Dr. Eric Karlsrom Interview on Jeff Rense Program (Oct. 27, 2022):
Contents:
I. Quotes On Deep State Origin of PROMIS, PRISM, and PALANTIR
II. Bullet Point Summary of Contents
III. Headlines From Whitney Webb Aug. 26, 2022 Interview Related to Organized Stalking-Electronic Harassment
IV. Notes From Whitney Webb Interview: “One Nation Under Blackmail: The Enterprise, PROMIS and Casolaro feat,” Aug. 26, 2022
V. PROMIS (Prosecutors Management Information System): (From Wikipedia)
VI. NSA’s ESCHELON
VII. NSA’s PRISM Spying Program
VIII. What Is The NSA’s Prism Program (FAQ)
IX. NSA mass surveillance leaks: Timeline of events to date, by Zack Whittacker, Nov. 22, 2013, CNET
X. Pentagon’s Total Information Awareness (TIA)
XI. Palantir Technologies (From Wikipedia)
XII. How Palantir Conquered the World, The Corbett Report, Oct. 22, 2022
XIII. How A “Deviant” Philosopher Built Palantir- A CIA-Funded Data Mining Juggernaut, by Andy Greenberg and Ryan Mac, Sept. 1, 2013, Forbes
XIX. Does Palantir See Too Much? By Michael Steinberger, Oct. 29, 2020, New York Times
XV. How Peter Thiel’s Palantir Helped the NSA Spy on the Whole World: Documents provided by NSA whistleblower Edward Snowden reveal Palantir’s role in creating the U.S. government’s international spy machine, Sam Biddle, The Intercept, 2/2/2017
XVI. Afterward: Truth and Consequences
I. Quotes On Deep State Origin of PROMIS, PRISM, and PALANTIR
…Betty Medsger’s new book on the Citizens’ Commission to Investigate the FBI, “The Burglary”, contains some relevant and largely suppressed history. In the wake of the Media, PA burglary and the subsequent newspaper articles exposing J. Edgar Hoover’s red squad surveillance programs (COINTELPRO), some CIA officers began to voice dissent internally about their own agency’s troubling domestic operations, codenamed MHCHAOS. In 1972, Medsger writes, CIA director Richard Helms
“called his top aides together and said he was adamant that MHCHAOS would not be “stopped simply because some members of the organization [the CIA] do not like this activity.” He made changes in order to protect the program more now that the [dissident officers were] so determined to have it end. To the maximum extent possible, within the agency, the program and the agent then in charge of it, Richard Ober, would be identified with terrorism and not with American dissidents. The massive program would in fact have the same functions it always had, including the monitoring and destruction of the more than five hundred alternative newspapers staffs it had under surveillance. (At the same time, the FBI also monitored alternative and campus newspapers, sometimes suppressing them.)
Henceforth, Colby wrote in a memorandum after that meeting, the label “international terrorist” would replace “political dissident” as the target of the CIA’s illegal domestic operations. As part of this image transformation, Helms did what (FBI’s J. Edgar) Hoover had done many times—and would do again in April 1971 to protect COINTELPRO when he thought it was about to be revealed—to minimize the possibility that secret operations would be exposed.
Helms ended (the CIA’s) MHCHAOS (program) in name, but continued it in reality with a new name: “International Terrorism Group.” It would be much easier for people, including people within the CIA, to accept the domestic operations if they thought they were aimed primarily at stopping terrorism rather than at stopping dissent.”
It’s common to hear law enforcement officials describe non-violent activists as terrorists today. History suggests we can thank former CIA director Richard Helms for that, at least in part. Years after his agency’s assassinations, anti-dissent programs, antidemocratic coups, and other dirty tricks were exposed to the public in congressional hearings during the 1970s, Helms reportedly said that all of it was “just a congressional firestorm over nothing,” Medsger writes.
The CIA’s domestic operations offices are currently based in Denver, Colorado. Per an executive order signed by Ronald Reagan in 1981, the CIA is allowed to collect information about Americans. The details of the order are classified, so we can’t be sure, but it’s a safe bet to assume that if the agency wants to spy on American dissidents, it just calls them Terrorists.”
2) From: How Palantir Conquered the World
“Imagine a company that knows everything about everyone. A company that is equally at ease helping banks identify fraud as it is helping intelligence agencies track down enemies of the state. A company that can combine pictures of you with your cell phone location data, emails you’ve written, your health records and credit card purchases and thousands of other pieces of electronic data to paint an intimate portrait of your life—a portrait that any would-be investigator can pull up with a few keystrokes. A company that can target you anywhere in the world at any time.
Now stop imagining that company, because it already exists. It’s called Palantir Technologies. Palantir is a front company for (DARPA’s Total Information Awareness/Terrorism Information Awareness), a once-secret military and intelligence project to collect and data mine every available piece of information about you.
Palantir is not just a database. It is not simply software. It is a weapon… the power to see into every nook and cranny of someone’s life is the ultimate power. To know where someone lives, where they work, who they talk to, what they talk about, what they buy, what they eat and drink, where they travel and what they do online is to have total control over them. Sauron himself couldn’t ask for anything more.
As CEO (Alex) Karp has bluntly stated: “our product is used on occasion to kill people.”
.. In the final analysis, the true threat is not Palantir itself but the deep state that has given rise to it.”
“(During the process in which Palantir software was being developed), C.I.A. analysts would test (Palantir software) out and offer feedback, and then Stephen Cohen and Aki Jain would fly back to California to tweak it. Jain estimates that from 2005 to 2009, he and Cohen made around 200 trips to Langley, Virginia (CIA headquarters).
…. (With Palintir) Once the data has been integrated, it can be presented in the form of tables, graphs, timelines, heat maps, artificial-intelligence models, histograms, spider diagrams and geospatial analysis. It is a digital panopticon, and having sat through several Palantir demos, I can report that the interface is impressive — the search results are strikingly elegant and easy to understand.
Those appealing visuals were conceived in order to hunt and kill terrorists….
Palantir’s effort to market its software to police departments can also be regarded as an example of how weapons originally meant for the war on terrorism are now being deployed on American streets.”
4) From: The Finish: The Killing of Osama Bin Laden (Webmaster: which was another staged fake news event of course.)
A start-up called Palantir came up with a program that elegantly accomplished what TIA (Total Information Awareness) had set out to do. Founded in 2004 (actually May, 2003) by Alex Karp and Peter Thiel, Palantir developed a product that actually deserves the popular designation Killer App. Newly minted software engineers from the best computer schools in the country were put up in a seventy thousand square foot workspace in Palo Alto. It was stocked with junk food and nicknamed “The Shire,” the Home of the Hobbits in Tolkien’s “Lord of the Rings.” The software produced from this very unlikely source would help turn America’s special forces into deadly effective hunters. Palantir is now worth billions, and has contracts with, among others, the CIA, the NSA, the Defense Department, the Defense Intelligence Agency, the FBI, the National Counterterrorism Center, and the Department of Homeland Security.
5) From: How Peter Thiel’s Palantir Helped the NSA Spy on the Whole World Documents provided by NSA whistleblower Edward Snowden reveal Palantir’s role in creating the U.S. government’s international spy machine
Documents provided by Edward Snowden (prove) that Palantir has helped expand and accelerate the NSA’s global spy network, which is jointly administered with allied foreign agencies around the world. Notably, the partnership has included building software specifically to facilitate, augment, and accelerate the use of XKEYSCORE, one of the most expansive and potentially intrusive tools in the NSA’s arsenal. A report by The Intercept showed that XKEYSCORE’s “collected communications not only include emails, chats, and web-browsing traffic, but also pictures, documents, voice calls, webcam photos, web searches, advertising analytics traffic, social media traffic, botnet traffic, logged keystrokes, computer network exploitation targeting, intercepted username and password pairs, file uploads to online services, Skype sessions, and more.” But how do you make so much data comprehensible for human spies? Palantir sold its services to make one of the most powerful surveillance systems ever devised even more powerful, bringing clarity and slick visuals to an ocean of surveillance data.
II. Bullet Point Summary of Contents: Information presented on this post about PROMIS, PRISM, and PALANTIR spying and tracking software strongly suggests that all play and/or played a central function in global gangstalking operations! In bullet form, these points are:
A. PROMIS
1) PROMIS software was/is mainly used to track so-called “dissidents”
2) PROMIS was/is used in conjunction with meta data
3) PROMIS was used to develop the MAIN CORE list of “dissidents” in 1980s (reported to have 6 million names in 2008)
4) The CIA’s 1960s-70s Phoenix Program computer-data-base system for identifying so-called “dissidents” and creating a “reign of terror” in Vietnam became the model for later state-terror operations such as “Operation Condor” in South America which used PROMIS in its latter stages
5) The inventor/owner of PROMIS charged that Reagan’s Dept. of Justice stole PROMIS and modified it to spy on people
6) The CIA shopped PROMIS to US intelligence agencies in 1981
7) Israeli spies in America stole and then placed a “back door” in PROMIS in 1983, then sold it to governments and spy agencies throughout the world to covertly spy on just about everyone
8) 1997 report stated that NSA has been seeding computers abroad with PROMIS-embedded SMART (Systems Management Automated Reasoning Tools) chips that can be read by US intelligence satellites as part of “an espionage program”
(Webmaster: Would that program be or include “Organized Stalking-Electronic Harassment“?! The elements identified here comprise essential tracking/spying/data collecting and sharing components of this draconian system.)
9) Israeli superspy, Robert Maxwell, and Iran-Contra “Enterprise” scandal criminals, Manucher Ghorbanifar and Adnan Khoshoggi, were involved in selling PROMIS throughout world in the early and middle 1980s
B. PRISM (Planning Tool for Resource Integration, Synchronization, and Management)
10) PRISM is the top-secret government program with which NSA collects, collates, monitors, looks at, and cross-checks different data types provided them from Internet companies, including Microsoft, Yahoo, AOL, Facebook, Google, Apple, PalTalk, YouTube, Dropbox, and Skype.
11) According to Edward Snowden, this data includes “e-mail, chat, videos, photos, stored data, VoIP, file transfers, video conferencing, notifications of target activity…log-ins, etc., online social networking details” – i.e., everything.
12) The attorney general issues a secret order to a tech company to hand over access to its data to the FBI. The FBI then hands that information over to the NSA.
C. PALANTIR (2003-present)
13) Founded in 2003 by Peter Thiel, Nathan Gettings, Joe Lonsdale, Stephen Cohen, and Alex Karp, Palantir is a big data-analytics software company whose technology was developed by computer scientists and analysts from intelligence agencies (2003-2009 time frame), through pilots facilitated by the CIA’s In-Q-Tel Investment Company. Palantir is used for counterterrorism by a number of Western governments
14) Palantir Gotham was/is widely is used by “counterterrorism” offices of US Intelligence Agencies and the DoD, cyber analysts at Information Warfare Monitor, and police departments
15) Palantir reported that computers using AI cannot defeat an “adaptive enemy” alone and need the assistance of human analysts (online human intelligence agents, aka HUMINT/cyber stalkers/cyber warfare, and on-the-ground civilian and special operations forces stalkers)
16) As of 2013, Palantir Gotham’s clients included the CIA, DHS, NSA, FBI, CDC, Marine Corps, Air Force, Special Operations Command, and US Military Academy Joint Improvised-Threat Defeat Organization and Allies.
(Webmaster: Over 2000 posts on this website indicate that all of the above military and intelligence agencies, in collaboration with sheriff’s departments, civilian-military sector operatives, and private sector operatives are involved in organized stalking-electronic torture operations, which are also commonly referred to as counterterrorism, counterintelligence stalking, Information Warfare, and Cyber Warfare, among other names. Online human intelligence (HUMINT) agents (cyberstalkers) as well as on-the-ground spies, surveillance role players, and other “counterterrorism” operatives are also deployed in these covert, unconventional warfare operations against targeted civilians.
All this is consistent with the conclusion that Organized Stalking-Electronic Torture is a US government-sponsored Unacknowledged Special Access Project (USAP) or black project. Speaking as a so-called “targeted individual,” it is truly astonishing to see how many insiders and scumbag-criminal profiteers and vigilante dupes (“useful idiots”) are “in on it.”)
III. Headlines From Whitney Webb Interview Related to Organized Stalking-Electronic Harassment (:
1) The intelligence agencies can use PROMIS surveillance technology to track anything, but they mainly use it for tracking people (they label as) “dissidents.”
2) This is tied in with data bases of what has been accumulated through surveillance.
3) In the US, the Main Core data base of “dissidents” was developed by PROMIS in 1980s. In 2008, it had 6 million Americans on it; probably more by now.
4) This system of keeping data bases on everyone in order to decide who is a dissident and who isn’t really started in the 60’s during the Vietnam War with the CIA’s Phoenix Program “Reign of Terror.” This became the model for a lot that came after, including OPERATION CONDOR in South America that was enabled in its latter stages by PROMIS. They’ve used it for the same thing in other dictatorships and occupied nations around the world.
5) (With their theft of and then sales of the PROMIS software to nations all over the world in the early 1980s), Israel got a back door into all the intelligence agencies of the world. This was basically a coup, because they knew everyone’s secrets because they could see what was happening in real time.
Headlines From Promis Definition by Wikipedia Related to Organized Stalking-Electronic Harassment
6) Bill Hamilton (the inventor and original owner of Promis) and others asserted that the Justice Department (stole the software from them) in order to modify PROMIS, originally created to manage legal cases, to become a monitoring software for intelligence operations.
7) A book written in 1997 by Fabrizio Calvi and Thierry Pfister claimed that the National Security Agency (NSA) had been “seeding computers abroad with PROMIS-embedded SMART (Systems Management Automated Reasoning Tools) chips, code-named Petrie, capable of covertly downloading data and transmitting it, using electrical wiring as an antenna, to U.S. intelligence satellites” as part of an espionage operation.
8) In the early 1980s, Manucher Ghorbanifar and Adnan Khashoggi (major players in the Iran-Contra scandal) both had facilitated the transaction of PROMIS software to Khalid bin Mahfouz, a prominent Saudi billionaire. [5][6]
9) Robert Maxwell, Israeli Spy and British media mogul, was involved in selling the PROMIS software.
Headlines From PALANTIR Definition by Wikipedia Related to Organized Stalking-Electronic Harassment
10) Palantir Technologies is a public American software company that specializes in big data analytics headquartered in Denver, Colorado. It’s founders are Peter Thiel*, Nathan Gettings**, Joe Lonsdale***, Stephen Cohen****, and Alex Karp***** in 2003. (* see below). Palantir developed its technology by computer scientists and analysts from intelligence agencies over three years through pilots facilitated by the CIA’s In-Q-Tel Investment Company.
11) The company is known for three projects in particular: Palantir Gotham, Palantir Apollo, and Palantir Foundry. Palantir Gotham is used by counter-terrorism analysts at offices in the United States Intelligence Community (USIC) and United States Department of Defense. In the past, Gotham was used by fraud investigators at the Recovery Accountability and Transparency Board, a former US federal agency which operated from 2009 to 2015. Gotham was also used by cyber analysts at Information Warfare Monitor, a Canadian public-private venture which operated from 2003 to 2012. Palantir Apollo is the operating system for continuous delivery and deployment across all environments.[5] Their SaaS is one of five offerings authorized for Mission Critical National Security Systems (IL5) by the U.S. Department of Defense.
12) A document leaked to TechCrunch revealed that Palantir’s clients as of 2013 included at least twelve groups within the U.S. government, including the CIA, the DHS, the NSA, the FBI, the CDC, the Marine Corps, the Air Force, the Special Operations Command, the United States Military Academy, the Joint Improvised-Threat Defeat Organization and Allies, the Recovery Accountability and Transparency Board and the National Center for Missing and Exploited Children.
13) The company stated computers alone using artificial intelligence could not defeat an adaptive adversary. Instead, Palantir proposed using human analysts to explore data from many sources, (in a process) called intelligence augmentation. (Webmaster: another name for these human analysts would be online Human Intelligence (HUMINT) agents).
Webmaster Comment: Each of these 13 summary points support the conclusion that PROMIS/PALANTIR software has been and is used in global gangstalking operations.
IV. Notes From: One Nation Under Blackmail: The Enterprise, PROMIS and Casolaro feat Whitney Webb
Notes From Whitney Webb Interview:
At about 21:00, Whitney describes the history of PROMIS Software:
Promis (Prosecutors Management Information System) was developed by a former NSA guy, Bill Hamilton, who created a company, Inslaw, Inc. with this wife Nancy. Inslaw Inc. leased/liscenced the software to the Dept. of Justice, but other government officials quickly recognized that this software would be useful to them. As early as 1981, the CIA was shopping PROMIS around to intelligence agencies in America. By 1982, Israeli intelligence spymaster, Rafi Eitan, heard about Promis and visited the US under an alias (“Dr. Ben Orr”) and tried to setup a demonstration of PROMIS, claiming to be from Israel’s Ministry of Justice. He tried to butter up the Hamiltons and make them think he could give them a good contract. Former Hamilton employee and DOJ employee, C. Madison (Brick) Brewer, passed a copy of Promis software to “Dr. Ben Orr” (Rafi Eitan), who then contacted Ari Ben-Menasha, of Israeli military intelligence. Ben-Menasha passed the software on to an Israeli-American software programmer in California who placed a back door into the Promis software so that whatever entity installs the software on their computers, this would give Israeli intelligence covert access to everything on that computer and even the broader network to which that computer was connected.
The guy who marketed this for Rafi Eitan, was an American, Earl Brian, a technology expert who was formerly in Governor Ronald Reagan’s cabinet. Allen Co., the investment banking firm of Charles and Herbert Allen, who were intimately linked to organized crime networks as well as Leslie Wexner, were also involved in marketing PROMIS.
Earl Brian tried but failed to bankrupt Inslaw, Inc., but then teamed up with Edwin Meese, then Attorney General under President Reagan, and they succeeded in bankrupting Inslaw. Earl Brian sold Promis to Jordan, giving Israeli intelligence access to their intelligence. Robert Maxwell proved to be a better salesman than Bryan, so Eitan hired him to replace Bryan as the Promis software salesman to intelligence agencies and corporations and governments all over the world. Financed by Israeli intelligence, Maxwell started buying up many companies. He sold Promis all over the world, to the Soviet Union, western Europe, and nuclear labs in the US. The sales to American nuclear labs were enabled by then Secretary of State and National Security Advisor, Henry Kissinger, and Senator John Tower. Maxwell’s daughters, Christine and Isabel, worked for the company that sold Promis.
So (with their theft of and then sales of the PROMIS software to nations all over the world), Israel got a back door into all the intelligence agencies of the world. This was basically a coup, because they knew everyone’s secrets because they could see what was happening in real time. And you could argue that ever since then, especially by the early 1990’s with Israel’s venture capital scene, you’ve seen the Israeli technology industry develop as it has and be intimately interlaced with it’s intelligence apparatus for decades now. Because it was a coup and they didn’t want to relinquish that advantage. My other reports note that Israeli media outlets have admitted that a lot of the Israeli tech industry comprises front companies for Israeli intelligence. They’ve admitted that Blackcube is that. And so is Carbyne 911, which focuses mainly on the US.
(With PROMIS surveillance technology), they can track anything, but the intelligence agencies mainly use it for tracking people (they label as) “dissidents.” This is tied in with data bases of what has been accumulated through surveillance. This really started in the 60’s with the CIA’s Phoenix Program in the Vietnam War; keeping data bases on everyone and deciding who is a dissident and who isn’t. The Phoenix Program was basically a ‘reign of terror’ in Vietnam. This was the model for a lot that came after, including OPERATION CONDOR in South America that was enabled in its later used by PROMIS. In other dictatorships around the world, they’ve used it for the same thing.
In the US, the Main Core data base of “dissidents” was developed by PROMIS in 1980s. In 2008, it had 6 million Americans on it; probably more by now. Basically, under every person’s name is everything the NSA has ever illegally surveilled you for. It’s your whole digital footprint basically.
Now I would argue that the successor to PROMIS is PALANTIR, what they use to analyze all that data. The people behind the Main Core list, like John Pointdexter and Richard Perle, are the behind the scenes architects of PALINITIR and they guided Peter Thiel, Alex Carp and Alan Wade from the CIA in setting up PALANTIR. The CIA helped set up PALANTIR because the CIA was always the intended client of PALANTIR. It was set up by the CIA’s IN-Q-TEL. Now PALANTIR’s client list includes SPACE FORCE and all 18 intelligence agencies.”
Robert Maxwell was the guy who sold PROMIS to all the intelligence agencies that used it to mostly track people. The CIA also made a version of PROMIS that was mostly used for tracking money for money laundering and was (is) used by organized crime figures. This was used to keep other people from tracking the money. They basically used this to bankrupt the financial world. The CIA and Israel were cooperating and collaborating throughout all this. They were working together in Iran-Contra back in the 80s.”
Whitney Webb: From: 30:45 / 51:39 Ep 268 One Nation Under Blackmail: The Enterprise, PROMIS and Casolaro feat Whitney Webb
V. PROMIS (Prosecutors Management Information System): (From: Wikipedia):
PROMIS was a case management software developed by Inslaw (formerly the Institute for Law and Social Research), a non-profit organization established in 1973 by Bill and Nancy Hamilton.[1] The software program was developed with aid from the Law Enforcement Assistance Administration to aid prosecutors’ offices in tracking; in 1982 (by which time Inslaw became a for-profit entity) Inslaw received a $10 million contract by the Justice Department to develop an improved PROMIS application for U.S. attorneys’ offices.[1] Having previously developed a 16-bit version of PROMIS, Inslaw developed a 32-bit version, for various operating systems, specifically VAX/VMS, Unix, OS/400, and (in the 1990s) Windows NT.[1]
The Hamiltons and the Justice Department (Webmaster: under AG Edwin Meese) engaged in an “unusually bitter contract dispute” over the software,[2] and Inslaw entered bankruptcy.[3] The Hamiltons sued the federal government, alleging that the Justice Department had dishonestly conspired to “drive Inslaw out of business ‘through trickery, fraud and deceit'” by withholding payments to Inslaw and then pirating the software.[2] A bankruptcy court and federal district court agreed with the Hamiltons, although these rulings were later vacated by a court of appeals for jurisdictional reasons.[2] Hamilton and others asserted that the Justice Department had done so in order to modify PROMIS, originally created to manage legal cases, to become a monitoring software for intelligence operations.[2][4] Affidavits created over the course of the Inslaw affair stated that “PROMIS was then given or sold at a profit to Israel and as many as 80 other countries by Dr. Earl W. Brian, a man with close personal and business ties to then-President Ronald Reagan and then-Presidential counsel Edwin Meese.“[4]
In September 1992, a House Judiciary Committee report raised “serious concerns” that Justice Department officials had schemed “to destroy Inslaw and co-opt the rights to its PROMIS software”[4] and had misappropriated the software.[2] The report was the outgrowth of a three-year investigation led by Jack Brooks, the committee’s chairman, who had launched in investigation in 1989.[4] The report faulted the Justice Department for a lack of cooperation in the investigation and found that “There appears to be strong evidence, as indicated by the findings in two Federal Court proceedings as well as by the committee investigation, that the Department of Justice ‘acted willfully and fraudulently,’ and ‘took, converted and stole,’ Inslaw’s Enhanced PROMIS by ‘trickery fraud and deceit.'”[4]
A book written in 1997 by Fabrizio Calvi and Thierry Pfister claimed that the National Security Agency (NSA) had been “seeding computers abroad with PROMIS-embedded SMART (Systems Management Automated Reasoning Tools) chips, code-named Petrie, capable of covertly downloading data and transmitting it, using electrical wiring as an antenna, to U.S. intelligence satellites” as part of an espionage operation.[1]
In the early 1980s, Manucher Ghorbanifar and Adnan Khashoggi both had facilitated the transaction of PROMIS software to Khalid bin Mahfouz, a prominent Saudi billionaire. [5][6]
The media mogul and alleged Israeli spy Robert Maxwell was involved in selling the PROMIS software.[1]
References
1. Steve Ditlea, In New French Best-Seller, Software Meets Espionage, New York Times (June 20, 1997).
2. Jeffrey A. Frank, The Inslaw File, Washington Post (June 14, 1992).
In re Inslaw, Inc., 97 B.R. 685 (D.D.C. 1989).
3. Richard L. Fricker, The INSLAW Octopus, Wired (January 1, 1993).
4. Jack Colhoun (23 February 2021), CAM Exclusive: CIA Adapts Database Software Called PROMIS with Back Door for Cyber-espionage
5. Ryan Gallagher (20 April 2011). “Dirtier than Watergate”.
VI. NSA’s Eschelon (From: “Monarch: The New Phoenix Program” By Marshall Thomas)
Signals Intelligence refers to the ability to eaves drop on cell phones, land lines, radios, and email. Eschelon was the name of the program that was exposed in Australia when it was charged with being used for political purposes. Eschelon‘s surveillance power lies in its ability “to tap all international and some domestic communications circuits, and sift out messages which sound interesting. Computers automatically analyze every telex message or data signal, and can also identify calls to, say, a target telephone number in London, no matter from which country they originate.” According to the BBC, “Every international telephone call, fax, e-mail, or radio transmission can be listened to by powerful computers capable of voice recognition. They home in on a long list of key words, or patterns of messages. They are looking for evidence of international crime, like Terrorism.” Building on an original post WWII alliance between the US, Britain, Australia, New Zealand, and Canada, Eschelon had by the late 1980‘s expanded to include joint operations with Germany, Japan, and China. It was initiated under the legal premise that while it is not permissible for the US government to monitor the conversations of its citizens without a warrant, it is not illegal for British intelligence to monitor American citizens, etc. Once the “take” has been pooled, the respective agencies can have safe access to their own domestic intelligence, because the Britons, Australians, or Germans did it, and not the home government. The primary operating agency for all Eschelon activities worldwide is the US National Security Agency [NSA]. (Rupert pg 228) When Boeing beat European Airbus in a major sale worth billions of dollars the Europeans accused the US government of conducting industrial espionage on behalf of Boeing using Eschelon or related technologies.
Wikipedia: ECHELON, originally a secret government code name, is a surveillance program (signals intelligence/SIGINT collection and analysis network) operated by the five signatory states to the UKUSA Security Agreement:[1] Australia, Canada, New Zealand, the United Kingdom and the United States, also known as the Five Eyes.[2][3][4]
Created in the late 1960s to monitor the military and diplomatic communications of the Soviet Union and its Eastern Bloc allies during the Cold War, the ECHELON project became formally established in 1971.[5][6]
By the end of the 20th century, the system referred to as “ECHELON” had greatly expanded.[
VII. https://privacysavvy.com/security/spying/prism-program/
Nwachukwu Glory
Last updated: September 13, 2022
Read time: 18 minutes
Disclosure
The post explains the PRISM program in detail to you alongside providing you with some practical ways to escape this mighty spying.
Sneak peek at PRISM program
PRISM – initially a top-secret but now a reported fact, is a program of the National Security Agency (NSA) through which it gets direct access to tech companies’ servers. This way, the agency receives users’ information, including emails, SMS, videos, chat messages, browsing history, and other sensitive data. Most high-tech companies like Microsoft, Facebook, Google, and Apple are bound to give access via PRISM. Its official purpose was to facilitate the surveillance and protection of US citizens. However, it threatens the users’ privacy policy globally. Let’s dig out more about the PRISM program in this guide.
In 2013 the Washington Post revealed the existence of a secret act called the Prism program. This information was leaked by militarization, who was a private contractor for Booz Allen Hamilton.
The leak was a massive shock in the U.S and around the world. Booz Allen compiled slides detailing how the National Security Agency (NSA) body got direct access to tech servers and pulled out information.
Big tech and internet firms such as Microsoft, Apple, Verizon, Yahoo, AT&T, Google, etc. cooperate with the NSA by giving direct access to their servers. The Guardian also published similar news about the National security Agency’s privacy (NSA) intrusion.
However, the PRISM program’s purpose was not well defined due to the Tech and Internet corporations’ constant denial and contradictions. That has led to the confusion of so many individuals and organizations that really cared about privacy.
Like we said before, the aim of the NSA PRISM program is gathering information from tech organizations. But the tech companies have been vehemently denying it. The actual objective of the Prism program and how the Government collects information is shrouded in secrecy. However, we have dug deep to provide detailed information about the PRISM program.
Some people still think that the NSA can’t wield such powers. Others believe the PRISM program is real. This article would provide you with all the information you need to know about the NSA PRISM Program.
Separating truth from the myths about the Prism Program
The PRISM program aims at gaining direct access to the communication of users. The information includes email communication, voice calls, SMS, social media communications, metadata, video calls, search preference, etc. The constitution governs this unlimited access to information by the NSA through the PRISM program.
Section 702 of the FISA (Foreign Intelligence Surveillance Acts), which became law in 2008, allows the Prism Program to gain direct access to the servers of Tech Companies. Since then, the United States government has drastically increased intelligent bodies’ ability to gain local and foreign information.
The intelligent bodies can investigate the retrieved information targeting terrorist, criminals, and even those not suspected of anything. Formerly the NSA was unable to obtain information from people living outside of the USA.
However, that has changed with the PRISM program formation. It does not matter what you do, where you live, whether you commit a crime or not, the NSA can access your personal information.
Why was PRISM created
(Unsplash)
PRISM Act of 2007 is an electronic data collection that aims at protecting the USA according to the NSA. It was a top-secret and advanced surveillance program of the NSA.
The PRISM program had a code-named US-984XN. According to the leak presentation, the NSA claimed that it launched the program to overcome the FISA warrant’s pitfalls. The FISA warrant is in charge of tracking down and prosecuting foreign terrorists.
But court mandates were needed before they can access and investigate the information of suspected criminals. The NSA wanted to overcome this challenge and have the flexibility of tracking down anyone when the body wants. Furthermore, the NSA noted that the USA has advantages in tracking down terrorists because most of the big tech companies reside in the U.S.
Aside from having the biggest tech companies the US also has most of the internet infrastructure. Therefore the NSA took advantage of the US technological might to create the PRISM program. It targets both the sender and receiver, whether based in the US or not.
The NSA disbanded FISA because it protected some people that are not bounded by the FISA law. FISA must go to court and get orders before gaining access to the communications of foreigners. Therefore the PRISM program was formed, which was a significant upgrade to the FISA. No court order is required to gain access to information by the NSA.
The PRISM program act further gives the attorney general and the director of national intelligence the power to prosecute telecommunications companies that fail to comply with PRISM. It also indemnifies Tech and internet organizations any consequences of granting the NSA access to user’s information.
FBI acting as the intermediary
The leaked document states that the FBI is the primary intermediary between tech companies and the various intelligence agencies. In the leaked documents, the National security Agency hailed the PRISM act as one of the most productive, unique, and most valuable assets to the NSA.
It boasts about how the FBI was able to gather information from tech companies. It also boasts about how the number of obtained communications from Skype astronomically rose to 248% as far back as 2012. The information gathered from Facebook rose by 131%, while Google rose by 63%.
When the NSA gathers information through the FBI, it reviews the communications, and if it warrants further investigations, the NSA will issue a “Report.” According to the leaked document, the NSA generates more than 2000 PRISM program-based reports monthly.
How NSA PRISM Collects data
(Unsplash)
The PRISM program activities are shrouded in secrecy, which is not also helped by the constant denial of tech companies. But from what we know and also from leaked documents, the PRISM program relies on two aspects for its data collection.
Number one is section 702 of the Foreign Intelligence Surveillance Act (FISA), while the second one is in section 215 of thUS’s e Patriot Act. The PRISM program law authorizes security agencies to retrieve communications and metadata from telecommunication companies like AT&T, Verizon, Google, Yahoo, Facebook, and every other telecommunication and internet company.
The secret law further allows security agencies to collect information and analyze them for up to five years. The program uses a lot of sophisticated tools for information gathering. One of them is the NUCLEON, which gathers information that is related to telephone conversations and SMS.
Another one is MARINA, which stores metadata from the internet. And lastly, PRISM has another tool known as the Signals intelligence Activity Designation (SIGADs), which gathers information from every other system. The PRISM further targets a targeted person’s mobile contact, which can cause an unjustified investigation of innocent people.
What do the telecommunication and internet companies say about PRISM?
All the companies that partake in the PRISM program have vehemently denied the accusation. But no one really expects them to come in public and agree that they share user’s information with the FBI, CIA, and other intelligent bodies anyway. In the past, Larry Page publicly said that any claim that Google compromises its user’s privacy is entirely not valid.
Google’s chief architect Yonatan Zunger has also stated that the only time Google can provide users with information to security authority is when the organization receives specific and lawful orders about the agencies.
He said Google couldn’t disclose user’s information to the PRISM program on such a magnitude. He further stated that he would have quit his role as the Chief Architect of Google if such ever happened.
What about Yahoo? Yahoo’s Ron Bell wrote that the assertion that yahoo compromises its users’ privacy and gives out information to security agencies is false. He said Yahoo does not give users information and communications to any federal agencies. It does not also provide any platform for federal agencies to have access to unfiltered communication.
What did Facebook Founder Mark Zuckerberg say
(Unsplash)
He said the PRISM program report is outrageous and that Facebook has not and would not participate in any program that would grant federal agencies direct access to its servers.
According to him, Facebook only complies with lawful orders for requests about specific identifiers or orders.
Microsoft stance?
Microsoft has vehemently denied that they participated in the PRISM program.
In a statement, the organization said they never have and would not compromise user’s information irrespective of the body demanding for such information.
They will not comply if any US agency has a broad program to retrieve information from its servers. Steve Dowling further stated that Microsoft has never heard of the PRISM program and does not directly access its servers to the Government. They will only provide customer’s records through court orders according to him.
Are the telecommunication/internet companies telling the truth?
It is evident that the internet and telecommunication companies are telling lies. Firstly no organization would come out publicly to agree that they shared user’s information with any intelligence agency.
Accepting they share user’s information would lead to boycott, which would be devastating to their organizations. Initially, many people believe that these internet communication companies were sincere. But the leak came out and made everyone understand how powerful the PRISM program is.
There have also been a lot of controversies here and there, which further proves that the tech companies are not sincere. In a statement by Google’s current CEO, Sundar Pichai, he said that Google only responds to orders about some individuals. This statement proves to some extent that Google participates in the PRISM program.
Yahoo’s Bell has also stated in the past that they send only a tiny percentage of customer’s information to security agencies. This statement sounds like a damage control mechanism, and it really proves that Yahoo also participates in the PRISM program.
How big was the leak?
Never in the NSA’s history has there been a leak as massive as the PRISM program leak. The leak documents first sufficed in April 2013, and such a leak is uncommon in the history of the NSA.
The NSA is the world’s largest surveillance organization, and it prides itself on maintaining the highest form of secrecy. Therefore the leak was a massive shock to everyone. This program allowed them to obtain information from tech companies without court orders.
Should we be worried that the NSA gets unfiltered access to the user’s information
(Unsplash)
Many internet and telecommunication corporations have systems that give access to intelligence agencies. This information can also be electronically transmitted to other Government institutions through the company servers.
Companies are obliged to provide information due to the constitutional backing of PRISM. The program has left many American’s confused, concerned, and feeling a great lack of control over their privacy.
The majority of people think that their personal data is no more secure. Although data collection through PRISM has its benefits, especially in the investigation of crimes.
But the disadvantages clearly outweigh the advantages, and many people also believe that it is impossible to live daily without any form of tracking. This view is shared by at least 6 in every 10 American citizens. Americans no longer feel confident in the manner tech companies handle and transmit their personal information.
What about the privacy policy?
Most people do not read privacies before creating online accounts. Most adults would simply accept privacy policy while creating accounts. However, reading a privacy policy would not do much in ensuring your data remains confidential.
The privacy policies do not, in any way, guarantee that the Government authorities will not get access to your personal information through the PRISM program. Data privacy laws have a lot of loopholes for tech companies to exploit. Moreover, a lot of adults do not understand data privacy policy laws and regulations.
The NSA PRISM has unfiltered access to telecom servers, and there are lots of questions to be asked. Is the information subject to the appropriate judicial procedure? They don’t because the PRISM information gathering is not a search warrant under the Constitution’s Fourth Amendment.
Also, the amendment does not require intelligence agencies to show that a target is either a criminal or not. This implies that the PRISM data collection system can target anybody irrespective of who you are. This is a great concern for the public because it can be used for political and business advantages by corrupt officials.
Which companies are involved?
Google, Yahoo, AOL, Apple, Skype, Vodacom, AT&T, YouTube, PalTalk, Dropbox (a popular US-based file hosting service) are among the most prominent companies involved in PRISM. However, all telecommunication and IT companies in the USA must cooperate with PRISM. But the leaked documents state that 98% of the information gathered through PRISM comes from Google, Microsoft, and Yahoo.
All the major companies involved in PRISM have publicly denied the allegations stating that no external or Government agencies have access to their servers. However, it is clear from the leak that the NSA gains direct access to tech company servers to pull out information anytime.
What do the defenders of PRISM say?
PRISM Defendants have stated that the program targets foreign users, and PRISM doesn’t gain access until they make a request. The New York times said in the last two instances of the PRISM data request, organizations created a secure dropbox storage where they electronically deposit specific information for the intelligence agencies.
In the past, Google also wrote a letter to the Department of Justice, seeking permission to disclose how PRISM works. Facebook also wanted permission to provide transparency on how the PRISM program works to enable people to see the true picture.
They got the approval, and Google discussed with Wired Magazine the different ways it passes legal information to the Government. Google insisted that it never gave intelligence body direct access to its servers for information gathering.
Why is Twitter not mentioned
(Unsplash)
No one has been able to answer if Twitter corporates with the PRISM program because the leak did not make mention of Twitter in any way.
It seems to some that Twitter said no and refused to corporate with the NSA PRISM program.
However, the PRISM program is backed by the constitution, obliging Twitter and other tech companies to corporate.
All companies in the USA should necessarily comply with federal laws, and Twitter must cooperate to the Government’s request for data. But Twitter is under no legal obligation to make the process of information gathering easy for any Government organization.
From all indication, it seems Twitter made the process of information gathering from their servers complicated for NSA. While other companies changed their system to transmit data to government agencies effectively and also discussed technical methods of information gathering, Twitter held their grounds and made the process very difficult. Twitter refused to join the bandwagon in steamrolling the information gathering process.
What type of data does the PRISM monitor?
According to the leak slides and other supporting documents published by the Washington Post and the Guardian alongside all other trusted sources till date, the monitored data include the following.
Additionally, data that Google and Microsoft share include Drive files, live surveillance, entire photo library, video chat, voice chats, metadata, information about who is talking to who, search terms, etc.
What about the information on private servers and the cloud?
It does not matter if your information is on shared, dedicated, or private servers; it is not safe if it is online. Simple.
Aside from the fact that Google, Bing, and other search engines crawl users’ emails and other data to target their ads, the PRISM program can have access to your email for use by the NSA.
This means third parties may have read your emails. The NSA and other intelligence bodies may have also read your iCloud emails and other third-party system emails.
What is the difference between the PRISM program and the data Verizon gives to the NSA?
According to the constitution, every telecommunication and internet company must provide information to federal agencies. However, the data Verizon gives to the NSA is different from the PRISM program.
Verizon gives only metadata to Government security agencies, which means they can see who you call and how long the call lasts, but they do not listen to your communication. They don’t listen to your voice mails as well. But this is a separate NSA program, and the PRISM program is more robust.
Has the PRISM program affected the USA Freedom ranking
(Unsplash)
According to freedom ranking, the USA ranked second most internet-free country on earth before the PRISM program leak. But the U.S. position drastically changed after the leak.
Freedom ranking started in 2015 by Civil liberties. It is an independent body run by Germany’s Liberales Institute, the U.S. Cato Institute, and Canada Fraser Institute. The index measures freedom of speech, freedom of religion, freedom of association, freedom of movement, etc.
Its rating measures on a scale of 10 to 0. In the last rating done in 2019, the U.S. dropped down to number 15 on the list. People thought that the PRISM program significantly contributed to pushing down the United States.
Is there a way to avoid the PRISM program?
There is no way you can avoid the PRISM program, whether you are an American citizen or not. That is the hard truth.
It is because American companies own the biggest tech companies. Organizations like Google, Facebook, Yahoo, Microsoft, and other major tech giants all have their servers resident in the US even though they have servers in other locations.
This means intelligence bodies can target your information whether you are a US citizen or not. Almost everyone around the world has an account with one or more of the above-listed tech companies. So technically, no one can avoid the PRISM program.
Ironically Microsoft ran an advertisement program with the catchphrase “Your Privacy is our Priority.” They were still the first organization to grant the NSA direct access to their servers through the PRISM program. Microsoft began giving direct access to its servers as far back as 2007.
Yahoo was next in line and gave the NSA direct access in 2008. Next were PalTalk, Facebook, and Google in 2009. YouTube gave access in 2010, AOL, and Skype in 2011. Finally, Apple obliged in 2012. The PRISM program keeps expanding as each day goes by, and many other medium-sized and multinational tech companies have joined the bandwagon.
So, one cannot get away from the PRISM program completely. But you can minimize the likelihood of Five Eyes, NSA, and other organizations tracking your voice traffic and internet activities.
The best thing you can do to escape PRISM is masking your IP address with a Virtual Private Network (VPN). However, the infamous free anonymizing tool Tor also lets you achieve that, but VPN is the safest and most reliable way of doing it.
A VPN client will encrypt your internet traffic and send it to another location for decryption. When you have a quality VPN service on, the NSA could see some traffic traveling through the tunnel, but it won’t be able to separate your internet traffic from others.
It would help if you also considered ditching tech giants to avoid the PRISM program. That can be harder for many, as most of us rely on Apple, Google, Microsoft, and Facebook in our daily lives.
What you can do here is, try using secure alternatives to the services offered by those tech giants. For example, instead of using Gmail, you should better use some secure email providers.
Concerning searching online, you can live without Google. Yes, that is true. Few people apprehend that plenty of exceptional secure alternative search engines exist out there. If you ask us, at the top of our list is the intelligently dubbed DuckDuckGo.
Encrypting your data is another useful way of minimizing data exposure to the PRISM program. TrueCrypt alternatives available in the market will do this task for you.
Who do you blame for the PRISM program
(Unsplash)
People frown at data breach because it puts their private information in the hands of third parties. They see what you read, what you say, your videos, your search, your emails, and much other information about you.
However, the Government claims that the PRISM program targets criminals, but the negatives far outweigh the positives. People no longer have freedom on the internet because of fear of data breaches.
So who should be blamed for the PRISM program? First of all, blame it on congress for legislating such powers to the intelligence agencies.
Secondly, blame it on the FISA court that passed the PRISM act into law and, lastly, blame it on the Government for discarding the true values of the American society.
What did the Government do about the leak?
There were diplomatic rows after the leak, which led to the prosecution of the people responsible for the leak. However, the Government cannot retrieve the information contained in the slide. Edward Snowden was one of the major sources of the leak, but he fled to Hong Kong.
In an interview with the Guardian, he stated that he fled to Hong Kong because of its perceived freedom. Hong Kong ranks number one on the Freedom index list with an impressive score of 8.91. The Freedom index measures a scale from 10 most free to 0 least free nations worldwide. He said people had the freedom of speech over in Hong Kong, and he intends to exercise that.
Although the United States has a bilateral agreement with Hong Kong on extradition. However, extraditing someone based on political grounds should more likely be vetoed by either Beijing or Hong Kong.
Final notes
The PRISM program serves as the National Security Agency’s tool used to obtain information directly from tech companies. Companies such as Facebook, Apple, Google, Microsoft, and other Tech/information communication giants are all obliged to grant access to the NSA through the PRISM program.
It remained a top secret before it got leaked and reported. The NSA gained access to information such as emails, calls, SMS, video, search history, chats, metadata, and just about a communication type through the PRISM program. According to the leaked document, it gets direct access to the servers of tech companies.
However, all the tech companies have denied this allegation even though the leaked documents expose the huge data privacy issue. Defenders of the PRISM program would always say that the act facilitates surveillance and protects the US. However, the PRISM program clearly violates the user’s privacy and poses a significant risk.
The program also targets people who live outside the USA. This means that it can spy on almost everyone. It is an unprecedented militarization of international and local communication infrastructure that significantly threatens the freedom of the internet.
The PRISM program troubles anyone concerned about their privacy. But the reality is you cannot do much as an internet user rather than only minimizing your exposure to it. Taking care of your digital privacy by using a VPN, a private search engine, and encrypting your computer data are your best defenses in a continuous tussle against the PRISM program.
VIII. https://www.cnet.com/news/privacy/what-is-the-nsas-prism-program-faq/
We now know that the NSA uses something called PRISM to monitor private Web data. Sounds like “1984.” What does it really mean?
Benjamin Dreyfuss headshot
Emily Dreyfuss headshot
Benjamin Dreyfuss
Emily Dreyfuss
June 7, 2013 11:44 a.m. PT
8 min read
Editors’ note: Updated on June 12 to include new information.
You’ve been hearing about a top-secret government program reportedly giving the NSA access to digital consumer information held by large tech companies. But what is it, really, and how does it affect you? Reports are changing fast, so we created this FAQ to let you know what is known so far. We will continue to update it as the facts become clear.
What is PRISM?
PRISM stands for “Planning Tool for Resource Integration, Synchronization, and Management,” and is a “data tool” designed to collect and process “foreign intelligence” that passes through American servers. Details about its existence were leaked to The Washington Post and The Guardian by Edward Snowden, a 29-year-old NSA contractor.
It has now been acknowledged by the Obama administration.
In the words of national security reporter Marc Ambinder, “PRISM [is] a kick-ass GUI that allows an analyst to look at, collate, monitor, and cross-check different data types provided to the NSA from Internet companies located inside the United States.”
It only targets foreigners?
PRISM “cannot be used to intentionally target any U.S. citizen (PDF), or any other U.S. person, or to intentionally target any person known to be in the United States, according to a statement released by Director Clapper on June 8.
Why would there be foreign intelligence on American servers?
A huge amount of foreign internet traffic is routed through or saved on U.S. servers. For instance, a majority of Facebook and Google users are not from the United States.
So how does this affect an American’s data?
The key word is intentional. The NSA can’t intentionally target an Americans data. But analysts need only be at least 51 percent confident of a target’s “foreignness.”
What is PRISM not?
It is apparently not the name for an overarching secret surveillance program in affiliation with certain large tech companies, as was originally reported by The Washington Post. Director of National Intelligence James Clapper has released a statement saying, “PRISM is not an undisclosed collection or data mining program.” Instead, the name PRISM appears to refer to the actual computer program used to collect and analyze data legally requested by the NSA and divulged by Internet companies. This matches reports from CNET and The New York Times.
However, as the New York Times reported late Friday evening, it has come to light that the nine large tech companies first reported to be working with the NSA to divulge information have, in fact, made it easier for the government to access data from their servers.
Which companies are involved?
Microsoft, Yahoo, AOL, Facebook, Google, Apple, PalTalk, YouTube, and Skype. Dropbox is allegedly “coming soon.” However, 98 percent of PRISM production is based on just Yahoo, Google, and Microsoft.
All nine of them have explicitly denied that the government has “direct access” to their servers. Reliable sources have confirmed to CNET that PRISM works on a request-by-request basis, rather than unfettered access, as was originally reported by the Washington Post. Here is a direct quote from our in-depth article on this issue:
Those reports are incorrect and appear to be based on a misreading of a leaked Powerpoint document, according to a former government official who is intimately familiar with this process of data acquisition and spoke today on condition of anonymity.
Still, it appears that though they may have withheld direct access to their servers, many did in fact agree to collaborate with the government on “developing technical methods to more efficiently and securely share the personal data of foreign users in response to lawful government requests.”
How?
It’s not entirely clear, but according to the New York Times, in at least two cases the companies discussed creating secure digital dropboxes where information sought by the NSA could be electronically deposited. Facebook reportedly actually built such a system.
On Tuesday, June 11, Google published a letter to the Justice Department, asking for permission to disclose the mechanism by which FISA requests are completed. A Facebook spokesperson joined the call, announcing that Facebook would “welcome the opportunity to provide a transparency report that allows us to share with those who use Facebook around the world a complete picture of the government requests we receive, and how we respond.” After writing the letter to the Justice Department, Google discussed with Wired Magazine the ways it gets legal information to the government, insisting throughout that reports of “direct access” to Google servers have been erroneous. Jump to our How does it work? section for more details.
Why isn’t Twitter a part of PRISM?
That’s a very good question that at first no one was able to answer.
It now appears as though the answer is: Twitter simply said no.
Companies are legally obligated to comply with any legitimate government request for user data, but they are under no legal obligation to make that process easier. Twitter apparently refused to join the other nine in steam rolling the process.
On Friday, June 7, the New York Times wrote:
Twitter declined to make it easier for the government. But other companies were more compliant, according to people briefed on the negotiations. They opened discussions with national security officials about developing technical methods to more efficiently and securely share the personal data of foreign users in response to lawful government requests. And in some cases, they changed their computer systems to do so.
What type of data is monitored?
According to “slides and other supporting materials” given to the The Guardian and The Washington Post by Snowden: “e-mail, chat, videos, photos, stored data, VoIP, file transfers, video conferencing, notifications of target activity…log-ins, etc., online social networking details” — so, everything.
For instance, Google data includes “Gmail, voice and video chat, Google Drive files, photo libraries, and live surveillance of search terms.”
The original report suggests that “NSA reporting increasingly relies on PRISM” as its leading source of raw material, accounting for nearly one in seven intelligence reports.
A reliable source tells CNET that both the contents of communications and metadata, such as information about who’s talking to whom, can be requested.
Can they read my iMessage?
Theoretically, yes. That is the kind of data the program has access to.
So someone has read my e-mail?
Aside from the fact that Google’s algorithms crawl your e-mail all the time to target ads at you, “someone” within the NSA may have read your e-mails.
Is it even legal?
Yes, under Section 702 of the Foreign Intelligence Surveillance Act (FISA) of 2008 and the Protect America Act of 2007. Director of National Intelligence James Clapper released a statement Thursday night saying that “Section 702 is a provision of FISA that is designed to facilitate the acquisition of foreign intelligence information concerning non-U.S. persons located outside the United States. It cannot be used to intentionally target any U.S. citizen, any other U.S. person, or anyone located within the United States.” FISA was renewed last year by Congress.
According to the Post, “Late last year, when critics in Congress sought changes in the FISA Amendments Act, the only lawmakers who knew about PRISM were bound by oaths of office to hold their tongues.” When the story broke, Ron Wyden (D-Ore.) and Mark Udall (D-Colo.) released a letter they cowrote to the Justice Department expressing their concerns relating to the program.
How does it work?
Essentially like this: The attorney general issues a secret order to a tech company to hand over access to its data to the FBI. The FBI then hands that information over to the NSA.
But many technical questions remain, such as: when given access, can the NSA tap directly into the companies’ servers, as was originally alleged? Is the data printed out and handed to an NSA operative? Is an NSA operative stationed on the company’s campus at a specific work station designed for such transactions?
On Tuesday, June 11, Google went to Wired Magazine in an attempt to answer some of these lingering questions. Google spokesman Chris Gaither flatly denied giving direct access to Google’s servers, stating:
“When required to comply with these requests, we deliver that information to the US government — generally through secure FTP transfers and in person. The US government does not have the ability to pull that data directly from our servers or network.”
One thing to note about this answer is that in order for the secure FTP transfer to take place, it looks as though Google does have a special encrypted dropbox on campus — which you could technically call a “company server” — that stores and delivers the requested data.
Splitting hairs? Perhaps. It is very different from total, real-time access to Google’s main servers.
Is this the same as the data Verizon is giving to the NSA?
No. This is separate. The data Verizon gives to the NSA is only metadata, so although the government can see who you call and how long you talk to them, they are not listening in on your voice mails and phone calls. But again, that’s a separate NSA program. For more information on it, read this.
What’s the fallout?
Well, so far respected human rights watchdog Freedom House has downgraded America’s freedom ranking. Last time their survey was released, the United States was the second most free country on Earth in terms of Internet freedoms. That position is about to change.
How can I avoid this?
You can’t.
Should I be outraged?
Probably! But maybe not. President Obama addressed PRISM on Friday and essentially said, “Don’t worry. You can trust us.”
Who is to blame for this?
Well, let’s let Anthony Romero of the American Civil Liberties Union sum it up. He is quoted by The New York Times as saying, “A pox on all the three houses of government. On Congress, for legislating such powers, on the FISA court for being such a paper tiger and rubber stamp, and on the Obama administration for not being true to its values.”
What happens next?
A diplomatic circus. The Obama administration has prosecuted leakers at an unprecedented rate, but it’s going to have at least a bit of a hard time getting its hands on the source of these leaks: Edward Snowden is apparently holed up in a hotel in Hong Kong.
The NSA contractor outed himself in an interview with The Guardian’s Glenn Greenwald in which he says that he chose Hong Kong because, “[it] has a reputation for freedom in spite of the People’s Republic of China. It has a strong tradition of free speech.” Hong Kong is a Special Administrative Region of The People’s Republic of China and has its own government distinct from, but ultimately subject to, Beijing. The United States does have a bilateral extradition treaty with Hong Kong, but a request from the U.S. based on political offenses could be vetoed by either Hong Kong or Beijing. For now Snowden says, “the only thing I can do is sit here and hope the Hong Kong government does not deport me.”
IX. NSA mass surveillance leaks: Timeline of events to date
The U.S. government mass surveillance scandal may be the biggest ongoing story of the year. In this updating timeline, you can explore the full scope of the Edward Snowden leaks, which have implicated the world’s most powerful nations in the worldwide spying operation.
By Zack Whittaker, Contributor on Nov. 22, 2013

