of Liberty Store: thesonsofliberty.squarespace.com/
Support us through a donation: thesonsofliberty.squarespace.com/donate
Partner with us as a Son or Daughter of Liberty: thesonsofliberty.squarespace.com/membership/
Release date:
25 May 2022
Transcription of Interview Highlights by Webmaster:
Sons of Liberty moderator: Amy Holem, former US Army military police officer, owns Aimee’s Audios. She has a bachelors specializes in digital forensic analysis. And she is an advocate for victims of child and sex trafficking.
Amy: I was in the military for 3 years. I had two knee surgeries and got out of the military with an honorable discharge. It started in 2016 for me. I went to the VA Hospital because I was having trouble sleeping. I was only getting 4 hours sleep per day. And you need 8 hours. So I went in for a sleep study test. They put 100 little electrodes all over your body, your brain, they are registering your brain waves your sleeping patterns, your heart rate, your pulse. The hospital I went to is run by Dept. of Defense. Three months later I got a phone call from a lady saying she was interested in hiring hire me in my former business. At the end of the conversation she said, “I’m an FBI agent’s wife. I’m going to do a severe background check on you. And if I don’t like what I see, I’m going to make your life a living hell.”
About three months later, I was feeling really dizzy after eating dinner. I was sitting down and all of a sudden I had a seizure. I haven’t had a seizure since 4th or 5th grade. After that I noticed weird things happening to me; rocks were being thrown at my window in the middle of the night, I kept seeing shadows underneath my door. As a matter of fact, where I was living up in Wisconsin at that time, the Chief of Police was actually arrested for training his officers to harass civilians and falsely arrest them.
The way that I kind of uncovered it (all this), I was listening to my phone conversations and I could actually hear some noises in the background. Things that weren’t normal. And this is how I got into the audio analysis part of this with my company, “subliminal acoustic fingerprinting.” I tried to analyze them. I knew law enforcement wasn’t going to help me. So I came up with a special technique to actually listen to the subliminal communications that are embedded into the recording in the files. So then I tested it out on probably 200 victims and 100 non-victims just to verify what information I was collecting… I was testing it out on different kinds of devices from tablets, to Ipads, to computers, to applications systems, from USB pins to security camera systems. So I tested it out on multiple things to make sure that what I was capturing is in almost all the different victims’ (communications).
And the great thing about this technique is that this only happens to people who are being victimized.
I’m analyzing different videos and (inaudible)…. Anything that is being recorded or you can record with sound I can capture their communications. I get a lot of videos of different types of stalkers, it can verify if those people are involved or are not involves, people driving down the highway, different incidences, being followed, types of technologies from holograms, to projectors, to laser technology. So different victims have a different goal in mind. Some need this information for court cases that are pending. So every time I enter a report into court cases, the courts drop the cases on the victims. Which is a great thing. It means I’m in the right direction. They don’t want my reports to enter into the court system.
When my targeting began, I had just passed out with a seizure and I had an instant feeling in my body that all of a sudden I was no longer alone. It was an instant feeling within my body that like: “somebody’s here.” I sat up and immediately realized that someone else is here in this room without me even seeing them or knowing them. You gotta sometimes listen to your inner self.
Moderator: This is the V2K (Voice of God) technology that the US military used in the first Iraq war.
Amy: Yes. They use directional antenna systems that can beam the voices directly into…. using… going in from the cochlea to the vestibula system. They are using radio frequencies. They are using FM and AM band widths for transmission purposes. The criminals are actually using a mobile, virtual, operating network system. They can create their own different types of VOIT systems, their own phone services, their own telecommunications, their own frequency sets, and install them into their own platform system. Some even use Zoom conference calling for the targeting purposes. They have access to the person’s microphone and video components. They are hacking into people’s computer system using Pokemon scripts, which is actually a level 5 technician status, who owned the rights and the operations of those operating systems. So… Microsoft. You would have to be a Microsoft programmer in order to know the bios and the information within that computer system, whether it’s a Windows 10, Windows 11, Windows 7. Right now we’re at Windows 11.
Moderator: Is it possible you got an implant during your sleep study?
Amy: No. But when I’ve done audio analysis on other victims, I have some verbal confirmation that I do have implants within my body. The military could have implanted me without my knowledge during my two knee surgeries. The only thing that could get rid of implants is an electromagnetic pulse (EMP). Because of the different types of nanotechnology, the smart dust, the graphene within people’s bodies, even through the vaccination systems, it could only be killed with an EMP. You could detect it using an RFID scanner. Some of those can get pretty pricey. If I can get a system to open up the terminal system with the RFID scanner then I could shut down the chip that’s inside the body.