Introduction: The surveillance scandal in a single slideshow
The biggest scandals of the year — perhaps even the decade — the U.S. government’s massive, global surveillance machine has been hitting headlines in international media, as a result of documents leaked by former U.S. contractor Edward Snowden.
Featured
This tech CEO fired two engineers for having second full-time jobs, warns they’re part of a new trend
This company successfully switched to a four-day workweek. Here’s how they did it
How to convert your home’s old TV cabling into powerful Ethernet lines
Scared of the dark? You won’t be if you get one of our favorite flashlights
With dozens of documents already published since they first went live in June 2013, Snowden is slated to have stolen hundreds of thousands of files. Led by The Guardian and The Washington Post on both sides of the Atlantic, numerous other news agencies have also reported the vast number of secret snooping programs.
The scandal has implicated numerous high-profile G20 countries in assisting the U.S. government in its intelligence gathering efforts. Meanwhile, many other countries have fallen foul to the U.S.’ privacy-invading surveillance techniques. The past six months alone have seen some of the toughest tests to global diplomatic relations since World War II.
From PRISM to UPSTREAM, ROYAL CONCIERGE and EGOTISTICAL GIRAFFE, there is a lot to take in and plenty more to find out.
We’ve gathered all the leaks to date all in one place in this slideshow, which will be kept up to date, for your viewing.
(News sources: The Guardian; The Washington Post; The New York Times; Der Spiegel; The Wall Street Journal; O Globo; CNET; South China Morning Post; Le Monde; CBS News; Reuters; De Standaard; Politico; Wired; The Japan Times)
Updated on November 25: with two additional slides on NSA malware infiltration, and U.S. working with Singapore and South Korea to tap other South Asian countries.
Updated on December 4: with four new slides on Australian leaks, and how the NSA is collecting 5 billion cellphone records a day, among others