Moderator: Can you use a magnet to erase these chips? Can you clear that out.
Amy: Magnets do help, but all they do is cause interference. But you need a very, very powerful magnet, mainly because of the protection layers within the graphene, the hydrogel sensors within the body, some are so small that they could be pulled out through it, the magnet. But it’s hard to flush it out of your system with an absolute magnet.
When I learned about the audio and heard these communications in the background, I thought, I know I can do this. It only took me 5 days to figure out the technique. I read 5 books front to back and within 5 days I figured out the technique.
This (on the screen in the interview) is a spectrum review slide I sent you. This image uses a spectrum analyzer tool. When I do the audio analysis, I can actually pull out the different types of frequencies and identify them with the FCC ID and data base system.
SAF is my subliminal acoustic fingerprint technique. RAW is the original file I’m analyzing. So you can definitely see the differences between the images and the projections and the identifying numbers.
I have to identify all of these frequencies and carrier frequencies they are using. I have to check out their wavelength, their broadband, what kind of sub-carrier wave is, whether it’s an underground mine, a submarine channel. Identifying the frequencies is key because it aligns with the equipment they are using and that I’ve identified within the victim and the type of network system that is attacking the victim.
When you are dealing with the FCC (Federal Communications Commission) and you are finding these frequencies, a lot of companies and corporations only have a specific allocation for that specific frequency in that range. So, for example, Arizona Avionics has to do with military grade weapons systems and aeronautical engineering programs. It’s an EU-NATO radio communications center. So a lot of that correlates with the information that is being collected from victims in foreign countries, which is where you find the EU and NATO….
Or in the US, you are dealing with Northcom (US Northern Command, i.e., US, Canada and Mexico), and military, and the DoD. So different companies and corporations deal with specific parts of the technology and the equipment that is being used.
Moderator: Why is Belgium so involved with all this?
Amy: I’m involved with an ICATOR class action lawsuit (International Class Action Lawsuit Against Neuro Torture). There are about 150 victims from different countries that are involved in this lawsuit. I have helped over 3500 victims on a global scale. We have victims from Japan, China Australia, London, Ireland, Scotland, Austria, Germany, Belgium, Spain, Argentina, Canada, and the United States. The ICATOR lawsuit will prove that mind control technology, the BCI (Brain-Computer-Interface) technology, the Neuralink technology, and the 5G microwave weapons system are being used. This lawsuit is very important because Belgium is the headquarters for the EU-NATO and NIST, the National Institute of Standards of Technology. A lot of the connections between the child-human sex traffickers is actually through the Department of Defense and NATO. NATO is actually supplying the links to the weapons systems that are being used on the victims.
(Regarding the possible connections between the TI torture program and the Covid so-called “vaccinated”), doing this type of study with the victims I’ve worked with, I have captured information about Biotech, Lunatech, and Pfizer, all creating the data base system and manipulating the mRNA and DNA sequencing within the human body using different types of military projects like Genesis.
Moderator: The CDC has hundreds, thousands of pages on a “zombie apocalypse.” The media are prepping us for this. Where people are just not in control of themselves. It’s almost like they are taken over by somebody else. This sounds exactly like what you are talking about. Do you think that’s a possibility?
Amy: Oh, absolutely. In some of the videos I wanted to show you.. I’ll just describe it instead. (In the video) a beam of light going on to a victim’s head and then you see the victim raising her arms straight up into the air. Then as soon as the beam of light releases the head and shoots back into direction where it came from, the victim puts her hand down. They are remotely moving her body and manipulating her while she was sleeping.
Another one that I have… ah, this poor woman… it made me cry watching this and listening to the audio…. They were forcing the woman to move her head and go around in circles. They are like: Move your head to the left and she would jerk to the left, etc. And move your head to the right, and it would jerk to the right. They were literally forcing her body to make all these movements without her authorizations or permissions. So using the nanotechnology and how much is in your body system is basically how they are mapping you out with their weapons systems. So it can be centralized to your central nervous system through the brain stem and the spine. I don’t know if I sent you the “Songs of the Spine” photo?
It should be a vertebrae and it then it shows the different tones? The tone generators, each can manipulate portions of your body system through the central nervous system playing a specific tone or a note. Do you have the chart of the notes?
Moderator: (Changes the subject) We’ve got a lot of people in the chat saying you are brilliant, you know what you are talking about, you the real deal. Karen Stewart recommends you. You are legitimate. So by being part of the solution this is above and beyond any military service. As far as I’m concerned the military is going along with the tyrants and the criminals. Our Founding Fathers didn’t want a standing military.
Yeah. And that’s the sad part. Mainly the US army is actually behind it. (And) all of these different forms of weapons systems.
So… To go back to the IOT devices diagram. That shows the different types of ranges, from short range to long range communications. And what those IOT… Anyone who knows the Internet of things. Those are your Fitbits, your Bluetooth speakers, your Siri, or Latsa programs. Anything that collects data. It could be different RFID chips, IR sensors, Proximity sensors. So these IOT devices show the different types of communications. And when we are dealing with those different frequency ranges, usually through the spectrum analyzer and the FCC, that is where those communications fall into. And I could actually capture those different companies and corporations and find out if they are using a Zigby. If it is being transmitted this way. There’s more to audio analysis than you can possibly fathom. I go into depth with these reports from different types of equipment, aligning echo-links from Amazon up to matching it with the broadband system, and making sure it is coming from the satellite communications too. So it’s aligning it step-by-step for the victim and proving that it is the technology that is assaulting the victim.
This is the note chart. Basically with the tone generators… Using the directional antenna systems, they can be either omni-directional or directional… using tone generators, they play specific notes. It’s kind of like how a garage door opener works. So you hit the button on your garage door opener and it plays a tone. And then the tone reaches the receiver and then your garage door opens because the tone matches and the output is to open or close your garage door. It’s an IR sensor. So it’s basically the same thing with Neuralink technology. They play a tone, which is also a form of people’s tinnitus, the ringing in the ears, it’s a tone. A lot of people that have tinnitus don’t realize…. If the tone is changing pitches on you, chances are that you are a victim. If it is a straight, steady tone, constantly, that means you have permanent ear damage and it is actually tinnitus.
But when they change these notes and these pitches they actually affect different portions of the body. Like G here is actually neurotransmitters. This actually connects it to the brain of the victim. And if they want to go down. Like let’s say, pertosis of the eyes, rapid-eye movements within your eyes, they’d hit an A. And that would travel down your facial nerve system and then remotely access your eye and get your eye to twitch or move your eyebrows up and down and force your body. This is how they do forced speech as well, hitting specific portions of your brain.
I have the “songs of the spine” chart here.
(Webmaster: Here are other diagrams about the songs of the spine I find online.)
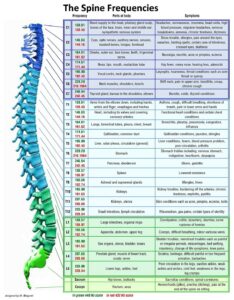
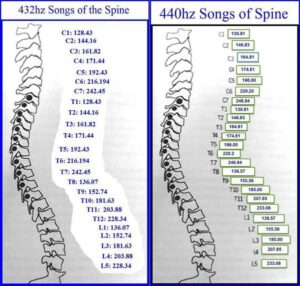
They are hitting your central nervous system through the cochlea and the vestibulae, it actually connects to your brain stem, which is at the base of your neck and it travels down the spine. The C-7 is actually your cervical, and then it goes in your thoracic, and then it goes into your lower lumbar system. So basically, when they are playing those notes, these are the different frequency ranges on there that they can play in order to hit specific areas. So if they want to make you sick and nauseous they would go to the 220 range. And that would hit directly into your stomach and this causes a lot of heart burn for people. It also creates nausea, vomiting, and it could force the person to actually go to the bathroom.
(Webmaster comment: This has happened to me dramatically a number of times.)
So the US government and UN and NATO are supplying this equipment to people who are child-human sex traffickers. They (government, DoD, UN, NATO) are selling this out to pedophiles and human sex traffickers; they are actually using these operating systems for them. That’s how they make their money back. All we are is a little product to them. So each one (trafficker) has different fetishes. Because of the video voyeurism attributes, they take videos and they also sell those videos of the victim. So if they have a fetish like a foot fetish, or going to the bathroom, or maybe they like larger women or things like that, everybody has their own different fetishes, they could hit specific parts of the body, including when they are actually going down to the lower lumbar, where they are hitting the L1 and L3. And that’s where they are allowed to actually sexually assault and rape males and females.
Moderator: (The late engineer and TI) Helena (Csorba) talked about this as well. She talked about them targeting all different parts of the body. She saw as some sort of diabolical sexual assault. They can make you defecate, urinate, and vomit on command. She said they can burn your body in certain places. They can put all sorts of pains in your body. It makes me wonder why they got rid with lead paint. Because I understand that’s actually helpful in cutting some of this off.