June 6, 2013
Verizon records vacuumed up by NSA under ‘top secret’ Patriot Act order
The Guardian newspaper was first to reveal the U.S. government’s demand to to vacuum up millions of Verizon customer details, including information on phone calls both within the U.S. and between the U.S. and other countries.
The data that is being collected on Verizon customers — including cellular and landline customers — includes all call details or “metadata,” including routing data, such as the originating and recipient phone number; the IMEI unique device identifier; the IMSI number used to identify calls on cellular networks; trunk identifiers; phone calling cards; and the time, date, and duration of the call.
Read more: Verizon records vacuumed up by NSA under ‘top secret’ Patriot Act order (ZDNet)

Source: The Guardian
a-2-prism.jpg
3 of 84 Zack Whittaker/ZDNET
June 6, 2013
PRISM unmasked: FBI, NSA said to be secretly mining data from nine U.S. tech giants
Citing a leaked presentation intended for only senior analysts within the National Security Agency’s (NSA) Signals Intelligence Directorate, the U.S. government began secretly mining user data from companies under a highly classified program called PRISM.
The ring of nine consists of Microsoft, Yahoo, Google, Facebook, AOL, Skype, YouTube, Apple, and video chat room community PalTalk. Apparently Dropbox was slated to be the next one added to the list. The named seven have strenuously denied the claims and reiterated their stance towards maintaining user and customer privacy.
Read more: PRISM unmasked: FBI, NSA secretly mining data from nine U.S. tech giants (ZDNet)

Source: The Washington Post
a-3-obamacyberattacks1.jpg
4 of 84 White House/Flickr
June 7, 2013
Obama’s secret order draws up overseas target list for cyberattacks
The latest leak pointed to U.S. President Barack Obama signing in October 2011 a directive that orders senior intelligence and defense staff to determine which foreign targets should be attacked with cyberweapons should the country come under attack.
Dubbed “Presidential Policy Directive 20,” written just months before the President signed an executive order on cybersecurity — the document describes how the White House could take offensive measures against a hostile country or system “with little or no warning,” and with “potential effects ranging from subtle to severely damaging.”
Read more: Obama’s secret order draws up overseas target list for cyberattacks (ZDNet)
Source: The Guardian

5 of 84 U.K. Ministry of Defense/Wikimedia Commons
June 7, 2013
U.K. government ‘complicit’ in NSA’s PRISM spy program
It wasn’t just the NSA conducting vast surveillance. Almost back to wartime efforts, the U.S. drafted in the help from the U.K. government’s electronic intercepts and listening station, Government Communications Headquarters (GCHQ). The British spy agency reportedly tapped directly into fiber cables on either side of the Atlantic. It also has access to the U.S. government’s PRISM database, allowing the U.K. to bypass mutual intelligence and information sharing treaties.
Read more: U.K. government ‘complicit’ in NSA’s PRISM spy program
Source: The Guardian

6 of 84 Zack Whittaker/ZDNET
June 8, 2013
PRISM: Here’s how the NSA wiretapped the Internet
A new slide released by The Washington Post said that NSA analysts “should use both” the newly-uncovered UPSTREAM program for data collection, as well as PRISM, indicating there are two methods of acquiring private user data.
The secret court order, authorized by the Foreign Intelligence Surveillance Court (FISC) allows the NSA to place a wiretap device on the core fiber optic cables that power the Internet, which effectively vacuumed up every bit and byte of data that flowed through telco’s networks.
Read more: PRISM: Here’s how the NSA wiretapped the Internet (ZDNet)
Image via The Washington Post

7 of 84 Zack Whittaker/ZDNET
June 10, 2013
Guardian reveals identity of NSA whistleblower
Meet Edward Snowden, the former U.S. government contractor turned whistleblower, who willingly revealed his identity by working with The Guardian.
The then 29-year-old said he had “no intention of hiding” who he was because, I know I have done nothing wrong,” he said, despite leaking secrets held close to the chest of the U.S. government. A former technical assistant for the CIA, Snowden also worked with defense contractor Booz Allen and computer giant Dell.
He will ultimately become one of the very few people in U.S. history charged with leaking government secrets under the Espionage Act.
Read more: Guardian reveals identity of NSA whistleblower (ZDNet)
Image via The Guardian (video)
Source: The Guardian
8 of 84 Zack Whittaker/ZDNET
June 11, 2013
U.S. gov’t collects 100 billion surveillance records a month
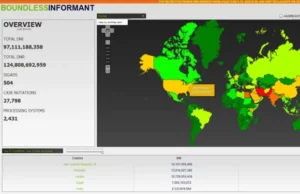
Meet the U.S. National Security Agency’s global intelligence tracking tool, BOUNDLESS INFORMANT.
Users of the tool are able to select countries from a “heat map” to metadata and volume details, as well as different kinds of other information collected by the spy agency. Iran topped the surveillance list with over 14 billion data reports, with Pakistan coming in close second at 13.5 billion reports. Jordan, Egypt and India are also top priorities for the U.S. surveillance efforts, according to the leaked slides and screenshots.
Read more: Boundless Informant: U.S. gov’t collects 100 billion surveillance records a month (ZDNet)
Image via The Guardian
Source: The Guardian

9 of 84 Connue Zhou/Google
June 11, 2013
Google says it wants to disclose FISA requests
In efforts to show it has “nothing to hide” amid the PRISM disclosures by Snowden, Google wrote an open letter to U.S. attorney general Eric Holder to disclose how many secret government orders it receives. It follows an earlier statement by Google chief executive Larry Page stating that the Internet giant had not heard of PRISM until The Guardian first disclosed it in early June.
Read more: Google says it wants to disclose FISA requests (CBS News)

10 of 84 Apple via CNET
June 13, 2013
NSA whistleblower: U.S has been hacking into China, Hong Kong
In the latest round of leaks, fugitive Snowden tells a Hong Kong newspaper that PRISM extends to China and Hong Kong. Citing unreleased documents, the U.S. government has been hacking into computers in the Asia region since 2009, notably those belonging to public officials, businesses, and students.
Read more: NSA whistleblower: U.S has been hacking into China, Hong Kong (CNET)

11 of 84 White House
June 16, 2013
NSA leaked documents reveal U.S. spied on Russian president at G20 summit
The Snowden leaks didn’t just disclose the U.S. government’s intentions to surveil citizens, both domestically and abroad. For the first time two weeks after the first round of leaks were published, foreign governments were also revealed to be targets.
Published by The Guardian, the U.S. was spying on former Russian President Dmitry Medvedev during the G20 summit in London in 2009. The NSA was able to intercept communications between Medvedev and his delegation, thanks to the U.S.’ close relationship with its British counterpart eavesdropping agency, GCHQ.
Read more: NSA leaked documents reveal U.S. spied on Russian president at G20 summit (CNET)
Source: The Guardian
![]()
12 of 84 ZDNet; Microsoft, Google, Facebook
June 17, 2013
Apple, Microsoft, Facebook release new details on national security requests
After denying any direct involvement in the PRISM spying scandal, three Silicon Valley technology giants released new details on U.S. government requests. Under the existing Foreign Intelligence Surveillance Act (FISA), companies are barred from even acknowledging such a court order exists, let alone disclosing it to the public. The move was in efforts to be more transparent about such national security requests for their customers’ data, despite gagging orders in effect.
Read more: Apple, Microsoft, Facebook release new details on national security requests (CBS News)

13 of 84 Zack Whittaker/ZDNET
June 20, 2013
Secret NSA documents on data collection appear more relaxed than first told
More leaks from The Guardian disclose the reach of the NSA’s ability to spy domestically. Two documents outlined how the U.S. spy agency is able to target non-U.S. residents, while the other outlined how it can minimize data collection from U.S. residents. The document shed new light on how the NSA targets individuals for monitoring and surveillance, including the “rules” in which it can acquire data on Americans, in spite of law to protect such domestic spying,
Read more: Secret NSA documents on data collection appear more relaxed than first told (ZDNet)
Image via The Guardian
Source: The Guardian
14 of 84 Zack Whittaker/ZDNET
June 21, 2013
British spy agency said to tap world’s phone calls, e-mails
Further details relating to the U.K. government’s involvement in the NSA’s surveillance are published. In a new slide called “Mastering the Internet,” GCHQ tapped into some of the world’s critical submarine fiber cables, which according to the slides, allows it access to much of the world’s telephone calls and Internet traffic. The data can be stored for up to 30 days, allowing analysts to look over the data.
The Guardian, which reported the story, said GCHQ had been carrying out the operation without warrants, and without public acknowledgement or debate, for almost 18 months.
Read more: British spy agency said to tap world’s phone calls, e-mails (CNET)
Screenshot: ZDNet/TeleGeography
Source: The Guardian

15 of 84 European Union
June 21, 2013
Amid NSA spying scandal, the gloves are off for EU’s justice chief
Europe’s justice chief Viviane Reding was enraged following the news that the U.S. and U.K. — both allies to the 28 member state bloc — were spying on its citizens in breach of EU data protection rules. But at a time when Brussels was looking to amend the privacy laws, Reding was pushing back against some proposals, which were “watered down” according to the politicians debating the law. Now news of the scandal broke, Reding is fighting back against her federal former friend.
Read more: Amid NSA spying scandal, the gloves are off for EU’s justice chief (ZDNet)

16 of 84 Dept. of Justice
June 21, 2013
U.S. files espionage charges against NSA leaker
Just two weeks after the NSA surveillance scandal broke, the U.S. government brought charges against Edward Snowden, whose whereabouts at the time were unclear. Believed to be holed up in Hong Kong, the whistleblower becomes one of the handful of those ever charged under the Espionage Act for leaking what may amount to hundreds of thousands of classified documents.
Read more: U.S. files espionage charges against NSA leaker (CBS News)

17 of 84 Ian Geldard/Twitter
June 24, 2013
Edward Snowden on the run, reportedly in Russia
As the global manhunt for Edward Snowden continues, the plane carrying the NSA leaker touches down at a Moscow airport. Everyone from U.S. authorities to the members of the media were guessing as to where his final destination would be. Russian authorities however did not say whether or not Snowden had formally entered Russian territory.
Read more: Edward Snowden on the run, reportedly in Russia (CBS News)

18 of 84 Microsoft via CNET
June 24, 2013
Skype’s Project Chess: Supernodes ditched for scalability or surveillance?
Skype’s principal architect explained why the company redesigned its backend infrastructure, which many have claimed made it easier for governments to wiretap calls. Following the acquisition of Microsoft, some claimed the infrastructure change to datacenters would make it easier for the NSA to tap into calls.
It follows claims by The New York Times that a small handful of Skype employees established “Project Chess,” a system designed to explore the legal and technical issues behind handing over Skype user data to law enforcement agencies..
Read more: Skype’s Project Chess revealed: Peer-to-peer supernodes ditched for scalability or surveillance? (ZDNet)
Source: The New York Times

19 of 84 CNET Asia
June 25, 2013
Snowden: NSA hacked China telcos, submarine cable network firm
Freshly published documents point to China as the latest victim behind the U.S.’ government’s cyber-operations, as a China newspaper publishes documents implicating the NSA in computer attacks that occurred during a four-year period. The NSA’s activities also included hacking major telcos in efforts to acquire massive amounts of text messages.
The revelations are particularly ironic, as the U.S. has increasingly scaled up its legislative operations against China alleging the Communist Party-ruled country is targeting Western computers and networks.
Read more: Snowden: NSA hacked China telcos, submarine cable network firm (CNET)
Source: South China Morning Post

20 of 84 European Union
June 30, 2013
European officials lash out at new NSA spying report
A top German official accused the U.S. of using “Cold War” methods against its allies regarding the ongoing spate of leaks detailing the NSA’s surveillance operations. It comes amid claims the U.S. government was eavesdropping on EU offices in Washington, New York, and Brussels, citing published leaked documents.
Read more: European officials lash out at new NSA spying report (CBS News)
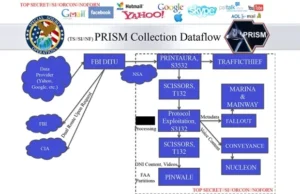
21 of 84 Zack Whittaker/ZDNET
June 30, 2013
Latest NSA leak details PRISM’s bigger picture
New leaks offered further details of the mass collection of email, video and voice chat, photos, file transfers, and other online social networking content on foreign nationals by the NSA in conjunction with the Federal Bureau of Investigation (FBI).
According to one slide, there were 117,675 “active surveillance targets” in PRISM’s database, but this figure does not detail which kinds of users these were, or among them how many Americans had their data collected inadvertently by the program.
Annotations by the Post suggest that PRINTAURA “sorts and dispatches the data stream” into different categories of data from the FBI’s Data Interception Technology Unit (DITU) — understood to be the Tier 1 company wiretaps. The DITU is understood to maintain this equipment, in which the data it collects is then passed to the NSA.
Read more: Latest NSA leak details PRISM’s bigger picture (ZDNet)
Image via The Washington Post
Source: The Washington Post

22 of 84 Jimmy Harris/Flickr
July 3, 2013
Bolivia president’s plane rerouted due to Snowden suspicions
With the fugitive whistleblower Snowden suspected of being on board, the private jet of Bolivian president was forced to land as a number of countries in the region refused to allow the plane through its airspace. The plane needed additional fuel as a result of the non-direct route. Officials denied Snowden was on board, which was confirmed after the plane was searched by authorities on the ground.
Read more: Bolivia president’s plane rerouted due to Snowden suspicions (CBS News)

23 of 84 European Parliament/Flickr
July 4, 2013
EU votes to support suspending U.S. data sharing agreements, including passenger flight data
The European Parliament voted in favor of a resolution that would back the Commission should it wish to suspend data sharing agreements with the U.S., such as the passenger name records system, which the U.S. claims is vital to protecting national security. It follows revelations that the U.S. spied on millions of European citizens.
The parliament’s plenary session highlighted the strained diplomatic relationship between the EU and the U.S. over the mass surveillance revelations.
Read more: EU votes to support suspending U.S. data sharing agreements (ZDNet)

24 of 84 Elliott Brown/Flickr
July 5, 2013
France has its own PRISM system, says report
Despite concern by many European countries, according to investigative work by French newspaper Le Monde, the country has its own “local” version of the PRISM-like systems. According to the report, the French foreign intelligence agency has been intercepting metadata from phone calls, emails, and Internet activity from domestic services, as well as between France and other countries.
Just like the NSA’s version of the program, Google, Facebook, Twitter, Microsoft, Apple, and Yahoo were all named as companies the French were able to tap into.
Read more: France has its own PRISM system, says report (ZDNet)
Source: Le Monde

25 of 84 Zack Whittaker/ZDNET
July 9, 2013
NSA leaker Snowden claimed U.S. and Israel co-wrote Stuxnet virus
The Stuxnet virus, which was slated to have caused mass damage at Iran’s nuclear facilities, was co-written by the U.S. and Israel, according to additional leaks published by German media. The weaponized malware specifically targeted the facilities in order to slow down the alleged plan by the Middle Eastern country to develop a nuclear weapon. The destruction caused by the virus was slated to have set the country’s efforts back by at least 18 months.
Read more: NSA leaker Snowden claimed U.S. and Israel co-wrote Stuxnet virus (CBS News)
Image via CNET
Source: Der Spiegel

26 of 84 CNET
July 11, 2013
Microsoft accused of handing NSA access to encrypted messages; denied by software giant
The Guardian published details that pointed the finger at Microsoft as being a close collaborator with the National Security Agency, citing a document that was not published. A system exists where the NSA was able to automate the process in which orders under the FISA and the Patriot Act are issued to data-holding companies.
Among the allegations, the files provided by Snowden seem to show Microsoft helped the NSA “circumvent its encryption” to enable Web chats to be intercepted in its Hotmail replacement, Outlook.com. The report cites an NSA internal December newsletter, stating that Microsoft “developed a surveillance capability” to deal with encryption issues.
The software giant later denied the claims, stating there were “significant inaccuracies in the interpretations of leaked government documents reported in the media last week.” Microsoft said it did not “provide or agree to provide any government with direct access to user content or the ability to break our encryption.”
Read more: Microsoft accused of handing NSA access to encrypted messages (ZDNet)
Source: The Guardian