Amy: They did the lead paint thing because it blocks the RF signals along with the microwave weapons systems. In order to get lead paint out of the houses. They banned it. Who eats paint chips? And that’s their main reason for banning it. American people are not that stupid.>
When it comes to radio frequencies, it doesn’t stop the radio frequencies. Scalar waves have to do more with your personal energy and giving you a protective layer- as in positive vibes, a healing sensation. I did notice that LED lighting creates vertical humbars on the electronic device… this means it was distorting their signal. So the audio I have from that device really wasn’t that great because she used the LED to distort their signal so a lot of their communications were distorted and choppy. But you want to stay away with SMART LED lights because different companies can use those wit remote access that are part of SMART devices, your thermostat, smart meters, your 5G, appliances, etc. They are using the proximity fuses, which is created by the DoD and the Energy Efficiency Act, to access your refrigerator, washer and dryer systems, your microwaves, your ceiling fans, because now all of those new appliances have those chips and sensors built into them. They started putting these chips in the appliances about the year 2000. So late 1990s and down is very safe for you.
When you see your lights going on and off in your house someone is targeting you remotely.
(Webmaster: This happens to me regularly in my Crestone, Colorado home as well.)
How do I know that? I have captured this on multiple devices. They use remote data acquisition systems, which are actually used by police departments to track and locate. A lot of it has to do with RFID chips and the sensors that are built into those products. Do your LED lights change colors? Are they bluetooth compatible? If so, it is hackable. So when you use your router configurations. If you don’t know the MAC address for it, chances are it can be accessed easily by perpetrators and criminals.
Moderator: What have you actually experienced in all of this and why do you think it happened?
Amy: I don’t like talking about me. I really don’t investigate me. I investigate other people. My targeting has varied from the beginning, from doing the audio analysis to the present day. Now, I am being sexually assaulted every single night. Every time I write a report for the victim I’m basically being I’m being trampled and murdered. If you show those wounds of my legs and the measurements, I’m being attacked with 5 different weapons systems. This is one example of them.
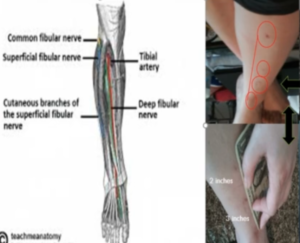
I use the dollar bill- that’s standard size for 6 inches. Each of them are basically 2 inches apart from each other. Those are laser weapons. Basically, they are burning my body and mutilating my whole entire body and basically what they are doing is they are mapping my body out like a grid system. Remember, I said they want to control and they were moving the woman’s arms up and down. Those are different types of laser weapons systems. I’m also being hit by solar energy from Legacy… by Solar Faith technology which belongs by the Clintons, from satellites. Solar Faith is a solar company that is dealing with solar technologies and satellite communications.
I’m also being attacked by Lumina, which is operated by (Governor) Jebidiah Bush. So I am being human sex trafficked out- sexually assaulted and raped every single night. And when I’m helping other victims, I get hit tenfold, because I get their perpetrators attacking me too. They don’t like me. Because I’ve captured their information, their names, locations, identities, their IP address systems, their servers. But also I know I have good guys when I’m analyzing my audio files… a lot of them are trying to block these systems…They block access. But some people are dead set on just torturing me through the NASA program, the space program. I’m in there as well. Which is why they are using the laser and solar technology systems on me. I get a lot of directed energy weapons using the ORIOLE, the Patriot system, and the Raytheir as well.
Moderator: Why do you think they are targeting you?
Amy: Me? I don’t think it matters. I don’t ask why because there is no reason why. These are evil people doing evil things to good people. The government can not hire good guys to attack people and practice their weapons systems on them. No good human being is going to do that to another. They are going to say this is wrong. That’s why they are hiring these child-human sex traffickers, these rapists and these pedophiles for their systems. Because they are the ones that are willing to attack innocent people so they can test it out. I’ve found cult information. Obviously, I keep saying child-human sex traffickers because I capture hundreds and thousands of audios in victims on them.
It’s not a matter of why? It’s human experimentation. (It’s) them working on virtualization systems, artificial intelligence, Cloud services, their network systems, VOIT services, robotics, neural link technology, neural print technology, BCI technology, HCI (Human-Computer Interaction), augmented reality. All of these systems are going together. So in my view, why I’m being attacked doesn’t matter. The fact is that I shouldn’t be attacked. I’m innocent.