27 of 84 Zack Whittaker/ZDNET
July 16, 2013
Edward Snowden files asylum request in Russia
It wasn’t much of a surprise when Edward Snowden filed paperwork with the Russian government to request asylum away from the U.S. government. As the biggest “frenemy” to the U.S., it only further outraged the West.
According to his lawyer Anatoly Kucherena, Snowden “faces persecution by the U.S. government and he fears for his life and safety and that he could be subjected to torture and capital punishment.” But in order to save face with the Western states, Russian president Vladimir Putin warned Snowden not to further damage the country’s already tepid relationship with the U.S..
Read more: Edward Snowden files asylum request in Russia (CBS News)
Image via CBS News

28 of 84 Zack Whittaker/ZDNET
July 18, 2013
Silicon Valley tech giants urge for greater U.S. government transparency
Close to two-dozen technology giants signed a letter to the U.S. government calling for the ability to disclose secretive data request figures. While Google and others already publish “transparency reports” that disclose unclassified data requests, these companies are not allowed to disclose the full amount of National Security Letter “gagging orders” handed down by federal authorities. Instead, they are only permitted to report the number range.
The group also calls for Congress to pass laws that force the U.S. government to report these figures accurately without having to first seek permission from the FISC.
Read more: Apple, Facebook, Google, Microsoft, others urge for greater U.S. government transparency (ZDNet)
Image via Center for Democracy & Technology

29 of 84 Office of the Director of National Intelligence
July 19, 2013
Verizon’s secret data order timed to expire, but NSA spying to carry on
The very first tidbit from the ever-expanding cache of Snowden files, the Verizon court order was due to expire. But the U.S. government, despite the leaks, pushed for its renewal.
“The Government filed an application with the Foreign Intelligence Surveillance Court seeking renewal of the authority to collect telephony metadata in bulk, and that the Court renewed that authority,” the statement from the Director of National Intelligence James Clapper read. This order continues the collection of all call details — or “metadata” — of calls created by Verizon between the U.S. and abroad, or within the U.S., including local calls.
Read more: Verizon’s secret data order timed to expire, but NSA spying to carry on (ZDNet)

30 of 84 Zack Whittaker/ZDNET
July 31, 2013
U.S. spy system XKeyscore allows NSA to ‘wiretap anyone’
With billions of fragments of data collected by the U.S. and its “Five Eyes” partners around the globe annually, XKeyscore brings it all together, according to Snowden. In spite of the denials by U.S. officials over claims that the NSA could “wiretap anyone,” the new batch of slides appeared to state otherwise.
The “top secret” program allows U.S. intelligence analysts to monitor in real time the emails, web browsing, Internet searches, social media use, and virtually all online activity of a target. Based on a “massive distributed Linux cluster”, the program has 500 servers distributed around the world. In one of the slides, a map suggests these servers are located on every continent, on the territory of U.S. allies and of rivals like Russia, China, and Venezuela.
Read more: U.S. spy system XKeyscore allows NSA to ‘wiretap anyone’ (ZDNet/AAP)
Image via The Guardian
Source: The Guardian

31 of 84 Zack Whittaker/ZDNET
August 7, 2013
DOJ probing claims U.S. drug agency ‘collaborated’ with NSA on intelligence
A Reuters report claimed not long after the discovery of XKeyscore that a U.S. drug agency, outside the traditional federal intelligence arena, was being given access to NSA-gathered data for the purposes of law enforcement.
The U.S. Drug Enforcement Agency (DEA) was understood to be able to access vast amounts of data from telco giant AT&T. DEA agents were taught to “recreate” the origin of intelligence as to not blow the lid on the massive intelligence gathering operation by the NSA and its global partners.
The Justice Dept., which oversees the DEA, said it was “looking into” the matter.
Read more: DOJ probing claims U.S. drug agency ‘collaborated’ with NSA on intelligence (ZDNet)
Image via CNET
(Source: Reuters)

32 of 84 ZDNet/Lavabit
August 9, 2013
Snowden’s email provider Lavabit shuts down under U.S. government pressure
Edward Snowden’s email provider shut down, citing ongoing pressure from the U.S. government. Little was known why the shadowy service shut down, except for a short note on its website. Snowden used the service that allowed the whistleblower to communicate with others outside of work, and with journalists investigating the NSA’s reach.
The note from Lavabit founder Ladar Levison published on its website said he decided to suspend operations but said he could only wish he was able to “legally share with you the events that led to my decision.”
Read more: Snowden’s privacy-oriented email provider shuts down under U.S. government pressure (ZDNet)

33 of 84 National Security Agency
August 12, 2013
NSA hunger demands 29 petabytes of data a day
New documents released by the NSA — in efforts to appease some of the concerns over its mass surveillance operations, claimed the agency is looking at 0.00004 percent of the world’s total Internet traffic. This translates roughly into 29 million gigabytes (29 petabytes) per day, which only 0.025 percent is inspected by authorities.
But some number crunches said that with peer-to-peer discounted and other content not considered for inspection, such as television content downloading, the total inspection would account for about half the communications on the Internet.
The agency also said: “Every search into the [business record] FISA database is auditable, and all three branches of our government exercise oversight over NSA’s use of this authority.”
Read more: NSA hunger demands 29 petabytes of data a day (ZDNet)

34 of 84 Wikimedia Commons
August 13, 2013
Spain demands answers over U.S. spying claims
Spain was next to get dragged into the U.S. government surveillance controversy, after reports claimed the country also fell victim to the massive spying operation. New reports said Spain was grouped with Germany, France, Italy, and Japan in the “middle” category of where the U.S. considers its surveillance efforts should be focused.
The revelations sparked anger with the Spanish government, which subsequently sought “clarification and information” from the U.S. Embassy in Madrid.
Read more: Spain demands answers over U.S. spying claims (ZDNet)
Source: Der Spiegel

35 of 84 Zack Whittaker/ZDNET
August 15, 2013
NSA violated privacy rules thousands of times, audit finds
Additional leaked documents showed the NSA was culpable of committing serious legal violations of the Fourth Amendment. An internal audit showed serious breaches that were in some cases as a result of typos that would lead to massive unintended data collection.
The May 2012 dated audit showed there were more than 2,700 incidents in the preceding 12 months of unauthorized collection, storage, access to or distribution of legally protected communications. In one of those cases it involved the unauthorized use of data on 3,000 American citizens and green-card holders.
Read more: NSA violated privacy rules thousands of times, audit finds (CNET)
Image via The Washington Post
Source: The Washington Post

36 of 84 Zack Whittaker/ZDNET
August 19, 2013
Partner of journalist at center of NSA leak detained
More controversy stirred for the U.S. and U.K. government after the partner of Glenn Greenwald, the journalist behind The Guardian’s “NSA Files” coverage, was detained at London’s Heathrow airport for nearly nine hours.
David Miranda was held under the maximum allotted time under the U.K.’s Terrorism Act Schedule 7, which authorizes British security services to stop and detain those suspected of involved in terrorism. According to later reports, the White House was given a “heads up” on Miranda’s detention. He was suspected of carrying important and classified documents for later publication.
U.K. lawmakers and politicians later demanded an explanation for the detention of Greenwald’s partner.
Read more: Partner of journalist at center of NSA leak detained (CBS News)
Image via BBC News (video)

37 of 84 The Guardian
August 20, 2013
U.K. gov’t thought destroying Guardian hard drives would prevent NSA leaks
While intelligence may have won the British the war, the U.K. government certainly didn’t score any awards for creativity when it sent intelligence officers to the basement of The Guardian’s newsroom to destroy hard drives, which, naively and stupidly, the U.K. government thought contained the Snowden documents.
In a blog post, The Guardian editor Alan Rusbridger described in detail how officials from the U.K. government raided its offices. According to the newspaper’s editor, he was given two options: “Hand the Snowden material back or destroy it,” Rusbridger said, citing the shadowy Whitehall figure:
“You’ve had your debate. There’s no need to write any more,” they reportedly said.
Read more: U.K. gov’t thought destroying hard drives would prevent NSA leaks (ZDNet)
Source: The Guardian

38 of 84 National Security Agency
August 21, 2013
Secret court ‘troubled’ by NSA surveillance, ruled illegal
A secret U.S. court, the FISC, which authorizes wiretaps and warrantless snooping, found some of the surveillance conducted by the NSA illegal.
The court document, dated October 2011, found some of the NSA’s collections to be in breach of the constitution, which gives U.S. persons protections against unreasonable searches and seizures. In the heavily redacted opinion, the court said it was “troubled” that the government’s revelations over the NSA’s acquisition of Internet traffic was the third time in less than three years in which the government disclosed a “substantial misrepresentation” of the scope of its collection programs.
Privacy group Electronic Frontier Foundation heralded the release of the 86-page opinion as a “victory.”
Read more: Secret court ‘troubled’ by NSA surveillance, ruled illegal (ZDNet)
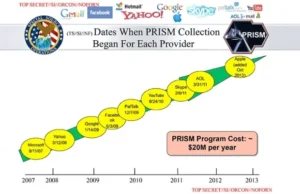
39 of 84 Zack Whittaker/ZDNET
August 23, 2013
NSA paid ‘millions’ to cover costs for tech giants in PRISM program
Following the initial PRISM leaks, which NSA slides cited the program as costing $20 million per year, Silicon Valley giants implicated in the program were further scrutinized for allegedly accepting payments from the U.S. government to cover the cost of data collection.
The latest detail points to the NSA reportedly paying “millions” of U.S. dollars out of the taxpayer’s kitty to foot the bill in covering compliance costs for the tech companies.
Read more: NSA said to have paid ‘millions’ to cover costs for tech giants in PRISM program (ZDNet)
Image via The Washington Post
Source: The Guardian

40 of 84 Zack Whittaker/ZDNET
August 29, 2013
New leaked documents detail secret U.S. intelligence ‘black budget’ figures
The secret $52.6 billion budget spent by the U.S. intelligence community is broken down for the first time, thanks to further disclosures by Snowden.
Out of the $52.6 billion, the Central Intelligence Agency (CIA), the National Security Agency (NSA), and National Reconnaissance Office (NRO) receives about two thirds of this overall figure. One of the biggest categories across the board is “data collection expenses,” which is used to fund intelligence-led operations based on information collected on companies, citizens, and foreign nationals.
Read more: New leaked documents detail secret U.S. intelligence ‘black budget’ figures (ZDNet)
Image via The Washington Post
Source: The Washington Post

41 of 84 Microsoft/U.S. Courts
August 30, 2013
Microsoft and Google to sue government over transparency
Not content with the inability to publish certain data request figures, Microsoft and Google — in a rare show of unity — said they are engaging in legal action against the U.S. government in order to disclose secret FISA court orders. By pursuing court action, the companies are hoping to be indemnified from the PRISM scandal, which they and others were named in.
Read more: Microsoft and Google to sue government over transparency (ZDNet)

42 of 84 Seth Rosenblatt/CNET
August 31, 2013
Leaked documents detail broad reach of U.S. cyberoperations
Not long after NSA chief Gen. Keith Alexander was heckled at the 2013 Black Hat conference in Las Vegas, the U.S. intelligence agency was revealed by a new round of Snowden leaks that it carried out “cyberoperations” against a number of foreign targets.
In 2011, a tight-knit group of U.S. authorities carried out 231 offensive cyberattacks, primarily targeted at Iran, Russia, North Korea, and China, according to the report. A $652 million projected, dubbed GENIE, allowed U.S. agencies to break into foreign networks to spy on operations abroad.
Read more: Leaked documents detail broad reach of U.S. cyberoperations (CNET)
Source: The Washington Post

43 of 84 Wikimedia Commons
September 2, 2013
Brazilian president, oil giant targeted by NSA spy program
Next up, it was South America’s turn. Brazilian president Dilma Rousseff was slated to be one of those picked out by the NSA for surveillance, along with her staff. It was also reported that the NSA tapped into the networks of state-owned oil company Petrobras, which would contradict the U.S.’ claim that it had nothing to do with economic espionage.
Read more: Brazilian president targeted by NSA spy program (ZDNet)
(Source: O Globo)

44 of 84 The New York Times
September 6, 2013
U.K., U.S. able to crack most encryption used online
Perhaps the most worrying claim of all to come out of the Snowden cache of leaked documents: the U.K. and U.S. governments are able to crack “most encryption” standards used online.
The two intelligence agencies, the NSA and GCHQ, used vast resources to crack standards allowing them to read data that was traveling across the wire and fiber cables in an encrypted form. They also worked to weaken security standards and insert vulnerabilities into vendors’ technologies.
It was reported that various types of security covered by BULLRUN, a program that was charged with defeating network security and privacy, cracked TLS and SSL — such as Web-based email, SSH, encrypted chat, VPN services, and even encrypted voice calls over VoIP.
Read more: U.K., U.S. able to crack most encryption used online (ZDNet)
(Source: The Guardian; The New York Times)

45 of 84 CNET
September 9, 2013
New claims NSA can access data on iOS, Android, BlackBerry
German media published new documents that stated mobile phones, including BlackBerry devices, Android phones, and Apple iPhones, were crackable and are able to have data extracted from them. According to the report, the NSA had set up “working parties’ to ensure the main mobile platforms had a “back door” available to intelligence agencies.
Later leaks would show that as a result of this vulnerability, even world leaders were not safe from prying (and spying) eyes.
Read more: New claims NSA can access data on iOS, Android, BlackBerry (ZDNet/AAP)
(Source: Der Spiegel)

46 of 84 IDF/Wikimedia Commons
September 12, 2013
NSA provides Israel with raw, unchecked U.S. intelligence
The close relationship between the U.S. and Israel is far from secret. But to what extent data is shared was outlined in further published revelations, which claimed the U.S. gives the Middle Eastern country raw, unchecked access to its collected intelligence.
The “raw” nature of the intelligence means that the data has not been filtered out to prevent Americans’ data from being inspected by the Israeli intelligence agency..
Read more: NSA provides Israel with raw, unchecked U.S. intelligence (ZDNet)
Source: The Guardian

47 of 84 StockMonkeys/Flickr
September 16, 2013
NSA snoops on credit card transactions, says report
New light was shed on the NSA’s “Follow the Money” division, which allowed the U.S. spy agency to tap into the vast amount of financial data held by Visa and other credit and debit card providers.
While Visa told German media that it was “not aware of any unauthorized access” to its networks, the NSA was still reportedly able to collate 180 million records in a secret database — with 84 percent of those records being credit card transactions.
Read more: NSA snoops on credit card transactions, says report (ZDNet)
Source: Der Spiegel

48 of 84 Wikimedia Commons
September 16, 2013
Belgacom clears up after hack attempt
The main telco in Belgium said it was dealing with the aftermath of an intrusion in its systems. The first suspect to mind was the NSA, which according to sources claimed the U.S. intelligence agency has been hacking into the telephone and Internet provider since early 2011.
Not long after and not far along the European western coast, three Dutch ministers said they had “no evidence” to suggest that major Internet provider in The Netherlands, KPN, was targeted by foreign intelligence agencies.
Read more: Belgacom clears up after hack attempt (ZDNet)
(Source: Belgacom; De Standard)

49 of 84 National Security Agency
September 17, 2013
U.S. secret surveillance court rules phone metadata collection lawful
Another blow for civil liberties as the U.S. secret court that authorized massive data collection — and in some cases ruled its activities “illegal” — upheld the NSA’s bulk metadata collection program as ultimately within the bounds of law.
The judges in the FISC said there is “no Constitutional impediment to the requested production” of metadata from phone companies order to hand over “all tangible things” under Section 215 of the Patriot Act.
Aware of the public’s reaction to the Snowden disclosures, the court’s opinion was declassified in a bid to allay fears of lack of transparency within the secret court.
Read more: U.S. secret surveillance court rules phone metadata collection lawful (ZDNet)

50 of 84 Zack Whittaker/ZDNET
September 18, 2013
NSA purchased zero-day exploits from French security firm Vupen
A new report, thanks to a Freedom of Information request by government transparency site MuckRock showed that the U.S. government bought zero-day vulnerabilities and the software to use them from French security company Vupen.
Vupen, which describes itself as a “leading provider of defensive and offensive cyber security intelligence and advanced vulnerability research,” essentially finds flaws in software and systems and then sells this data on to governments.
Read more: NSA purchased zero-day exploits from French security firm Vupen (ZDNet)
Image via CBS News (video)
(Source: MuckRock)

51 of 84 CNET/Scribd
September 27, 2013
NSA offers details on ‘LOVEINT’ (that’s spying on lovers, exes)
It’s not surprising that when NSA analysts are given access to vast amounts of American and foreign personal information, there might a chance they might misuse it for their own personal gain.
The latest, albeit not-as-shocking revelation, was that a handful of NSA staffers misused their security clearance to access data on their lovers and partners. Dubbed LOVEINT, or “love intelligence,” there were 12 substantiated instances of intentional misuse of signals intelligence at the NSA — compared to an average of seven per day of “inadvertent” mistakes, such as the collection of American data.
Read more: NSA offers details on ‘LOVEINT’ (that’s spying on lovers, exes) (CNET)
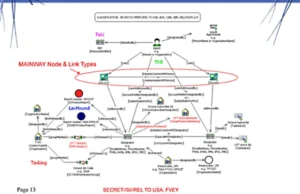
52 of 84 The New York Times
September 28, 2013
NSA maps some Americans’ social connections, says report
Facebook may be for yourself and your friends, but it’s also very much for the NSA. More documents leaked by Snowden said the intelligence agency had created “social graphs” of Americans in efforts to “rapidly discover and correlate complex relationships and patterns across diverse data sources on a massive scale.”
According to the documents, 94 types of data are included, such as phone numbers, email addresses, and IP address details. Other data is pulled in from other sources, such as passenger name records (gathered domestically and from the European Union under existing agreements), voter registration rolls, tax info, GPS location data, bank codes, insurance information, and even Facebook profiles.
Read more: NSA maps some Americans’ social connections, says report
Source: The New York Times

53 of 84 CNET
September 30, 2013
Verizon: ‘No comment’ on FISA court challenge
While Verizon remains mum on challenging any secret U.S. court order that authorizes the mass vacuuming of U.S. and international data, a growing number of technology firms called on Congress for greater transparency and data request reporting.
Foursquare, Twilio, and Automattic — the creator of WordPress.com — have added their names to a list, joining Apple, CloudFlare, Dropbox, Facebook, Google, LinkedIn, Twitter, and Yahoo, among others, calling on Congress for greater transparency surrounding secret government data requests for customer and user information.
Read more: Verizon: ‘No comment’ on FISA court challenge (ZDNet)

54 of 84 Zack Whittaker/ZDNET
October 1, 2013
NSA stores metadata on innocent web users for a year, according to new leaks
Exactly how long the NSA holds your data for was previously unknown. That is until a new leaked report confirmed that should your Internet data fall within the scope of the NSA’s massive data collection dragnet, the intelligence agency will hold it for up to a year. According to the media reports, the protocol was to allow the U.S. government to find information on people who may be innocent today, but may become criminal suspects later.
Read more: NSA stores metadata on innocent web users for a year, according to new leaks (ZDNet)
Image via The Guardian
Source: The Guardian
![]()
55 of 84 White House
October 2, 2013
NSA ran secret test on tracking Americans’ cell phones
The NSA, not content with its ever-expanding surveillance capabilities, was reportedly “testing” location tracking. The news came not from the Snowden leaks, but the U.S. Director of National Intelligence James Clapper.
Clapper described the test: “In 2010 and 2011 NSA received samples [of location data] in order to test the ability of its systems to handle the data format, but that data was not used for any other purpose and was never available for intelligence analysis purposes.” But the NSA hadn’t yet sought approval from the FISA court. That, he said, would come later.
Read more: NSA ran secret test on tracking Americans’ cell phones
Source The New York Times; Politico

56 of 84 U.S. Courts/Lavabit
October 3, 2013
Unsealed docs show what really happened with Lavabit
In October, the reason behind Lavabit’s shutdown became clear. While at the time he could not “legally share with you the events that led to my decision,” the formerly sealed court order showed that secure email service owner Ladar Levison was forced to hand over the encryption keys behind the site. This would have given the federal authorities wide-ranging access to vast amounts of customer data. Levison was gagged from disclosing the court order to anyone.
Read more: Unsealed docs show what really happened with Lavabit (ZDNet)
Source: Wired
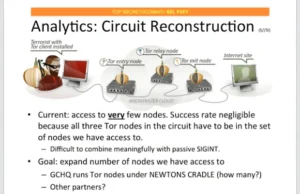
57 of 84 Zack Whittaker/ZDNET
October 4, 2013
NSA, GCHQ target Tor user to crack encrypted ‘dark Web’
Enter yet another codename — perhaps the strangest to date — EGOTISTICAL GIRAFFE. New leaks showed how the American and British spy agencies have put together their resources to crack the “dark Web,” otherwise known as Tor.
The encrypted, anonymous network may be part-funded by the U.S. Defense Dept. and the U.S. State Dept., but it’s regular use by privacy-conscious users was enough to concern the NSA and GCHQ. While the intelligence agencies haven’t been able to crack Tor outright, they have been able to “de-anonymize a very small fraction of Tor users,” according to the documents.
Read more: NSA sought to unmask users of Net-privacy tool Tor (CNET)
Image via The Guardian
Source: The Guardian

58 of 84 Dept. of Justice
October 4, 2013
U.S. gov’t argues tech companies should not be allowed to report data request figures
Amid the ongoing battle of words between the U.S. government and the Silicon Valley giants, the latest round saw the Justice Dept. claim in a filing with the secretive FISA court that technology firms should not be allowed to disclose how many requests it makes to technology companies holding user data.
It argued that the decision to classify requests made under the Foreign Intelligence Surveillance Act (FISA) would “undermine the secrecy of the surveillance.”
Read more: U.S. gov’t argues tech companies should not be allowed to report data request figures (ZDNet)

59 of 84 Australian Government
October 7, 2013
Australian government briefed on PRISM before Snowden leaks
More from the Five Eyes: this time Australia. Documents released under the country’s Freedom of Information laws show that the Australian Attorney-General prepared a briefing for the minister on the secret NSA spying program PRISM more than two months before information about the program was leaked in June.
Read more: Australian government briefed on PRISM before Snowden leaks
(Source: ABC)

60 of 84 Microsoft
October 11, 2013
Skype faces fines in Luxembourg probe over NSA links
Luxembourg-based Skype, which was implicated in the PRISM surveillance scandal, is under investigation by the country’s data protection officials over its connections to the U.S. intelligence agency.
The Microsoft-owned company could face administrative and criminal sanctions in the country, which may include a ban on secretly handing data over to the U.S. government. That is, however, unless it is uncovered that Luxembourg’s judiciary didn’t sanction it in the first place.
Read more: Skype faces fines in Luxembourg probe over NSA links (…only if the courts didn’t sanction it first) (ZDNet)
Source: The Guardian

61 of 84 Deutsche Telekom
October 14, 2013
Deutsche Telekom to foreign secret services: ‘Eyes off our internet!’
Germany’s telco giant Deutsche Telekom spearheaded efforts to keep local Internet traffic inside the country following the spate of leaks that left German citizens vulnerable to U.S. snooping. The company said it found it “deeply frustrating” that it didn’t know to what extent its networks were being monitored by foreign secret services.
The plan would essentially help keep user data within the country. Exactly how the company plans to do this remain on the most part unclear.
Read more: Deutsche Telekom to foreign secret services: ‘Eyes off our internet!’ (ZDNet)

62 of 84 Zack Whittaker/ZDNET
October 15, 2013
NSA, Australian intelligence agencies rifle through users’ address books
New PRISM slides were released outlining the scope and scale of data collection of personal information. It was reported that the NSA is vacuuming up email and instant message address books that are sent around the Internet. The fresh leak shows U.S. and Australian intelligence agencies have targeted the address books belonging to users of Yahoo, Hotmail, Gmail, and Facebook. This data is stored across multiple government-owned databases.
It also came at a time when, amid earlier reports the intelligence agency takes in about 29 petabytes of data each day, the NSA has a “spam” issue.
Read more: NSA, Australian intelligence agencies rifle through users’ address books (ZDNet)
Image via The Washington Post
Source: The Washington Post

63 of 84 Dept. of Defense/YouTube
October 17, 2013
NSA director Keith Alexander to stand down
Just four months after the surveillance scandal broke in June, the NSA announced its director Gen. Keith Alexander would leave the agency and his deputy John Inglis will retire. However, the agency was keep to stress that Alexander’s departure had nothing to do with the recent media attention over allegations that the NSA was engaged in unlawfully spying on U.S. and foreign citizens.
Read more: NSA director Keith Alexander to stand down (ZDNet)
Source: Reuters

64 of 84 European Union
October 21, 2013
NSA reportedly spied on Mexican President’s emails
Next in line to face the NSA’s snooping powers is Mexico’s president Felipe Calderon, whose email account was reportedly breached by the U.S. government.
The NSA’s Tailored Access Operations (TAO) division was successful in compromising an email server within the Mexican presidential network. Cabinet members were also reportedly affected by the breach. The NSA said in the slides it now has access to “diplomatic, economic, and leadership communications.
Read more: NSA reportedly spied on Mexican President’s emails (ZDNet)
Source: Der Spiegel

65 of 84 European Parliament/Flickr
October 21, 2013
EU lawmakers OK beefing up data protection laws
European Parliament members approved new data protection rules that outlaw data transfers to the U.S. that could be used for surveillance purposes. After 18 months of lobbying and negotiations, the Civil Liberties Committee voted almost unanimously to adopt the motion.
The rules will replace outdated legislation that has been in effect for more than 15 years, and not protected against unlawful third-country transfers of European citizen data.
Read more: EU lawmakers OK beefing up data protection laws (CBS News)

66 of 84 U.S. Dept. of State
October 24, 2013
Merkel to Obama: Are you tapping my phone?
The aftermath of the spying scandal in Germany percolated all the way to the top of the country’s political elite. Chancellor Angela Merkel called U.S. President Barack Obama to seek assurances that the U.S. government did not tap her phone. Merkel, a heavy mobile phone user, said should the reassurances be false or inaccurate, it would be “completely unacceptable” for allies to be spying on their friends.
Read more: Merkel to Obama: Are you tapping my phone? (ZDNet)

67 of 84 U.S. Embassy in Berlin
October 24, 2013
Merkel wasn’t alone: NSA tapped calls of 35 world leaders
The same day as the White House made reassurances to the German government’s leader, new leaks appeared to disprove what the U.S. had initially claimed, specifically that it wasn’t tapping into the phones of world leaders. According to the new reports, more than 200 phone numbers were handed over by a U.S. official, including almost three-dozen numbers belonging to prime ministers, presidents, and heads of state.
But the surveillance turned up “little reportable intelligence” on the 35 world leaders whose phones were tapped into by the U.S., the documents showed.
Read more: Merkel wasn’t alone: NSA tapped calls of 35 world leaders (ZDNet)
(Source: The Guardian)

68 of 84 Zack Whittaker/ZDNET
October 28, 2013
Japan reportedly rejected NSA requests to tap fiber in 2011
In efforts to expand the U.S. government’s surveillance program to the Asian states, particularly with China set in its sights, the U.S. made efforts to ask Japan if it would allow the tapping of undersea fiber cables. But Japan refused, according to sources speaking to Japanese media.
The report said legislation preventing the intercepting of communications in the country forced the Japanese government to refuse the request — even if it meant missing out on collecting the communications of suspected terrorists.
Read more: Japan reportedly rejected NSA requests to tap fiber in 2011 (ZDNet/AAP)
Image via CNET
Source: The Japan Times

69 of 84 European Union
October 30, 2013
NSA accused of tapping links between Yahoo, Google datacenters
The next big leak from the Snowden files was the revealing of a new NSA project, codenamed MUSCULAR, which suggests the U.S. spy agency was tapping into the links between Google and Yahoo datacenters worldwide, including Americans’ data.
The U.S. also works with its British counterparts at GCHQ to intercept cables that span across the Atlantic.
Data, which is sapped from the private optical cables between the technology giants’ datacenters, is siphoned off and sent back to the agency’s Fort Meade headquarters. In the preceding 30 days, the agency collected 181 million new records alone, including metadata — such as traffic records and details relating to customer data — as well as the contents of communications.
Read more: Meet ‘Muscular’: NSA accused of tapping links between Yahoo, Google datacenters (ZDNet)
Source: The Washington Post

70 of 84 Wikimedia Commons
October 31, 2013
NSA hid spy equipment at embassies, consulates
Another revelation that focuses more on the diplomatic side of snooping than the wider civilian population, new documents show the NSA hid surveillance equipment at its embassies and consulates abroad.
The NSA’s Special Collection Service dubbed the program STATEROOM, which allows the agency to monitor microwave, Wi-Fi, WiMAX, GSM, CDMA, and satellite signals in over 80 worldwide. The spy equipment is located at the U.S., the U.K., Canadian and Australian embassies and consulates in various major cities.
In some cases, the buildings are modified to conceal such rooftop equipment. “For example, antennas are sometimes hidden in false architectural features or roof maintenance sheds,” the documents state.
Read more: NSA hid spy equipment at embassies, consulates (ZDNet/AAP)
Source: Der Spiegel

71 of 84 Wikimedia Commons
November 4, 2013
Google’s Eric Schmidt calls NSA’s spying ‘outrageous’
In an interview with The Wall Street Journal, Google executive chairman Eric Schmidt called the NSA’s spying operation — specifically the agency’s ability to acquire data between its datacenters — as “outrageous.”
It follows earlier leaks that showed project MUSCULAR was able to tap into connections between Google and Yahoo’s global datacenters. Schmidt also called the allegations that the intelligence agency may have acted illegally, by “collect[ing] the phone records of every phone call of 320 million people in order to identify roughly 300 people who might be a risk.”
Read more: Google’s Eric Schmidt calls NSA’s spying ‘outrageous’ (CNET)
Source: The Wall Street Journal

72 of 84 Wikimedia Commons
November 5, 2013
Apple defends government-mandated gaps in new transparency report
For the first time, Apple published a transparency report, akin to the reports published by other Silicon Valley giants. The company wanted to distance itself from the U.S. government in the wake of the NSA scandal.
The company was keen to stress, aside from the reported numbers, that its business does not rely on collecting personal information. It also lashed out at the government for not allowing it to disclose the full figures. Interestingly, Apple also included a “warrant canary” by stating it had never received an order under Section 215 of the Patriot Act. Should that change, the company will not be allowed to report it, thus indicating to the world that it is in fact under such an order.
Read more: Apple defends government-mandated gaps in new transparency report (ZDNet)

73 of 84 Wikimedia Commons
November 8, 2013
Germany brings anti-spying bill to the UN, meets with U.S. intelligence
Following the news that the U.S. government spied on Germany’s executive branch, the European federal state filed a draft resolution calling for the United Nations to address electronic surveillance. The efforts were part of a global bid to restore lost trust between various governments around the world, particularly in Germany where World War II memories of the Stasi remain raw for many.
Read more: Germany brings anti-spying bill to the UN, meets with U.S. intelligence

74 of 84 LinkedIn via CNET
November 11, 2013
GCHQ used fake LinkedIn pages to target engineers
More from Belgium and the hack on its main telco Belgacom, which appeared implicated the NSA directly in the unauthorized access. German media reported new documents from Snowden that said, with the U.K.’s help, turned fake LinkedIn and Slashdot.org pages — a site popular in the IT community — into honeypots for installing malware on machines belonging to Belgacom engineers.
Dubbed QUANTUM INSERT, it allowed British intelligence to spy deep within the Belgian network. The news came just days after officials from the three British intelligence branches, MI5, MI6, and GCHQ, were called before a U.K. parliamentary committee to explain their actions to lawmakers.
Read more: GCHQ used fake LinkedIn pages to target engineers (Der Spiegel)

75 of 84 Seth Rosenblatt/CNET
November 14, 2013
CIA collects global data on transfers of money
The U.S. Central Intelligence Agency’s (CIA) role in the surveillance scandal has been mostly muted. Now, according to two reports by U.S. media, the CIA is able to acquire vast amounts of financial data and money transfer information handled by U.S. companies, in efforts to track terrorist funding activities.
Operating under the same provisions of the Patriot Act that the NSA uses to acquire data, it’s not explicitly clear if Americans’ data was collected and inspected by the spy agency. It’s expected further Snowden leaks will reveal far more about the system.
Read more: CIA collecting bulk data on money transfers, reports say (CNET)
Source: The Wall Street Journal; The New York Times

76 of 84 Expedia/Intercontinental
November 17, 2013
Snowden cache reveals diplomats’ hotel bookings being tracked by GCHQ
In a perhaps bizarre twist, British agents at GCHQ are slated to have bugged around 350 hotels around the world used by diplomats in order to get the inside track of what foreign governments are talking about behind closed doors.
Under the program dubbed ROYAL CONCIERGE, the program has been in operation since 2010. The program also monitors hotel-booking systems that allow the U.K. and U.S. governments to keep tabs on where diplomats are heading. The names of the hotels were not released, but documents seen by Der Spiegel said telephones, computers, and fax machines in hotel rooms were bugged and wiretap-enabled.
Read more: Snowden cache reveals diplomats’ hotel bookings being tracked by GCHQ (The Guardian)
Source: Der Spiegel

77 of 84 White House/Flickr
November 19, 2013
FISA court order that allowed NSA surveillance is revealed for first time
The secret FISA court, which authorizes U.S. government surveillance actions, released on the instructions of U.S. intelligence community chief James Clapper a legal opinion that allowed the NSA to collect even more data on Americans, despite finding the agency exceeding its powers and capabilities.
Even though one of the FISA judges recounted a number of problems with the smaller NSA programs, wider scale programs were nonetheless approved. According to the documents, metadata — the information around messages but not the messages themselves, did not enjoy Fourth Amendment protections
Read more: FISA court order that allowed NSA surveillance is revealed for first time (The Guardian)

78 of 84 Zack Whittaker/ZDNET
November 20, 2013
U.S. and U.K. struck secret deal with U.K. to monitor British citizen data
Fresh information suggested what the NSA was telling the Brits might not have been all it was letting on. According to the Snowden-leaked documents, the “Five Eyes” group of countries, including the two superpowers, Canada, Australia, and New Zealand, may not have been as binding as first thought.
A 2005 secret draft directive said the NSA could spy on its allies without informing them — though, it’s not clear if it was ever enacted. A 2007 NSA memo provided, according to The Guardian, the “first explicit confirmation” that Brits were caught up in the U.S. surveillance dragnet.
Read more: NSA’s BFFs not necessarily immune to spying eyes (CNET)
Image via The Guardian
Source: The Guardian
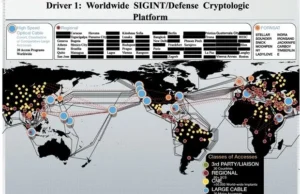
79 of 84 Zack Whittaker/ZDNET
November 23, 2013
NSA malware infected over 50,000 computer networks worldwide
The NSA infected more than 50,000 computer networks worldwide with malware, according to new slides leaked by Snowden to Dutch media outlet NRC. A presentation dated 2012 showed a spiderweb map dubbed “Computer Network Exploitation,” citing more than 50,000 locations globally.
The division of the intelligence agency, Tailored Access Operations (TAO), describes the operation in which includes, “enabling actions and intelligence collection via computer networks that exploit data gathered from target or enemy information systems or networks.”
Read more: NSA malware infected over 50,000 computer networks worldwide (ZDNet)
Image via NRC
Source: NRC

80 of 84 Malaysian Government
November 25, 2013
U.S. hooks Singapore, South Korea as players in “Five Eyes” pact
Reports in Australian media cited new documents leaked by Snowden that point to Singapore and South Korea as playing “key roles” in helping the U.S. and Australia, two members of the so-called “Five Eyes” pact of spying partners, to tap into other South Asian countries.
The map, leaked by Dutch media earlier in November, showed Singapore as a key telecoms hub in the Pacific region, as an important “third party” working with its U.S. partners. The operation helps the U.S. and other allied nations tap into the communications of other countries in the region, notably Indonesia and Malaysia.
Read more: Singapore, Seoul key players in ‘Five Eyes’ spy ring (ZDNet)
Source: Sydney Morning Herald

81 of 84 European Commission
November 27, 2013
EU lays out new U.S. data agreement pact
In efforts to get the “special relationship” back on track after months of painful political rhetoric and frenemy-like relations, the European Commission wants to rekindle its trans-Atlantic love with its American partners.
The EU on Wednesday threw down its demands — albeit in a somewhat subdued typical softly-softly European way now that the 28 member state bloc has taken time to breathe and think this one through — and hopes its U.S. counterparts bites at the chance to restore relations with its trans-Atlantic friend.
This includes new rules to Safe Harbor, which would force companies, like the seven named technology companies implicated under the data-acquiring PRISM program, to extend the rules of Safe Harbor, by adjusting their privacy policies. This would result in the disclosure of “information on the extent to which U.S. law allows public authorities to collect and process data transferred.”
Read more: Realizing it’s the underdog post-PRISM, EU lays out new BFF pact with the U.S. (ZDNet)

82 of 84 Cryptome
December 2, 2013
Australian government willing to share uncensored citizen data
The Australian Signals Directorate — or Defence Signals Directorate (DSD), as it was known in 2008 — was said to be able to share “bulk, unselected, un-minimised metadata, as long as there is no intent to target an Australian national — unintentional collection is not viewed as a significant issue”.
This metadata was handed to other governments of the “Five Eyes” group — the U.S., the U.K., Canada, and New Zealand.
The Australian government recorded 183,099 authorisations from government departments to access metadata from Australian telecommunications companies. In 2011-12, authorisations for metadata access rose to 293,501.
Read more: Australian government willing to share uncensored citizen data (ZDNet)
Source: The Guardian