The DoD and the FBI have a list of targeted individuals (TIs) and all the people who have been implanted and not implanted. (Karen Stewart talks about the Fusion Centers.) We all have an ID number. And I’ve actually identified some of these ID numbers for the victims. They give this ID number to law enforcement programs that are state and government funded. They are using different types of programs like the CP3, (Center for Prevention Programs and Partnerships) which Biden just passed in 2021. It’s a pre-crime program. So law enforcement officers are using this pre-crime program in order to stalk, harass, and sexually assault and rape the victims. They are using their different types of technologies that they are testing. Like firearm management systems, their automated license plate readers, their facial recognition systems, which are written by Facebook. And they are using biometrics along with the fingerprinting and the ID and their automated fingerprint identification systems. All these programs that are state and federally funded.
Along with the intelligence LED act. I’m down here in Florida. NASA has a lot of access to the satellite systems. NASA comes into play because they have all these connections. So NASA can ship them out from victim to victim. The criminals get to pick and choose their victims they want to sexually assault. And they get linked out to the location where the person is at. So they are using these satellite systems and radio frequencies to transmit them globally around the world. So when I say I’m part of NASA it’s because I’m down here in Florida. So NASA has specific programs they are using- like the neuralink technology- so like Elon Musk.
Residents of Florida and Texas are often victims because they are where NASA is located.
Moderator: What is the real solution? You are going to Belgium but we understand that Belgium is tied in the United Nations. So what’s your goal here? Is it to get this stuff shut down? You aren’t going to do it through the court systems because they are just as corrupt as the perpetrators. Is it to get the message out to the people? So that there is a hew and outcry?
Amy: A lot of it is bringing truth to it. To show evidence to the victims. The victims need solace and hope. My audio analyses provide that to them. My audios prove the communications and the attacks on these people’s bodies. So capturing these names gives them a chance to press criminal charges against the perpetrators and the names that I’ve collected, the different companies and organizations.
It is really hard within the United States because law enforcement is highly involved. They are running it through the back end operation systems. And they are giving all this information to the sex traffickers and the pedophiles. They are actually running traffic control and blocking and deleting license plate information and kid’s photos from their systems so they can properly human sex traffic them.
When it comes to helping the victims, I can provide audio analysis. I provide the FCC imaging, I can do thermal scan images, show the microwave frequencies, the microwave radiation on their body systems. I can pinpoint if they do have a chip and sensor, where a chip is located in their body, so they know how to get it removed.
In the US they are blocking us in every aspect. Law enforcement refuse to open up any cases. It’s a vicious circle. You go to the FBI. The FBI deny it. They won’t open up a case.
Then they say, “Oh, it’s out of our jurisdiction.” Or we don’t have that kind of equipment.” They are liars. Then you go higher, you go to your State’s attorney, your Governors, your Senators, and they say: “It sounds like a legal issue, you have to go to your local police.” All it is a vicious cycle and it keeps the victim going in a circle. And we never get anywhere.
The reason that Belgium (the ICATOR lawsuit) is so important is that we are allowed to press criminal charges against the US. Even here in the federal court system, I have a copy of the memo to refuse any and all cases, to never allow it into the court system, to falsely Baker Act the victim.
So we are up against a huge child-human sex trafficking ring and operations system. So getting this information out there and proving it is what the victims need.
I actually want to go to Belgium to present my evidence to the lawyer- I have over 27,000 domain and IP addresses of child and human sex traffickers. it will be a 3 year process. Right now we are in the process of writing a petition and we have to get the proper signatures.
EU and NATO are very important. They have a big pull with the UN. With the ICATOR lawsuit, I’m going to be working with Barry Trower, an MI5 agent who worked on these weapon systems. There’s a French lawyer named Jeanne who has won every single case on 5G.
Moderator: How do you see 5G working with this?
Amy: It’s completely tied to it… To your smart meters, to your electrical grid systems, they are controlling it with 3-way transmitters, your transformers, this is why the government and state funding are authorizing. They want to be able to remotely access your vehicles. They want self-driving cars. They want to get us to stop using our vehicles and going with electric cars. It’s easier to be controlled through the 5G weapons systems.
They want to do a mass mesh network system, Jeff Bezos is working on this, where all of our internet is going to be provided by a whole street, we’ll all connected to each other. So basically, they can hop from home to home to home and basically sexually assault and spy on anyone. (Yes,) it all started with Obama’s cash-for-clunkers program to get old cars out of circulation. Obama and the Biden crowd are the main child sex traffickers behind this.