83 of 84 BBC Parliament (live stream
December 3, 2013
Guardian newspaper may face U.K. terror charges over Snowden leaks
The editor of The Guardian, Alan Rusbridger, was summoned to give testimony to a U.K. parliamentary committee in early December.
Aside from the questioning, British police are looking to see whether or not the London-based newspaper broke any laws in regards to the detention of then-Guardian columnist’s Glenn Greenwald’s partner, David Miranda, earlier this year.
Rusbridger also told lawmakers under oath that the paper had published only 1 percent of the total cache of leaked documents provided by Snowden.
Read more: British news staff may face terrorism charges over Snowden leaks (Reuters)
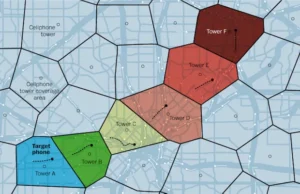
84 of 84 The Washington Post
December 4, 2013
NSA collects 5 billion cell location records a day
The U.S. National Security Agency is gathering close to 5 billion records a day on cellular devices around the world, allowing the agency to track individual’s movements.
New leaks provided to The Washington Post, the records flow into a vast database that can store the location of “at least hundreds of millions of devices,” according to the documents.
The NSA is understood to keep about 1 percent of the records — some 27 terabytes, according to the documents.
Read more: NSA collects 5 billion cell location records a day, Snowden leaks say (ZDNet)
X. Total Information Awareness (TIA)
The Department of Homeland Security (DHS) will be given access to all state and local databases, complete access to all banking and stock transactions, and all private data bases on demand (medical records). They will monitor and control all communications at state and local levels, as well as build an intranet for corporations. Local police agencies that receive federal subsidies (all of them), will in effect become intelligence gathering units for the federal government.
Under the TIA program created by DARPA the government is now monitoring almost all activity of all Americans, including bank deposits, shopping, web surfing, academic grades, divorce records, spending, phone calls, utility usage, travel, virtually everything. It plans to track everything you do employing face recognition software that can stop you from making a withdrawal at the bank or from boarding a plane. The government has placed all its faith in incredible new technologies such as PROMIS software and exotic weaponry systems that are just beginning to be unveiled. TIA plans to recognize you by your voice, by your unique body odor, it even plans to use “non-invasive neuroelectric sensors” to read your mind. (Washington Times 8/17/02 (1)
XI. Palantir Technologies (from wikipedia)
Founded 2003; 19 years ago
Founders: Peter Thiel, Nathan Gettings, Joe Lonsdale, Stephen Cohen, Alex Karp
Headquarters: Denver, Colorado, U.S.[1]
Key people: Peter Thiel (Chairperson), Alex Karp (CEO), Shyam Sankar (COO)
Products: Palantir Gotham, Palantir Foundry, Palantir Apollo
Revenue Increase US$1.541 billion (2021)a
Operating income
Increase US$-488.494 million (2021)a
Net income
Increase US$-520.379 million (2021)a
Total assets Increase US$3.247 billion (2021)a
Total equity Increase US$2.291 billion (2021)a
Number of employees
Increase 2,920 (2021)a
Website palantir.com
Palantir Technologies is a public American software company that specializes in big data analytics. Headquartered in Denver, Colorado, it was founded by Peter Thiel,[3] Nathan Gettings, Joe Lonsdale, Stephen Cohen, and Alex Karp in 2003. The company’s name is derived from The Lord of the Rings where the magical palantíri were “seeing-stones,” described as indestructible balls of crystal used for communication and to see events in other parts of the world.
The company is known for three projects in particular: Palantir Gotham, Palantir Apollo, and Palantir Foundry. Palantir Gotham is used by counter-terrorism analysts at offices in the United States Intelligence Community (USIC) and United States Department of Defense.[4] In the past, Gotham was used by fraud investigators at the Recovery Accountability and Transparency Board, a former US federal agency which operated from 2009 to 2015. Gotham was also used by cyber analysts at Information Warfare Monitor, a Canadian public-private venture which operated from 2003 to 2012. Palantir Apollo is the operating system for continuous delivery and deployment across all environments.[5] Their SaaS is one of five offerings authorized for Mission Critical National Security Systems (IL5) by the U.S. Department of Defense.[6][7] Palantir Foundry is used by corporate clients such as Morgan Stanley, Merck KGaA, Airbus, Wejo, Lilium, and Fiat Chrysler Automobiles.[8]
Palantir’s original clients were federal agencies of the USIC. It has since expanded its customer base to serve state and local governments, as well as private companies in the financial and healthcare industries.[9]
Contents
1 History
1.1 2003–2008: Founding and early years
1.2 2009: GhostNet and the Shadow Network
1.3 2010–2012: Expansion
1.4 2013–2016: Additional funding
1.5 2020
1.6 Valuation
1.7 Investments
2 Products
2.1 Palantir Gotham
2.2 Palantir Metropolis
2.3 Palantir Apollo
2.4 Palantir Foundry
2.5 Other
3 Customers
3.1 Corporate use
3.2 U.S. civil entities
3.3 U.S. military, intelligence, and police
3.4 International Atomic Energy Agency
3.5 Europe
4 Partnerships and contracts
4.1 International Business Machines
4.2 Amazon (AWS)
4.3 Babylon Health
5 Controversies
5.1 Algorithm development
5.2 WikiLeaks proposals (2010)
5.3 Racial discrimination lawsuit (2016)
5.4 British Parliament inquiry (2018)
5.5 ICE partnership (since 2014)
5.6 “HHS Protect Now” and privacy concerns (since 2020)
5.7 Project Maven (since 2018)
6 See also
7 References
8 External links
History
2003–2008: Founding and early years
Founder and chairman Peter Thiel was Palantir’s largest shareholder as of late 2014.
Though usually listed as having been founded in 2004, SEC filings state Palantir’s official incorporation to be in May 2003 by Peter Thiel (co-founder of PayPal), who named the start-up after the “seeing stone” in Tolkien’s legendarium.[9] Thiel saw Palantir as a “mission-oriented company” which could apply software similar to PayPal’s fraud recognition systems to “reduce terrorism while preserving civil liberties.”[10]
In 2004, Thiel bankrolled the creation of a prototype by PayPal engineer Nathan Gettings and Stanford University students Joe Lonsdale and Stephen Cohen. That same year, Thiel hired Alex Karp, a former colleague of his from Stanford Law School, as chief executive officer.[11]
Headquartered in Palo Alto, California, the company initially struggled to find investors. According to Karp, Sequoia Capital chairman Michael Moritz doodled through an entire meeting, and a Kleiner Perkins executive lectured the founders about the inevitable failure of their company.[12] The only early investments were $2 million from the U.S. Central Intelligence Agency’s venture capital arm In-Q-Tel, and $30 million from Thiel himself and his venture capital firm, Founders Fund.[6][7][13][14][15]
Palantir developed its technology by computer scientists and analysts from intelligence agencies over three years, through pilots facilitated by In-Q-Tel.[16][6] The company stated computers alone using artificial intelligence could not defeat an adaptive adversary. Instead, Palantir proposed using human analysts to explore data from many sources, called intelligence augmentation.[17]
2009: GhostNet and the Shadow Network
In 2009 and 2010 respectively, Information Warfare Monitor used Palantir software to uncover the GhostNet and the Shadow Network. The GhostNet was a China-based cyber espionage network targeting 1,295 computers in 103 countries, including the Dalai Lama’s office, a NATO computer and various national embassies.[18] The Shadow Network was also a China-based espionage operation that hacked into the Indian security and defense apparatus. Cyber spies stole documents related to Indian security and NATO troop activity in Afghanistan.[19][20]
2010–2012: Expansion
In April 2010, Palantir announced a partnership with Thomson Reuters to sell the Palantir Metropolis product as “QA Studio” (a quantitative analysis tool).[21] On June 18, 2010, Vice President Joe Biden and Office of Management and Budget Director Peter Orszag held a press conference at the White House announcing the success of fighting fraud in the stimulus by the Recovery Accountability and Transparency Board (RATB). Biden credited the success to the software, Palantir, being deployed by the federal government.[22] He announced that the capability will be deployed at other government agencies, starting with Medicare and Medicaid.[23][24][25][26]
Estimates were $250 million in revenues in 2011.[27]
2013–2016: Additional funding
“[As of 2013] the U.S. spy agencies also employed Palantir to connect databases across departments. Before this, most of the databases used by the CIA and FBI were siloed, forcing users to search each database individually. Now everything is linked together using Palantir.”
— TechCrunch in January 2015[28]
A document leaked to TechCrunch revealed that Palantir’s clients as of 2013 included at least twelve groups within the U.S. government, including the CIA, the DHS, the NSA, the FBI, the CDC, the Marine Corps, the Air Force, the Special Operations Command, the United States Military Academy, the Joint Improvised-Threat Defeat Organization and Allies, the Recovery Accountability and Transparency Board and the National Center for Missing and Exploited Children. However, at the time, the United States Army continued to use its own data analysis tool.[28] Also, according to TechCrunch, the U.S. spy agencies such as the CIA and FBI were linked for the first time with Palantir software, as their databases had previously been “siloed.”[28]
In September 2013, Palantir disclosed over $196 million in funding according to a U.S. Securities and Exchange Commission filing.[29][30] It was estimated that the company would likely close almost $1 billion in contracts in 2014.[31] CEO Alex Karp announced in 2013 that the company would not be pursuing an IPO, as going public would make “running a company like ours very difficult.”[32] In December 2013, the company began a round of financing, raising around $450 million from private funders. This raised the company’s value to $9 billion, according to Forbes, with the magazine further explaining that the valuation made Palantir “among Silicon Valley’s most valuable private technology companies.”[32]
In December 2014, Forbes reported that Palantir was looking to raise $400 million in an additional round of financing, after the company filed paperwork with the Securities and Exchange Commission the month before. The report was based on research by VC Experts. If completed, Forbes stated Palantir’s funding could reach a total of $1.2 billion.[32] As of December 2014, the company continued to have diverse private funders, Ken Langone and Stanley Druckenmiller, In-Q-Tel of the CIA,[33] Tiger Global Management, and Founders Fund, which is a venture Firm operated by Peter Thiel, the chairman of Palantir. As of December 2014, Thiel was Palantir’s largest shareholder.[32]
The company was valued at $15 billion in November 2014.[34] In June 2015, BuzzFeed reported the company was raising up to $500 million in new capital at a valuation of $20 billion.[35] By December 2015, it had raised a further $880 million, while the company was still valued at $20 billion.[36] In February 2016, Palantir bought Kimono Labs, a startup which makes it easy to collect information from public facing websites.
In August 2016, Palantir acquired data visualization startup Silk.[37]
2020
Palantir is one of four large technology firms[38] to start working with the NHS on supporting COVID-19 efforts through the provision of software from Palantir Foundry[39] and by April 2020 several countries have used Palantir technology to track and contain the contagion.[40] Palantir also developed Tiberius, a software for vaccine allocation used in the United States.[41]
In December 2020, Palantir was awarded a $44.4 million contract by the U.S. Food and Drug Administration, boosting its shares by about 21%.[42]
Valuation
The company was valued at $9 billion in early 2014, with Forbes stating that the valuation made Palantir “among Silicon Valley’s most valuable private technology companies”.[32] As of December 2014, Thiel was Palantir’s largest shareholder.[32] In January 2015, the company was valued at $15 billion after an undisclosed round of funding with $50 million in November 2014.[43] This valuation rose to $20 billion in late 2015 as the company closed an $880 million round of funding.[44] Palantir has never reported a profit. In 2018, Morgan Stanley valued the company at $6 billion.[45]
Karp, Palantir’s chief executive officer, announced in 2013 that the company would not pursue an IPO, as going public would make “running a company like ours very difficult”.[32] However, on October 18, 2018, the Wall Street Journal reported that Palantir was considering an IPO in the first half of 2019 following a $41 billion valuation.[46] In July 2020, it was revealed the company had filed for an IPO.[47]
It ultimately went public on the New York Stock Exchange through a direct public offering on September 30, 2020 under the ticker symbol “PLTR”.[48]
Investments
The company has invested over $400 million into nearly two dozen SPAC targets according to investment bank RBC Capital Markets, while bringing alongside those companies as customers.[49]
Products
Palantir Gotham
Palantir Gotham is Palantir’s government offering. It is an evolution of Palantir’s longstanding work in the United States Intelligence Community. More recently, Palantir Gotham has been used as a predictive policing system, which has elicited some controversy over racism in their AI analytics.[50]
Palantir Metropolis
Palantir Metropolis (formerly known as Palantir Finance) was[51][52] software for data integration, information management and quantitative analytics. The software connects to commercial, proprietary and public data sets and discovers trends, relationships and anomalies, including predictive analytics.[53][54] Aided by 120 “forward-deployed engineers” of Palantir during 2009, Peter Cavicchia III of JPMorgan used Metropolis to monitor employee communications and alert the insider threat team when an employee showed any signs of potential disgruntlement: the insider alert team would further scrutinize the employee and possibly conduct physical surveillance after hours with bank security personnel.[53][54] The Metropolis team used emails, download activity, browser histories, and GPS locations from JPMorgan owned smartphones and their transcripts of digitally recorded phone conversations to search, aggregate, sort, and analyze this information for any specific keywords, phrases, and patterns of behavior.[53][54] In 2013, Cavicchia may have shared this information with Frank Bisignano who had become the CEO of First Data Corporation.[53]
Palantir Apollo
Palantir Apollo is a continuous delivery system that manages and deploys Palantir Gotham and Foundry.[55] Apollo was built out of the need for customers to use multiple public and private cloud platforms as part of their infrastructure. Apollo orchestrates updates to configurations and software in the Foundry and Gotham platforms using a micro-service architecture. This product allows Palantir to provide software as a service (SaaS) rather than to operate as a consulting company.[56]
Palantir Foundry
Palantir Foundry was used by NHS England in dealing with the COVID-19 pandemic in England to analyse the operation of the vaccination programme. A campaign was started against the company in June 2021 by Foxglove, a tech-justice nonprofit, because “Their background has generally been in contracts where people are harmed, not healed.” Clive Lewis MP, supporting the campaign said Palantir had an “appalling track record.”[57]
Other
The company has been involved in a number of business and consumer products, designing in part or in whole. For example, in 2014, they premiered Insightics, which according to the Wall Street Journal “extracts customer spending and demographic information from merchants’ credit-card records.” It was created in tandem with credit processing company First Data.[58]
Customers
Corporate use
See also: Information Warfare Monitor
Palantir Metropolis is used by hedge funds, banks, and financial services firms.[6][7][19][59]
Palantir Foundry clients include Merck KGaA,[60] Airbus[61] and Ferrari.[62]
Palantir partner Information Warfare Monitor used Palantir software to uncover both the Ghostnet and the Shadow Network.[19][63][20]
U.S. civil entities
Palantir’s software is used by the Recovery Accountability and Transparency Board to detect and investigate fraud and abuse in the American Recovery and Reinvestment Act. Specifically, the Recovery Operations Center (ROC) used Palantir to integrate transactional data with open-source and private data sets that describe the entities receiving stimulus funds.[clarification needed][25] Other clients as of 2019 included Polaris Project,[64] the Centers for Disease Control and Prevention, the National Center for Missing and Exploited Children,[28] the National Institutes of Health,[65] Team Rubicon,[66] and the United Nations World Food Programme.[67]
In October 2020, Palantir began helping the federal government set up a system that will track the manufacture, distribution and administration of COVID-19 vaccines across the country.[68]
U.S. military, intelligence, and police
Palantir Gotham is used by counter-terrorism analysts at offices in the United States Intelligence Community and United States Department of Defense, fraud investigators at the Recovery Accountability and Transparency Board, and cyber analysts at Information Warfare Monitor (responsible for the GhostNet and the Shadow Network investigation).
Other clients as of 2013 included DHS, NSA, FBI, CDC, the Marine Corps, the Air Force, Special Operations Command, West Point, the Joint IED Defeat Organization and Allies. However, at the time the United States Army continued to use its own data analysis tool.[28] Also, according to TechCrunch, “The U.S. spy agencies also employed Palantir to connect databases across departments. Before this, most of the databases used by the CIA and FBI were siloed, forcing users to search each database individually. Now everything is linked together using Palantir.”[28]
U.S. military intelligence used the Palantir product to improve their ability to predict locations of improvised explosive devices in its war in Afghanistan. A small number of practitioners reported it to be more useful than the United States Army’s Program of Record, the Distributed Common Ground System (DCGS-A). California Congressman Duncan D. Hunter complained of United States Department of Defense obstacles to its wider use in 2012.[69]
Palantir has also been reported to be working with various U.S. police departments, for example accepting a contract in 2013 to help the Northern California Regional Intelligence Center build a controversial license plates database for California.[70] In 2012 New Orleans Police Department partnered with Palantir to create a predictive policing program.[71]
In 2014, US Immigration and Customs Enforcement (ICE) awarded Palantir a $41 million contract to build and maintain a new intelligence system called Investigative Case Management (ICM) to track personal and criminal records of legal and illegal immigrants. This application has originally been conceived by ICE’s office of Homeland Security Investigations (HSI), allowing its users access to intelligence platforms maintained by other federal and private law enforcement entities. The system reached its “final operation capacity” under the Trump administration in September 2017.[72]
Palantir took over the Pentagon’s Project Maven contract in 2019 after Google decided not to continue developing AI unmanned drones used for bombings and intelligence.[73]
International Atomic Energy Agency
Palantir was used by the International Atomic Energy Agency (IAEA) to verify if Iran was in compliance with the 2015 agreement.[33]
Europe
The firm has contracts relating to patient data from the British National Health Service. It was awarded an emergency, no-competition contract to mine COVID-19 patient data in 2019. In 2020 this was valued at more than £23.5 million and was extended for two more years. The firm was encouraged by Liam Fox “to expand their software business” in Britain.[74] It was said to be ” critical to the success of the vaccination and PPE programmes,” but its involvement in the NHS was controversial among civil liberties groups.[75]
The Danish POL-INTEL predictive policing project has been operational since 2017 and is based on the Gotham system. According to the AP the Danish system “uses a mapping system to build a so-called heat map identifying areas with higher crime rates.” The Gotham system has also been used by German state police in Hesse and Europol.[50]
The Norwegian Customs is using Palantir Gotham to screen passengers and vehicles for control. Known inputs are prefiled freight documents, passenger lists, the national Currency Exchange database (tracks all cross-border currency exchanges), the Norwegian Welfare Administrations employer- and employee-registry, the Norwegian stock holder registry and 30 public databases from InfoTorg. InfoTorg provides access to more than 30 databases, including the Norwegian National Citizen registry, European Business Register, the Norwegian DMV vehicle registry, various credit databases etc. These databases are supplemented by the Norwegian Customs Departments own intelligence reports, including results of previous controls. The system is also augmented by data from public sources such as social media.[76]
NHS England’s former artificial intelligence chief, Indra Joshi, was recruited by the company in 2022. The company said they were planning to increase their team in the UK by 250.[77]
Palantir stand at the NHS Confederation conference 2022
Partnerships and contracts
International Business Machines
On February 8, 2021, Palantir and IBM announced a new partnership that would use IBM’s hybrid cloud data platform alongside Palantir’s operations platform for building applications. The product, Palantir for IBM Cloud Pak for Data, is expected to simplify the process of building and deploying AI-integrated applications with IBM Watson. It will help businesses/users interpret and use large datasets without needing a strong technical background. Palantir for IBM Cloud Pak for Data will be available for general use in March 2021.[78]
Amazon (AWS)
On March 5, 2021, Palantir announced its partnership with Amazon AWS. Palantir’s ERP Suite is now optimized to run on Amazon Web Services. One of the first notable successes of the ERP suite was with BP, which was able to save about $50 million in working capital within two weeks of onboarding the system.[79]
Babylon Health
Palantir took a stake in Babylon Health in June 2021. Ali Parsa told the Financial Times that “nobody” has brought some of the tech that Palantir owns “into the realm of biology and health care”.[57]
Controversies
Algorithm development
I2 Inc sued Palantir in Federal Court alleging fraud, conspiracy, and copyright infringement over Palantir’s algorithm. Shyam Sankar, Palantir’s director of business development, used a private eye company as the cutout for obtaining I2’s code. I2 settled out of court for $10 million in 2011.[53]
WikiLeaks proposals (2010)
In 2010, Hunton & Williams LLP allegedly asked Berico Technologies, Palantir, and HBGary Federal to draft a response plan to “the WikiLeaks Threat.” In early 2011 Anonymous publicly released HBGary-internal documents, including the plan. The plan proposed that Palantir software would “serve as the foundation for all the data collection, integration, analysis, and production efforts.”[80] The plan also included slides, allegedly authored by HBGary CEO Aaron Barr, which suggested “[spreading] disinformation” and “disrupting” Glenn Greenwald’s support for WikiLeaks.[81]
Palantir CEO Karp ended all ties to HBGary and issued a statement apologizing to “progressive organizations… and Greenwald … for any involvement that we may have had in these matters.” Palantir placed an employee on leave pending a review by a third-party law firm. The employee was later reinstated.[80]
Racial discrimination lawsuit (2016)
On September 26, 2016, the Office of Federal Contract Compliance Programs of the U.S. Department of Labor filed a lawsuit against Palantir alleging that the company discriminated against Asian job applicants on the basis of their race.[82] According to the lawsuit, the company “routinely eliminated” Asian applicants during the hiring process, even when they were “as qualified as white applicants” for the same jobs.[83] Palantir settled the suit in April 2017 for $1.7 million while not admitting wrongdoing.[84]
British Parliament inquiry (2018)
During questioning in front of the Digital, Culture, Media and Sport Select Committee, Christopher Wylie, the former research director of Cambridge Analytica, said that several meetings had taken place between Palantir and Cambridge Analytica, and that Alexander Nix, the chief executive of SCL, had facilitated their use of Aleksandr Kogan’s data which had been obtained from his app “thisisyourdigitallife” by mining personal surveys. Kogan later established Global Science Research to share the data with Cambridge Analytica and others. Wylie confirmed that both employees from Cambridge Analytica and Palantir used Kogan’s Global Science Research and harvested Facebook data together in the same offices.[85][86]
ICE partnership (since 2014)
Palantir has come under criticism due to its partnership developing software for U.S. Immigration and Customs Enforcement. Palantir has responded that its software is not used to facilitate deportations. In a statement provided to the New York Times,[87] the firm implied that because its contract was with HSI, a division of ICE focused on investigating criminal activities, it played no role in deportations. However, documents obtained by The Intercept[72] show that this is not the case. According to these documents, Palantir’s ICM software is considered ‘mission critical’ to ICE. Other groups critical of Palantir include the Brennan Center for Justice,[88] National Immigration Project,[89] the Immigrant Defense Project,[90] the Tech Workers Coalition and Mijente.[91] In one internal ICE report[92] Mijente acquired, it was revealed that Palantir’s software was critical in an operation to arrest the parents of undocumented migrant children.
On September 28, 2020, Amnesty International released a report criticizing Palantir failure to conduct human rights due diligence around its contracts with ICE. Concerns around Palantir’s rights record were being scrutinized for contributing to human rights violations of asylum-seekers and migrants.[93][94]
“HHS Protect Now” and privacy concerns (since 2020)
Unbalanced scales.svg
This section may be unbalanced towards certain viewpoints. Please improve the article or discuss the issue on the talk page. (December 2020)
The ongoing COVID-19 pandemic has prompted tech companies to respond to growing demand for citizen information from governments in order to conduct contact tracing and to analyze patient data.[95] Consequently, data collection companies, such as Palantir, have been contracted to partake in pandemic data collection practices. Palantir’s participation in “HHS Protect Now”, a program launched by the United States Department of Health and Human Services to track the spread of the coronavirus, has attracted criticism from American lawmakers.[96]
Palantir’s participation in COVID-19 response projects re-ignited debates over its controversial involvement in tracking undocumented immigrants, especially its alleged effects on digital inequality and potential restrictions on online freedoms. Critics allege that confidential data acquired by HHS could be exploited by other federal agencies in unregulated and potentially harmful ways.[96] Alternative proposals request greater transparency in the process to determine whether any of the data aggregated would be shared with the US Immigration and Customs Enforcement to single out undocumented immigrants.[96]
Project Maven (since 2018)
After Google had issues with employees walking out concerning the new contract in partnership with the Pentagon, Project Maven, a secret artificial intelligence program aimed at the unmanned operation of aerial vehicles, was taken up by Palantir. Critics warn that the technology could lead to autonomous weapons that decide who to strike without human input.[73]
See also
Government by algorithm
References
Bursztynsky, Jessica (19 August 2020). “Palantir to relocate headquarters from Silicon Valley to Colorado”. CNBC. Archived from the original on 28 October 2020. Retrieved 5 October 2020.
“US SEC: Form 10-K Palantir Technologies Inc”. U.S. Securities and Exchange Commission. 24 February 2022.
Steinberger, Michael (2020-10-21). “Does Palantir See Too Much?”. The New York Times. ISSN 0362-4331. Retrieved 2020-11-02.
“Peter Thiel’s Palantir Wins Role in $823 Million Government Contract”. Bloomberg. 2020-02-25. Archived from the original on 2020-10-28. Retrieved 2020-03-18.
“Apollo | Palantir”. www.palantir.com. Retrieved 2021-12-14.
Gorman, Siobhan (September 4, 2009). “How Team of Geeks Cracked Spy Trade”. The Wall Street Journal. Archived from the original on April 16, 2019. Retrieved August 8, 2017.
“A Tech Fix For Illegal Government Snooping?”. NPR.org. NPR. Archived from the original on 2020-10-28. Retrieved 2012-01-30.
“Palantir Posted Nearly $1 Billion in 2018 Sales, Executive Says”. Bloomberg.com. Bloomberg. 2019-01-16. Archived from the original on 2020-10-28. Retrieved 2019-02-21.
“A (Pretty) Complete History of Palantir”. Maus Strategic Consulting. April 2014. Archived from the original on 16 May 2014.
Greenberg, Andy; Mac, Ryan (August 14, 2013). “How A ‘Deviant’ Philosopher Built Palantir, A CIA-Funded Data-Mining Juggernaut”. Forbes. Archived from the original on June 4, 2015. Retrieved September 7, 2017.
“charlierose”. Media.palantirtech.com. Archived from the original on 2012-02-01. Retrieved 2012-01-30.
“Contact information”. Archived from the original on 2013-09-06. Retrieved 2013-09-10.
“Palantir”. Founders Fund. Archived from the original on 2010-11-23. Retrieved 2012-01-30.
Rusli, Evelyn (2010-06-25). “Palantir: The Next Billion-Dollar Company Raises $90 Million”. TechCrunch. Archived from the original on 2020-10-28. Retrieved 2012-01-30.
“Alexander Karp”. Charlie Rose. 2009-08-11. Archived from the original on 2012-01-04. Retrieved 2012-01-30.
Widman, Jeff (2009-06-05). “Palantir keeps it lean and mean on five-year journey from zero to 150 employees”. VentureBeat. Archived from the original on 2012-03-03. Retrieved 2012-01-30.
Gesher, Ari (2010-03-08). “Friction in Human-Computer Symbiosis: Kasparov on Chess”. Palantir tech. Archived from the original on 2012-04-14. Retrieved 2012-01-30.
“Video”. CNN. Archived from the original on 2000-08-16. Retrieved 2010-06-26.
Chiang, Oliver (2010-04-30). “PayPal-Based Technology Helped Bust India’s And The Dalai Lama’s Cyberspies”. Forbes. Archived from the original on 2017-08-14. Retrieved 2017-09-07.
Markoff, John (March 29, 2009). “Vast Spy System Loots Computers in 103 Countries”. The New York Times. Archived from the original on April 1, 2009. Retrieved February 25, 2017.
“Press release: Thomson Reuters and Palantir Technologies enter exclusive agreement to create next-generation analytics platform for financial clients”. Thomson Reuters. 2010-04-12. Archived from the original on 2012-05-08. Retrieved 2013-05-27.
Kauffman, Tim (2010-06-27). “The new high-tech weapons against fraud”. Federal Times. Retrieved 2012-01-30.
Kiely, Kathy (2010-06-18). “Obama administration to create ‘do not pay’ list to bar shady contractors”. USA Today. Archived from the original on 2012-07-07. Retrieved 2010-06-22.
Orszag, Peter (2010-06-18). “Do Not Pay? Do Read This Post”. Office of Management and Budget. Retrieved 2012-01-30 – via National Archives.
Kuhn, Eric (June 1, 2010). “Companies capitalize on ‘open government'”. Political Ticker blog. CNN. Archived from the original on October 28, 2020. Retrieved September 28, 2013.
“Using Palantir with Open Source Data: Finding and Preventing Fraud in Stimulus Spending”. Palantir Technologies. 2010-05-04. Archived from the original on 2013-11-10. Retrieved 2013-05-27.
Vance, Ashlee; Stone, Brad (November 22, 2011). “Palantir, the War on Terror’s Secret Weapon: A Silicon Valley startup that collates threats has quietly become indispensable to the U.S. intelligence community”. Business Week Magazine. Archived from the original on February 18, 2013. Retrieved September 28, 2013.
Burns, Matt (January 11, 2015). “Leaked Palantir Doc Reveals Uses, Specific Functions And Key Clients”. TechCrunch. Archived from the original on 2015-11-27. Retrieved 2015-02-21.
“Notice of Exempt Offering of Securities”. The United States Securities and Exchange Commission. September 27, 2013. Archived from the original on October 28, 2020. Retrieved September 28, 2013.
Cutler, Kim-Mai. “Palantir Is Raising $197M In Growth Capital, SEC Filing Shows”. TechCrunch. Archived from the original on 2020-10-28. Retrieved 2017-06-25.
Greenberg, Andy; Mac, Ryan (September 2, 2013). “How A ‘Deviant’ Philosopher Built Palantir, A CIA-Funded Data-Mining Juggernaut”. Forbes. Archived from the original on June 4, 2015. Retrieved September 28, 2013.
Mac, Ryan (December 11, 2014). “Palantir Aiming To Raise $400 Million In New Round”. Forbes. Archived from the original on 2015-01-02. Retrieved 2015-02-21.
Tirone, Jonathan (2018-05-08). “Peter Thiel and Palantir Are at the Heart of the Iran Nuclear Deal”. Bloomberg.com. Retrieved 2018-05-08. “Palantir, which Thiel and his partners built with CIA funding”
“Palantir raising more money after tagged with 15 billion valuation”, The Wall Street Journal, January 16, 2015, archived from the original on October 28, 2020, retrieved August 4, 2017.
Alden, William (June 23, 2015). “Palantir Valued At $20 Billion In New Funding Round”. BuzzFeed. Archived from the original on June 24, 2015. Retrieved June 23, 2015.
Buhr, Sarah (December 23, 2015). “Palantir Has Raised $880 Million At A $20 Billion Valuation”. TechCrunch. Archived from the original on January 29, 2017. Retrieved December 15, 2016.
Condon, Stephanie. “Palantir acquires data visualization startup Silk”. Archived from the original on 28 October 2020. Retrieved 10 August 2016.
Kelion, Leo (2020-03-28). “NHS turns to big tech to tackle Covid-19 hot spots”. BBC News. Archived from the original on 2020-10-28. Retrieved 2020-03-29.
“The power of data in a pandemic – Technology in the NHS”. healthtech.blog.gov.uk. Retrieved 2020-03-29.
Steinberger, Michael (21 October 2020). “Does Palantir See Too Much?”. The New York Times. Archived from the original on 28 October 2020. Retrieved 26 October 2020.
Parker, Ashley; Stanley-Becker, Isaac; Linskey, Annie. “10 days of struggle: Inside Biden’s early coronavirus vaccine effort”. Washington Post. ISSN 0190-8286. Retrieved 2021-01-31.
O’Donnell, Carl (2020-12-07). “Palantir wins $44 million FDA contract, boosting shares 21%”. Reuters. Retrieved 2020-12-08.
“SEC FORM D”. Securities and Exchange Commission. Archived from the original on 2015-07-25. Retrieved 2015-05-31.
Buhr, Sarah (December 23, 2015). “Palantir Has Raised $880 Million At A $20 Billion Valuation”. TechCrunch. Archived from the original on January 29, 2017. Retrieved December 15, 2016.
Waldman, Peter; Chapman, Lizette; April 19, Jordan Robertson. “Palantir Knows Everything About You”. Bloomberg.com. Bloomberg. Archived from the original on 23 April 2018. Retrieved 23 April 2018.
Copeland, Rob (2018-10-18). “Secretive Data Company Palantir Weighs Giant Public Offering”. Wall Street Journal. ISSN 0099-9660. Archived from the original on 2018-10-18. Retrieved 2018-10-19.
Korosec, Kirsten; Whittaker, Zack; Mascarenhas, Natasha (7 July 2020). “Secretive data startup Palantir has confidentially filed for an IPO”. TechCrunch. Archived from the original on 7 July 2020.
Kindig, Beth (2020-09-29). “Palantir IPO: Deep-Dive Analysis”. Forbes. Retrieved 2020-11-09.
“Palantir has pumped over $400 million into SPACs and boosted its revenues at the same time”. Forbes. 2021-11-24. Archived from the original on 2021-11-24.
Neslen, Arthur (20 October 2021). “FEATURE-Pushback against AI policing in Europe heats up over racism fears”. www.reuters.com. Reuters. Retrieved 1 November 2021.
“Palantir Stops Mocking Salespeople and Starts Hiring Them”. Bloomberg.com. 7 January 2019. Retrieved 2019-02-28.
Chapman, Lizette (7 January 2019). “Palantir once mocked the idea of salespeople. Now it’s hiring them”. Los Angeles Times. Archived from the original on 2020-10-28. Retrieved 2019-02-28.
Waldman, Peter; Chapman, Lizette; Robertson, Jordan (April 19, 2018). “Peter Thiel’s data-mining company is using War on Terror tools to track American citizens. The scary thing? Palantir is desperate for new customers”. Bloomberg. Archived from the original on October 28, 2020. Retrieved April 24, 2018.
Mak, Aaron (April 19, 2018). “Report: Palantir Helped JPMorgan Spy on Employees”. Bloomberg. Archived from the original on October 28, 2020. Retrieved April 24, 2018.
Palantir (2020-10-08). “Palantir Apollo: Powering SaaS where no SaaS has gone before”. Medium. Archived from the original on 2020-10-19. Retrieved 2020-10-19.
Cash, Mark. “Peering into Palantir’s Data Market Disruption”. Morningstar CA. Retrieved 2020-10-19.
“Campaign launches to try to force Palantir out of Britain’s NHS”. CNBC. 4 June 2021. Retrieved 16 June 2021.
Sidel, Robin (February 10, 2015). “First Data Reports First Quarterly Profit in More Than Seven Years”. Wall Street Journal. Archived from the original on 2020-10-28. Retrieved 2015-02-25.
“A Human Driven Data-centric Approach to Accountability: Analyzing Data to Prevent Fraud, Waste and Abuse in Stimulus Spending: Gov 2.0 Expo 2010 – Co-produced by UBM TechWeb & O’Reilly Conferences, May 25 – 27, 2010, Washington, DC”. Gov2expo.com. Archived from the original on 2020-10-28. Retrieved 2012-01-30.
“Merck KGaA, Palantir’s new joint venture looks to tear down cancer research data silos”. MobiHealthNews. 2018-11-20. Archived from the original on 2020-10-28. Retrieved 2019-02-27.
“Airbus believes its AI can eliminate flight delays”. VentureBeat. 2018-10-23. Archived from the original on 2020-10-28. Retrieved 2019-02-27.
Palantir. “Palantir Foundry Enables Scuderia Ferrari Through Data”. www.prnewswire.com. Archived from the original on 2020-10-28. Retrieved 2019-02-27.
“CNN.com Video”. CNN. Archived from the original on 2000-08-16. Retrieved 2010-06-26.
Knox, Karin (January 24, 2014). “How Many Years A Slave?”. Archived from the original on March 4, 2016.
“With $7M contract, NIH taps big data analysis platform Palantir to streamline health research”. MobiHealthNews. 2018-09-24. Archived from the original on 2020-10-28. Retrieved 2019-02-28.
“Can Data-Crunching Palantir Find Missing Children and Catch Traffickers?”. Fortune. Archived from the original on 2020-10-28. Retrieved 2019-02-28.
“Palantir and WFP partner to help transform global humanitarian delivery | World Food Programme”. www1.wfp.org. Archived from the original on 2020-10-28. Retrieved 2019-02-28.
Winkler, Peter Loftus and Rolfe (2020-10-22). “WSJ News Exclusive | Palantir to Help U.S. Track Covid-19 Vaccines”. Wall Street Journal. ISSN 0099-9660. Archived from the original on 2020-10-28. Retrieved 2020-10-23.
Scarborough, Rowan (July 16, 2012). “Military has to fight to purchase lauded IED buster”. The Washington Times. Archived from the original on July 19, 2012. Retrieved September 29, 2013.
Blagdon, Jeff (June 29, 2013). “Palantir is helping California police develop controversial license plate database”. The Verge. Archived from the original on October 28, 2020. Retrieved September 7, 2017.
Winston, Ali (February 27, 2018). “PALANTIR HAS SECRETLY BEEN USING NEW ORLEANS TO TEST ITS PREDICTIVE POLICING TECHNOLOGY”. The Verge. Archived from the original on February 28, 2018. Retrieved February 28, 2018.
Woodman, Spencer (2 March 2017). “Palantir Provides the Engine for Donald Trump’s Deportation Machine”. The Intercept. The Intercept. Archived from the original on 28 October 2020. Retrieved 6 November 2018.
“Palantir took over from Google on Project Maven”. Business Insider. December 2019. Archived from the original on 28 October 2020. Retrieved 17 January 2020.
“UK trade department courted US firm Palantir over ‘untapped’ NHS data potential”. Politico. 29 June 2021. Retrieved 6 July 2021.
“Palantir gears up to expand its reach into UK’s NHS”. Financial Times. 9 June 2022. Retrieved 9 June 2022.
“Norwegian Customs implement new methods to catch smugglers”. Nettavisen. 24 January 2018. Retrieved 5 December 2021.
“NHS’s AI chief joins CIA-linked US tech firm”. Health Service Journal. 22 April 2022. Retrieved 24 May 2022.
“IBM and Palantir Partner to Help Businesses Easily Deploy Powerful and Open AI Applications; Unlock Valuable Data Across Hybrid Cloud Environments”.
“Launching ERP Suite to deliver cost savings for AWS customers”. 5 March 2021.
Harris, Shane (31 January 2012). “Killer App”. Washingtonian. Archived from the original on 28 October 2020. Retrieved 14 March 2012.
Wray, James; Stabe, Ulf. “Data intelligence firms proposed a systematic attack against WikiLeaks”. Thetechherald.com. Archived from the original on 2018-11-26. Retrieved 2012-01-30.
“COMPLAINT FOR VIOLATIONS OF EXECUTIVE ORDER 11246” (PDF). United States Department of Justice. Archived from the original (PDF) on 2016-10-01. Retrieved 2016-09-27.
Kosoff, Maya (September 27, 2016). “U.S. GOVERNMENT SUES PETER THIEL’S SECRETIVE BIG-DATA START-UP FOR DISCRIMINATION”. Vanity Fair. Archived from the original on November 4, 2016. Retrieved October 31, 2016.
Kravets, David (26 April 2017). “Palantir settles US charges that it discriminated against Asian engineers”. Ars Technica. Archived from the original on 28 October 2020. Retrieved 26 April 2017.
Pegg, David; Cadwalladr, Carole (March 27, 2018). “US data firm admits employee approached Cambridge Analytica: Palantir confirm employee ‘engaged in a personal capacity’ with the company”. The Guardian. Archived from the original on October 28, 2020. Retrieved April 23, 2018.
Confessore, Nicholas; Rosenberg, Matthew (March 27, 2018). “Spy Contractor’s Idea Helped Cambridge Analytica Harvest Facebook Data”. New York Times. Archived from the original on October 28, 2020. Retrieved April 24, 2018.
“DealBook Briefing: Investors May Be Overlooking Their Own Discrimination”. The New York Times. 11 December 2018. Archived from the original on 4 August 2019. Retrieved 4 August 2019.
“Palantir Contract Dispute Exposes NYPD’s Lack of Transparency”. Brennan Center for Justice. Brennan Center for Justice. Archived from the original on 2020-10-28. Retrieved 2019-08-04.
“National Immigration Project of the National Lawyers Guild”. www.nationalimmigrationproject.org. Archived from the original on 2020-10-28. Retrieved 2019-08-04.
“Immigrant Defense Project – Fighting for Justice & Human Rights for ALL”. Archived from the original on 2020-10-28. Retrieved 2019-08-04.
“Mijente”. Mijente. Archived from the original on 2019-08-04. Retrieved 2019-08-04.
“Palantir Played Key Role in Arresting Families for Deportation, Document Shows”. Mijente. 2 May 2019. Archived from the original on 28 October 2020. Retrieved 4 August 2019.
“Failing To Do Right:The Urgent Need for Palantir to Respect Human Rights” (PDF). Amnesty International. Archived (PDF) from the original on 28 October 2020. Retrieved 28 September 2020.
“Amnesty International slams Palantir’s human rights record”. CBS News. Archived from the original on 28 October 2020. Retrieved 29 September 2020.
Muhlberg, Byron (13 May 2020). “Privacy Advocates Calls for Transparency Over Use of Patient Data”. CPO Magazine. Retrieved 30 November 2020.
Albergotti, Reed (1 July 2020). “Lawmakers call for more transparency in health agency’s pandemic data collection practices”. Washington Post. Retrieved 30 November 2020.
External links
Official website
Business data for Palantir Technologies:
BloombergGoogleReutersSEC filingsYahoo!
Categories:
2003 establishments in CaliforniaAnalytics companiesBig data companiesBusiness software companiesCompanies based in DenverAmerican companies established in 2003Data brokersDetectives and criminal investigatorsCriminal investigationSoftware companies based in ColoradoSoftware companies of the United StatesGovernment by algorithmSoftware companies established in 2003Companies listed on the New York Stock ExchangeDirect stock offeringsLink analysisThings named after Tolkien works
*Founders of Palantir:
* (Wiki) Peter Andreas Thiel is a German-American billionaire entrepreneur, venture capitalist, and political activist. A co-founder of PayPal, Palantir Technologies, and Founders Fund, he was the first outside investor in Facebook. As of May 2022, Thiel had an estimated net worth of $7.19 billion and was ranked 297th on the Bloomberg Billionaires Index
** (Wiki) Nathan Gettings is CEO of RoboteX, which makes multi-purpose robots used by police agencies, SWAT teams, and civilian users. Gettings is also CTO of Founders Fund portfolio company Palantir, the analytical software firm that helped track down the perpetrators of the attacks on the Dalai Lama’s computers
*** Joseph Todd Lonsdale V is an American entrepreneur, technology investor, and philanthropist. He is a founder of 8VC, a technology investment firm, and a co-founder of Palantir Technologies, Addepar, and OpenGov, and was an early investor in a number of companies, including the e-commerce platform Wish. After graduating from Stanford University, Lonsdale worked as an executive at Clarium Capital, a global macro hedge fund run by Peter Thiel, and in 2004 co-founded Palantir, a data analytics company for organizations in industries like intelligence and finance. Lonsdale left Palantir in 2009 to co-found Addepar, a wealth management technology company. He has co-founded several other technology companies, including OpenGov (a technology platform for data intelligence and budgeting of governments) and Epirus (a defense technology company)
**** Stephen Cohen (born September 30, 1982) is an American computer scientist and entrepreneur. He is best known as a co-founder of Palantir Technologies,[1][2] a platform for analyzing integration and visualizing data used by governments and businesses.[3][4] He is credited with creating the initial prototype of Palantir in eight weeks.[5] Since then, he has interviewed over 4500 candidates and continues to be actively involved in Palantir.[6] Previously to Palantir, Cohen worked with Peter Thiel at Clarium Capital.[1] He also served as an adviser to Backtype prior to its acquisition by Twitter in 2011
***** Alexander Caedmon Karp was born on 2 October 1967 in New York City,[4] the son of a Jewish father and an African American mother,[5] Karp was raised in Philadelphia and graduated from Central High School in 1985.[6][7] He has said he struggled with dyslexia from an early age.[8]
***** (Wiki) Alexander Caedmon Karp was born on 2 October 1967 in New York City, the son of a Jewish father and an African American mother, Karp was raised in Philadelphia and graduated from Central High School in 1985. He has said he struggled with dyslexia from an early age.[Alex Karp earned a bachelor’s degree from Haverford College (Haverford, Pennsylvania) in 1989, a juris doctor (JD) degree from Stanford University in 1992, and a Dr. phil. degree in neoclassical social theory from Goethe University (Frankfurt, Germany) in 2002. Karp’s doctoral thesis, supervised by Karola Brede, was titled “Aggression in der Lebenswelt: Die Erweiterung des Parsonsschen Konzepts der Aggression durch die Beschreibung des Zusammenhangs von Jargon, Aggression und Kultur”, which means “Aggression in the life-world: The extension of Parsons’ concept of aggression by describing the connection between jargon, aggression, and culture.”
XII. How Palantir Conquered the World
The Corbett Report
by James Corbett
corbettreport.com
October 22, 2022

Imagine a company that knows everything about everyone. A company that is equally at ease helping banks identify fraud as it is helping intelligence agencies track down enemies of the state. A company that can combine pictures of you with your cell phone location data, emails you’ve written, your health records and credit card purchases and thousands of other pieces of electronic data to paint an intimate portrait of your life—a portrait that any would-be investigator can pull up with a few keystrokes. A company that can target you anywhere in the world at any time.
Now stop imagining that company, because it already exists. It’s called Palantir Technologies.
Founded by billionaire PayPal co-founder and Facebook early investor Peter Thiel, this plucky little Silicon Valley startup has long been the darling of the US military and the intelligence community, and it’s increasingly the darling of the corporate world. And—given Palantir’s ability to surveil, track and, ultimately, control every aspect of your daily life—it isn’t hard to see why.
Even so, few in the general public have ever heard of Palantir, and those who have know little beyond the fact that it’s a bad company that does creepy things.
But this is The Corbett Report. We can do better than that.
Today, let’s explore the roots of this threat to humanity, expose the extent to which it has already laid your life bare to the all-seeing eye of the would-be world controllers, and peer into the magical seeing stone to see what the future holds for Palantir Technologies.
WHAT IS PALANTIR?

So, what is Palantir, exactly?
As it turns out, that question is surprisingly easy to answer. Palantir is a front company for a once-secret military and intelligence project to collect and data mine every available piece of information about you. The hard part is extracting that simple answer from the mass of lies, obfuscation, untruths, half-truths and contextless facts that are presented in the lamestream media’s coverage of the company.
You see, the official story of this Silicon Valley surveillance specialist outfit—repeated in any number of mainstream puff pieces—is that Peter Thiel founded Palantir Technologies in 2004 as a vehicle for turning PayPal’s fraud detection software into a marketable product. His dream was for Palantir to assist the growing national security leviathan in creating a system for analyzing financial activity for signs of terrorist activity.
But, according to the “libertarian” Thiel (who works with and profits from the national security state, promotes warmongering politicians, writes paeans to Leo Strauss and Carl Schmitt, and, oh by the way, just happens to be a member of Bilderberg’s steering committee), Palantir’s software is not about constructing the most intrusive system of electronic surveillance ever devised. No, of course not! It’s all about protecting civil liberties!
From its inception, Palantir was conceived as “a mission-oriented company,” Thiel told Forbes in a 2013 profile of the company and its founders. “I defined the problem as needing to reduce terrorism while preserving civil liberties.”
This is such a bald-faced and easily debunkable lie that it could only be regurgitated by the mockingbird repeaters of the dinosaur media. But it’s easy to see why the dutiful stenographers of the lapdog press would repeat it. After all, when it comes to Palantir, there are always more interesting things to report on than how it came to be founded or what it actually does.
Just take the name of the company: Palantir. It is a reference to the magical seeing stones that the wizards of J. R. R. Tolkien’s mythical The Lord of the Rings universe use to see through space and time. This whimsical naming convention carries over into what one reporter has labeled a “casual, nerdy culture” that permeates the company:
Its offices are named after locations in the Tolkien fable. Thus, Palantir’s Palo Alto headquarters is The Shire, its office in McLean, Virginia (located just six miles from the CIA), is Rivendell; its Washington, D.C., branch is dubbed Minas Tirith, etc.
It has a hotline called the Batphone that allows engineers to anonymously report to company officials any customer requests that they consider to be unethical.
Two of its core analytic software programs, Gotham and Metropolis, are named after cities in the DC Comics universe.
One of the conference rooms in The Shire has been converted into a children’s ball pit.
Oh, how delightfully quirky! Surely no Silicon Valley startup with such an eclectic working environment could be involved in anything evil, could they?
To be fair, a number of the company profiles in the corporate press—a 2012 corporate profile from The Washingtonian, for example, or a 2013 profile of the company’s eclectic philosophy grad CEO in Forbes, or a 2020 New York Times Magazine piece on “Does Palantir See Too Much?”—do gesture to the creepier facets of Palantir.
Why does Palantir’s CEO, Alex Karp, insist on two-way mirrors for his office windows? Why does the company use acoustic transducers to vibrate the glass of their office windows, creating white noise to disrupt possible electronic eavesdroppers? Was Palantir’s Prism program related to the NSA’s PRISM program? (SPOILER: It sure wasn’t! Nothing to see here, folks!)
But still, one is left feeling that something is wanting after reading these MSM articles. It’s as if they have the pieces of a puzzle sitting in front of them but they still haven’t actually put those pieces together.
In order to complete that puzzle, you need to turn to an independent researcher like Whitney Webb. As Webb points out in her new, must-read, two-volume tour de force, One Nation Under Blackmail, Palantir was not founded in 2004—as the corporate presstitutes continually assert—but in May 2003. (The professional journos probably missed this small detail because they’d have to actually read through SEC filings to discover that Thiel’s origin story of Palantir is a demonstrable lie, and what dinosaur media “reporter” has time to do that?)
Now, whether the company was founded in 2003 or 2004 may seem like a small detail at first glance. But, upon closer inspection, this data discrepancy—and the fact that Thiel has so often lied about the true founding of the company—provides a clue to Palantir’s actual origin.
You see, it just so happens that May 2003 was the exact time when the Pentagon’s Defense Advanced Research Projects Agency (DARPA) began officially backing away from its proposed the Total Information Awareness (TIA) program, renaming it Terrorism Information Awareness before Congress defunded the program altogether.
Never heard of the Total Information Awareness program? Well you probably remember the friendly little logo of the Information Awareness Office (IAO), the DARPA department under which it operated:

Lest that image leave any doubt, the IAO and its TIA program were indeed committed to collecting, storing and analyzing every piece of data on as many people as possible—from personal e-mails to social networks, credit card records, phone calls, medical records and numerous other sources—without so much as a warrant. The program’s goal was to “develop data-mining or knowledge discovery tools that would sort through the massive amounts of information to find patterns and associations,” and it even included funding for “the development of biometric technology to enable the identification and tracking of individuals.”
It’s a testament to just how incredibly creepy and over-the-line the TIA program was that, even then, in 2003—at the absolute pinnacle of War of Terror hysteria—it was immediately denounced by almost everyone in the public as the most draconian system of surveillance ever proposed. This bipartisan, widespread public backlash led to the second downfall of the IAO’s director, John Poindexter (who had previously been convicted for his role in the Iran-Contra affair), and to the defunding of the TIA program.
Thus, once we discover that Palantir was in fact incorporated in May 2003, not in 2004, which nearly every account of the company falsely asserts, we encounter a remarkable “coincidence.” We discover that at the exact same moment as the TIA was being dismantled (and transferred deeper into the bowels of Uncle Sam’s bureaucracy), Peter Thiel decided to create a company that could do exactly what the TIA had been attempting to achieve. That alone would make it the most remarkable coincidence in the world since Facebook was launched on the very same day that DARPA’s LifeLog program was scrapped.
But, amazingly, it gets even more coincidental.
Do you want to guess who it was that Thiel and co. turned to when they were looking to find their first customer for their new TIA-like company? You guessed it:
One day not long after Palantir was launched in 2004 [sic], Poindexter received a call from his friend Richard Perle, ex-chair of the Defense Policy Board, asking if he’d come to Perle’s house for a meeting with two entrepreneurs he knew from Palo Alto—Alex Karp, Palantir’s CEO, and his fellow cofounder Peter Thiel, a billionaire venture capitalist who’d helped start PayPal and was an early investor in Facebook.
That’s right, Thiel and Karp—an eccentric philosophy grad and fellow Stanford Law School alum whom Thiel appointed Palantir’s CEO despite his having no corporate experience—just so happened to secure a meeting with the recently ousted chief of the TIA program. And it just so happened that Poindexter was so impressed by the duo’s presentation—they had “elegantly accomplished what the TIA had set out to do,” as one popular account put it—that he referred them to In-Q-Tel, the CIA’s venture capital arm.
The CIA ended up pumping the first $2 million of outside money into Palantir and, more importantly, helped the company get its foot in the door of many other government clients, from intelligence agencies and military departments to the US Immigration and Customs Enforcement, the Centers for Disease Control and the IRS (among others).
And the rest, as they say, is history. . . .
. . . History written by the winners, that is. After all, “intrepid” lamestream “reporters” now have a ready-made narrative to spew for their profiles of the company: these weird, scruffily-dressed Silicon Valley outsiders arrived on the CIA’s doorstep like a band of invading barbarians to tear down the protocols of stuffy bureaucracy. Heck, they even sued the US Army over its procurement practices and ended up winning Army contracts!
Lost amid the gee-whizzery of this story are the niggling little details connecting Palantir to its TIA predecessor.
But that leads us to the next question in today’s exploration . . .
WHAT DOES PALANTIR DO?
OK, so Palantir is some kind of surveillance system thing-y? What does it actually do? How does it actually work?
Good questions. Glad you asked.
As noted above, the original impetus behind the founding of Palantir was the idea of turning PayPal’s fraud detection software into a data mining product that could be sold to national security clients to help them find “terrorists” (broadly defined).
Although the PayPal system worked specifically on data surrounding financial transactions, the Palantir idea quickly expanded to include all sorts of data. From the content of your emails to the subject of your phone calls to the details of your credit card transactions to your social media ramblings to your cell phone GPS logs, if it can be digitized, Palantir aims to feed it into a database and data mine it to discover relations and connections that are not immediately obvious to the average analyst. Palantir’s operating system then presents that data in a visually intuitive way and makes it easily searchable even by the non-tech inclined.
Well, that’s the idea, anyway. How it works in reality depends on who you ask. Some give glowing reports of the incredible results it can achieve. Others contend it’s all smoke and mirrors and the products’ success comes from good old-fashioned manpower. If the company sends teams of software developers to essentially embed themselves in clients’ companies and fine tune the generic Palantir software to those companies’ specific needs, is it really a magical “AI-driven” all-seeing-eye-in-a-box after all?
We in the general public might never know. Exactly how the software functions and what it looks like for its intelligence community clients—let alone how those clients actually use the software—is, needless to say, hidden behind layers of secrecy and classification.
Palantir, of course, uses this secrecy to its advantage.
In his account of the killing of Bin Laden, journalist Mark Bowden asserted that Osama bin Laden was caught less by the torture-and-courier Hollywood theatrics of Zero Dark Thirty and more by “an unfathomably rich database.” Bowden then goes on in the same passage to recount the founding of Palantir. For years thereafter, every feature article or company profile in the mainstream press implied that Palantir had been used to find bin Laden.
Eventually, the lamestream repeaters realized they were engaged in a game of telephone, repeating a story that started as a baseless implication that was never even asserted as fact, let alone properly reported. But the story still looms large in the mythos of Palantir and most “deep dives” on the company in the dinosaur press will include a repetition of the rumour that Palantir killed bin Laden. When questioned about it, Karp simply insists that he can’t comment, adding even further to the Palantir mystique.
Here’s what we do know: since its founding, Palantir has developed a range of products to serve its various clients, including:
Palantir Gotham — The original software developed by Palantir for the intelligence community, Gotham is billed as a “commercially-available, AI-ready operating system that improves and accelerates decisions for operators across roles and all domains;” and
Palantir Foundry — Palantir’s latest product, Foundry, is focused on the company’s corporate clients and is sold as an operating system that “leverages an open architecture to inform closed-loop operations—connecting data, analytics, and business teams to a common foundation,” which only sounds innocuous if you don’t know about what Ptech did on 9/11.
How precisely the company’s products are used is, again, a combination of classified information and trade secrets, but we do know that Palantir has:
Helped the NSA build the software to facilitate and augment the use of XKEYSCORE, the NSA’s “widest reaching” program, which captures “nearly everything a typical user does on the internet”;
Helped tech security firm HBGary formulate plans for attacking Wikileaks and its supporters, including exposing the identities of those trying to leak to the organization and smearing journalists who defend the site;
Helped New Orleans implement a “predictive policing” program, giving Palantir access to millions of searchable public records, court filings, licenses, addresses, phone numbers, and social media data without the knowledge or approval of the city council;
Partnered with the Centers for Disease Creation on its Data Collation and Integration for Public Health Event Response (DCIPHER) program, a partnership that has expanded in the COVID era to include “supporting the U.S. fight against the COVID-19 pandemic, from vaccine distribution to new areas such as improving supply chain resiliency and the distribution of life-saving therapeutics”; and
Expanded its biosecurity business to other countries, including overseeing the processing of sensitive medical records in a new partnership with Britain’s National Health Service.
But simply listing Palantir’s contracts or noting the lowlights of the creepy surveillance and database projects it has been involved in over the years is not enough. Palantir is not just a database. It is not simply software. It is a weapon.
As should be plainly evident by now, the power to see into every nook and cranny of someone’s life is the ultimate power. To know where someone lives, where they work, who they talk to, what they talk about, what they buy, what they eat and drink, where they travel and what they do online is to have total control over them. Sauron himself couldn’t ask for anything more.
As CEO Karp has bluntly stated: “our product is used on occasion to kill people.”
So, that only leaves one question . . .
WHERE IS PALANTIR GOING FROM HERE?

There are signs that cracks are showing in the Palantir facade. As soon as Trump was out of office, CDC officials were lobbying for the new Puppet-in-Chief to stop using Palantir’s software, telling Biden’s transition team that Palantir’s COVID tracking system “had problems from the very beginning” and it “never functioned in the way we thought it was going to.”
Some have even come out to claim that Palantir is all hype and little substance. A 2017 Buzzfeed article on Palantir’s connections with the intelligence community, for instance, contends that its relationship with the NSA has been more fraught with tension than is commonly reported. Later, a 2020 report from New York Magazine’s Intelligencer questioned whether Palantir is all smoke and mirrors, pointing out that the software’s “magical” ability to tease out useful leads from reams of data is in fact made possible by the company’s army of software engineers, who have to laboriously tailor the program to each clients’ needs.
More worrying for investors in the company, Palantir’s stock price has plummeted this year, from a years-long trading range around the $25 mark to $8.29 today, a point actually lower than its initial trading price when the stock went public in 2020.
But reports of Palantir’s demise (or its fall into irrelevance) may be premature. Just this past week the company inked a multi-year deal with Hertz to use the Palantir Foundry operating system to manage its 500,000 vehicle fleet and announced it will be opening a second UK office, this one near Britain’s National Health Service’s digital headquarters.
But this hand-wringing about the future of the company completely misses the point. Palantir Technologies did not start the drive to collect, analyze and act on every possible scrap of digital information in the world. It isn’t Peter Thiel, Alex Karp, or any of the other characters inhabiting the offices of The Shire who are the masterminds of this global surveillance grid. They are simply presenting a product to their customer, the deep state.
Palantir does not write the checks, it cashes them. It has served its role well for decades now, providing a convenient third-party cutout for the intelligence agencies to continue their work constructing the digital panopticon.
Make no mistake: as soon as Palantir no longer serves that role to their paymasters’ liking—as soon as the company becomes too burdened by the baggage of scandal or just too creepy to effectively perform its role as a front company for the deep state surveillance agenda—the “Shire” will be scoured just as thoroughly as Tolkein’s mythical village was. And, like Main Core, PROMIS, Ptech and the Information Awareness Office before it, Palantir will be relegated to a trivia question for conspiracy nerds. Meanwhile, all of Palantir’s capabilities will be rebuilt elsewhere under different corporate offices, operated under a different name and run by a different crew of willing dupes who will be only too eager to do their paymasters’ bidding.
Yes, regardless of whether or not Palantir’s fortunes are rising or falling, we can be sure of one thing: the idea behind Palantir—the dream of capturing, storing, analyzing and weaponizing data from every possible data source in order to better control the population—will not be going away anytime soon.
In the final analysis, the true threat is not Palantir itself but the deep state that has given rise to it. Our one saving grace is that the technocrats’ wet dream is in fact a pipe dream. Technocracy is, after all, insane and anti-Human and it will fail, but not without a hell of a fight.
In the meantime, there are things we can do to stop the construction of Our Digital Gulag. We can salt our data, for one. More fundamentally, we can begin taking the steps to unplug from the matrix and reject the electronic currency that is increasingly being used to track, trace and control our lives.
But, in the end, the Palantir nightmare isn’t going to end until the deep state that created it is removed from power.
altittude says:
10/24/2022 at 2:59 am
Fantastic article once again James. Was wondering if you have evver considered doing an article on Blackrocks Aladdin software? Anyhow keep up the fantastic Job both you and Brock
wessel says:
10/24/2022 at 4:20 am
The famous author is Tolkien, not Tolkein. It was high humans (Numenoreans) who brought the Palantirs to Middle Earth. One Palantir was used by a Wizard named Saruman, but otherwise there are few links between Palantirs and Wizards.
“The palantíri were made by the Ñoldor in Eldamar, likely by Fëanor himself during his time in Aman in the Time of the Trees, and then given by the Elves to The Faithful Númenóreans, who kept them as heirlooms until the Fall of Númenor during the late Second Age. Seven of these stones were rescued and brought to Middle-earth by Elendil and his sons and set in well-guarded Towers throughout the Realms in Exile.”
https://lotr.fandom.com/wiki/Palant%C3%ADri
Corbett says:
10/24/2022 at 8:25 am
Haha. I’m not going to lie; it gives me great pleasure to imagine someone like Thiel reading this article and getting angry not because I’m exposing Palantir but because “this guy just doesn’t know the lore of the palantíri!” Anyway, I’ve corrected the spelling of TolkEin but my misrepresentation of the gift of the elves to the Dumbledoreans (or whatever) stands!
wessel says:
10/25/2022 at 1:08 am
There are often insights to be gained from an art concept. Palantirs were used by Sauron to spy and mislead, specifically to paint an image of reality that was technically true, but misled those who saw it, to despair or death.
So the name “Palantir” advertises exactly what they do.
Funny honesty like that is not at all unusual. For example, before 2020, medical schools taught that Corona virus causes the common cold. So, when you look at headlines like:
Daily Coronavirus infections grow exponentially to 30.000!
80% of people in intensive care test positive for Corona!
Youths pass Corona virus to their grandparents!
Knowledge of the name will solve the riddle. Just replace “corona” with “common cold”. Not so scary now. And technically true, like propaganda must be.
hanky says:
10/24/2022 at 4:29 am
https://www.nytimes.com/2017/05/22/world/middleeast/trump-glowing-orb-saudi.html
Too cute to boot. What a joke (on the world).
Stephen says:
10/24/2022 at 8:55 pm
Brilliant as always JC!
beaconterraone says:
10/25/2022 at 3:54 pm
My obligatory reminder that we were warned, in the Bible. “That no one may buy or sell save he that had the Mark.” For over 19 centuries, people have speculated over what that means, and have tried to contort its meaning to fit Nero’s times or other nonsense explanation. Now, we see that the warning was literal, in relation to our modern world, described by a man who saw what he saw, but limited by the language and conceptualizations of his era.
Total Information Awareness, everywhere, all the time. And a universal, mandatory identifier for every livesto…uh, human, is a fundamental part of it.
HomeRemedySupply says:
10/25/2022 at 8:42 pm
I finally finished reading How Palantir Conquered the World.
This was fascinating. I learned a lot!
XIII. How A ‘Deviant’ Philosopher Built Palantir, A CIA-Funded Data-Mining Juggernaut
Andy GreenbergFormer Staff
Covering the worlds of data security, privacy and hacker culture.
Aug 14, 2013,10:10am EDT
This story appears in the Septemper 1, 2013 issue of Forbes.
Palantir chief executive Alex Karp. (Credit: Eric Millette for Forbes)
By Andy Greenberg and Ryan Mac
Since rumors began to spread that a startup called Palantir helped to kill Osama bin Laden, Alex Karp hasn’t had much time to himself.
On one sun-baked July morning in Silicon Valley Palantir’s lean 45-year-old chief executive, with a top-heavy mop of frazzled hair, hikes the grassy hills around Stanford University’s massive satellite antennae known as the Dish, a favorite meditative pastime. But his solitude is disturbed somewhat by “Mike,” an ex-Marine–silent, 6 foot 1, 270 pounds of mostly pectoral muscle–who trails him everywhere he goes. Even on the suburban streets of Palo Alto, steps from Palantir’s headquarters, the bodyguard lingers a few feet behind.
“It puts a massive cramp on your life,” Karp complains, his expression hidden behind large black sunglasses. “There’s nothing worse for reducing your ability to flirt with someone.”
Karp’s 24/7 security detail is meant to protect him from extremists who have sent him death threats and conspiracy theorists who have called Palantir to rant about the Illuminati. Schizophrenics have stalked Karp outside his office for days at a stretch. “It’s easy to be the focal point of fantasies,” he says, “if your company is involved in realities like ours.”
PROMOTED
Palantir lives the realities of its customers: the NSA, the FBI and the CIA–an early investor through its In-Q-Tel venture fund–along with an alphabet soup of other U.S. counterterrorism and military agencies. In the last five years Palantir has become the go-to company for mining massive data sets for intelligence and law enforcement applications, with a slick software interface and coders who parachute into clients’ headquarters to customize its programs. Palantir turns messy swamps of information into intuitively visualized maps, histograms and link charts. Give its so-called “forward-deployed engineers” a few days to crawl, tag and integrate every scrap of a customer’s data, and Palantir can elucidate problems as disparate as terrorism, disaster response and human trafficking.
Palantir’s advisors include Condoleezza Rice and former CIA director George Tenet, who says in an interview that “I wish we had a tool of its power” before 9/11. General David Petraeus, the most recent former CIA chief, describes Palantir to FORBES as “a better mousetrap when a better mousetrap was needed” and calls Karp “sheer brilliant.”
Among those using Palantir to connect the dots are the Marines, who have deployed its tools in Afghanistan for forensic analysis of roadside bombs and predicting insurgent attacks. The software helped locate Mexican drug cartel members who murdered an American customs agent and tracked down hackers who installed spyware on the computer of the Dalai Lama. In the book The Finish, detailing the killing of Osama bin Laden, author Mark Bowden writes that Palantir’s software “actually deserves the popular designation Killer App.”
And now Palantir is emerging from the shadow world of spies and special ops to take corporate America by storm. The same tools that can predict ambushes in Iraq are helping pharmaceutical firms analyze drug data. According to a former JPMorgan Chase staffer, they’ve saved the firm hundreds of millions of dollars by addressing issues from cyberfraud to distressed mortgages. A Palantir user at a bank can, in seconds, see connections between a Nigerian Internet protocol address, a proxy server somewhere within the U.S. and payments flowing out from a hijacked home equity line of credit, just as military customers piece together fingerprints on artillery shell fragments, location data, anonymous tips and social media to track down Afghani bombmakers.
Those tools have allowed Palantir’s T-shirted twentysomethings to woo customers away from the suits and ties of IBM, Booz Allen and Lockheed Martin with a product that deploys faster, offers cleaner results and often costs less than $1 million per installation–a fraction of the price its rivals can offer. Its commercial clients–whose identities it guards even more closely than those of its government customers–include Bank of America and News Corp. Private-sector deals now account for close to 60% of the company’s revenue, which FORBES estimates will hit $450 million this year, up from less than $300 million last year. Karp projects Palantir will sign a billion dollars in new, long-term contracts in 2014, a year that may also bring the company its first profits.
The bottom line: A CIA-funded firm run by an eccentric philosopher has become one of the most valuable private companies in tech, priced at between $5 billion and $8 billion in a round of funding the company is currently pursuing. Karp owns roughly a tenth of the firm–just less than its largest stakeholder, Peter Thiel, the PayPal and Facebook billionaire. (Other billionaire investors include Ken Langone and hedge fund titan Stanley Druckenmiller.) That puts Karp on course to become Silicon Valley’s latest billionaire–and Thiel could double his fortune–if the company goes public, a possibility Karp says Palantir is reluctantly considering.
The biggest problem for Palantir’s business may be just how well its software works: It helps its customers see too much. In the wake of NSA leaker Edward Snowden’s revelations of the agency’s mass surveillance, Palantir’s tools have come to represent privacy advocates’ greatest fears of data-mining technology — Google-level engineering applied directly to government spying. That combination of Big Brother and Big Data has come into focus just as Palantir is emerging as one of the fastest-growing startups in the Valley, threatening to contaminate its first public impressions and render the firm toxic in the eyes of customers and investors just when it needs them most.
“They’re in a scary business,” says Electronic Frontier Foundation attorney Lee Tien. ACLU analyst Jay Stanley has written that Palantir’s software could enable a “true totalitarian nightmare, monitoring the activities of innocent Americans on a mass scale.”
Karp, a social theory Ph.D., doesn’t dodge those concerns. He sees Palantir as the company that can rewrite the rules of the zero-sum game of privacy and security. “I didn’t sign up for the government to know when I smoke a joint or have an affair,” he acknowledges. In a company address he stated, “We have to find places that we protect away from government so that we can all be the unique and interesting and, in my case, somewhat deviant people we’d like to be.”
Karp with billionaire co-founder Peter Thiel at the Sun Valley conference in 2009. “No one was doing… [+] anything like Palantir,” says Thiel, who believed from the beginning “it was going to be as valuable as Facebook.” (Credit: Allen & Co.)
Karp with billionaire co-founder Peter Thiel at the Sun Valley conference in 2009. “No one was doing… [+]
Palantir boasts of technical safeguards for privacy that go well beyond the legal requirements for most of its customers, as well as a team of “privacy and civil liberties engineers.” But it’s Karp himself who ultimately decides the company’s path. “He’s our conscience,” says senior engineer Ari Gesher.
The question looms, however, of whether business realities and competition will corrupt those warm and fuzzy ideals. When it comes to talking about industry rivals, Karp often sounds less like Palantir’s conscience than its id. He expressed his primary motivation in his July company address: to “kill or maim” competitors like IBM and Booz Allen. “I think of it like survival,” he said. “We beat the lame competition before they kill us.”
KARP SEEMS TO enjoy listing reasons he isn’t qualified for his job. “He doesn’t have a technical degree, he doesn’t have any cultural affiliation with the government or commercial areas, his parents are hippies,” he says, manically pacing around his office as he describes himself in the third person. “How could it be the case that this person is cofounder and CEO since 2005 and the company still exists?”
The answer dates back to Karp’s decades-long friendship with Peter Thiel, starting at Stanford Law School. The two both lived in the no-frills Crothers dorm and shared most of their classes during their first year, but held starkly opposite political views. Karp had grown up in Philadelphia, the son of an artist and a pediatrician who spent many of their weekends taking him to protests for labor rights and against “anything Reagan did,” he recalls. Thiel had already founded the staunchly libertarian Stanford Review during his time at the university as an undergrad.
“We would run into each other and go at it … like wild animals on the same path,” Karp says. “Basically I loved sparring with him.”
With no desire to practice law, Karp went on to study under Jurgen Habermas, one of the 20th century’s most prominent philosophers, at the University of Frankfurt. Not long after obtaining his doctorate, he received an inheritance from his grandfather, and began investing it in startups and stocks with surprising success. Some high-net-worth individuals heard that “this crazy dude was good at investing” and began to seek his services, he says. To manage their money he set up the London-based Caedmon Group, a reference to Karp’s middle name, the same as the first known English-language poet.
Back in Silicon Valley Thiel had cofounded PayPal and sold it to eBay in October 2002 for $1.5 billion. He went on to create a hedge fund called Clarium Capital but continued to found new companies: One would become Palantir, named by Thiel for the Palantiri seeing stones from J.R.R. Tolkien’s Lord of the Rings, orbs that allow the holder to gaze across vast distances to track friends and foes.
In a post-9/11 world Thiel wanted to sell those Palantiri-like powers to the growing national security complex: His concept for Palantir was to use the fraud-recognition software designed for PayPal to stop terrorist attacks. But from the beginning the libertarian saw Palantir as an antidote to–not a tool for–privacy violations in a society slipping into a vise of security. “It was a mission-oriented company,” says Thiel, who has personally invested $40 million in Palantir and today serves as its chairman. “I defined the problem as needing to reduce terrorism while preserving civil liberties.”
In 2004 Thiel teamed up with Joe Lonsdale and Stephen Cohen, two Stanford computer science grads, and PayPal engineer Nathan Gettings to code together a rough product. Initially they were bankrolled entirely by Thiel, and the young team struggled to get investors or potential customers to take them seriously. “How the hell do you get them to listen to 22-year-olds?” says Lonsdale. “We wanted someone to have a little more gray hair.”
Enter Karp, whose Krameresque brown curls, European wealth connections and Ph.D. masked his business inexperience. Despite his nonexistent tech background, the founders were struck by his ability to immediately grasp complex problems and translate them to nonengineers.
Lonsdale and Cohen quickly asked him to become acting CEO, and as they interviewed other candidates for the permanent job, none of the starched-collar Washington types or M.B.A.s they met impressed them. “They were asking questions about our diagnostic of the total available market,” says Karp, disdaining the B-school lingo. “We were talking about building the most important company in the world.”
While Karp attracted some early European angel investors, American venture capitalists seemed allergic to the company. According to Karp, Sequoia Chairman Michael Moritz doodled through an entire meeting. A Kleiner Perkins exec lectured the Palantir founders on the inevitable failure of their company for an hour and a half.
Palantir was rescued by a referral to In-Q-Tel, the CIA’s venture arm, which would make two rounds of investment totaling more than $2 million. (See our sidebar on In-Q-Tel’s greatest hits.) “They were clearly top-tier talent,” says former In-Q-Tel executive Harsh Patel. “The most impressive thing about the team was how focused they were on the problem … how humans would talk with data.”
Karp in Palantir’s Palo Alto offices. (Credit: Eric Millette for Forbes)
That mission turned out to be vastly more difficult than any of the founders had imagined. PayPal had started with perfectly structured and organized information for its fraud analysis. Intelligence customers, by contrast, had mismatched collections of e-mails, recordings and spreadsheets.
To fulfill its privacy and security promises, Palantir needed to catalog and tag customers’ data to ensure that only users with the right credentials could access it. This need-to-know system meant classified information couldn’t be seen by those without proper clearances–and was also designed to prevent the misuse of sensitive personal data.
But Palantir’s central privacy and security protection would be what Karp calls, with his academic’s love of jargon, “the immutable log.” Everything a user does in Palantir creates a trail that can be audited. No Russian spy, jealous husband or Edward Snowden can use the tool’s abilities without leaving an indelible record of his or her actions.
From 2005 to 2008 the CIA was Palantir’s patron and only customer, alpha-testing and evaluating its software. But with Langley’s imprimatur, word of Palantir’s growing abilities spread, and the motley Californians began to bring in deals and recruits. The philosopher Karp turned out to have a unique ability to recognize and seduce star engineers. His colleagues were so flummoxed by his nose for technical talent that they once sent a pair of underwhelming applicants into a final interview with Karp as a test. He smelled both out immediately.
A unique Palantir culture began to form in Karp’s iconoclast image. Its Palo Alto headquarters, which it calls “the Shire” in reference to the homeland of Tolkien’s hobbits, features a conference room turned giant plastic ball pit and has floors littered with Nerf darts and dog hair. (Canines are welcome.) Staffers, most of whom choose to wear Palantir-branded apparel daily, spend so much time at the office that some leave their toothbrushes by the bathroom sinks.
Karp himself remains the most eccentric of Palantir’s eccentrics. The lifelong bachelor, who says that the notion of settling down and raising a family gives him “hives,” is known for his obsessive personality: He solves Rubik’s cubes in less than three minutes, swims and practices the meditative art of Qigong daily and has gone through aikido and jujitsu phases that involved putting cofounders in holds in the Shire’s hallways. A cabinet in his office is stocked with vitamins, 20 pairs of identical swimming goggles and hand sanitizer. And he addresses his staff using an internal video channel called KarpTube, speaking on wide-ranging subjects like greed, integrity and Marxism. “The only time I’m not thinking about Palantir,” he says, “is when I’m swimming, practicing Qigong or during sexual activity.”
In 2010 Palantir’s customers at the New York Police Department referred the company to JPMorgan, which would become its first commercial customer. A team of engineers rented a Tribeca loft, sleeping in bunk beds and working around the clock to help untangle the bank’s fraud problems. Soon they were given the task of unwinding its toxic mortgage portfolio. Today Palantir’s New York operation has expanded to a full, Batman-themed office known as Gotham, and its lucrative financial-services practice includes everything from predicting foreclosures to battling Chinese hackers.
As its customer base grew, however, cracks began to show in Palantir’s idealistic culture. In early 2011 e-mails emerged that showed a Palantir engineer had collaborated on a proposal to deal with a WikiLeaks threat to spill documents from Bank of America. The Palantir staffer had eagerly agreed in the e-mails to propose tracking and identifying the group’s donors, launching cyberattacks on WikiLeaks’ infrastructure and even threatening its sympathizers. When the scandal broke, Karp put the offending engineer on leave and issued a statement personally apologizing and pledging the company’s support of “progressive values and causes.” Outside counsel was retained to review the firm’s actions and policies and, after some deliberation, determined it was acceptable to rehire the offending employee, much to the scorn of the company’s critics.
Following the WikiLeaks incident, Palantir’s privacy and civil liberties team created an ethics hotline for engineers called the Batphone: Any engineer can use it to anonymously report to Palantir’s directors work on behalf of a customer they consider unethical. As the result of one Batphone communication, for instance, the company backed out of a job that involved analyzing information on public Facebook pages. Karp has also stated that Palantir turned down a chance to work with a tobacco firm, and overall the company walks away from as much as 20% of its possible revenue for ethical reasons. (It remains to be seen whether the company will be so picky if it becomes accountable to public shareholders and the demand for quarterly results.)
Still, according to former employees, Palantir has explored work in Saudi Arabia despite the staff’s misgivings about human rights abuses in the kingdom. And for all Karp’s emphasis on values, his apology for the WikiLeaks affair also doesn’t seem to have left much of an impression in his memory. In his address to Palantir engineers in July he sounded defiant: “We’ve never had a scandal that was really our fault.”
AT 4:07 P.M. ON NOV. 14, 2009 Michael Katz-Lacabe was parking his red Toyota Prius in the driveway of his home in the quiet Oakland suburb of San Leandro when a police car drove past. A license plate camera mounted on the squad car silently and routinely snapped a photo of the scene: his off-white, single-floor house, his wilted lawn and rosebushes, and his 5- and 8-year-old daughters jumping out of the car.
Katz-Lacabe, a gray-bearded and shaggy-haired member of the local school board, community activist and blogger, saw the photo only a year later: In 2010 he learned about the San Leandro Police Department’s automatic license plate readers, designed to constantly photograph and track the movements of every car in the city. He filed a public records request for any images that included either of his two cars. The police sent back 112 photos. He found the one of his children most disturbing.
“Who knows how many other people’s kids are captured in these images?” he asks. His concerns go beyond a mere sense of parental protection. “With this technology you can wind back the clock and see where everyone is, if they were parked at the house of someone other than their wife, a medical marijuana clinic, a Planned Parenthood center, a protest.”
San Leandro, Calif. community activist Michael Katz-Lacabe has taken a stand against cops using… [+] Palantir to analyze license plate photos of millions of unsuspecting drivers. (Credit: Eric Millette for Forbes)
San Leandro, Calif. community activist Michael Katz-Lacabe has taken a stand against cops using… [+]
As Katz-Lacabe dug deeper, he found that the millions of pictures collected by San Leandro’s license plate cameras are now passed on to the Northern California Regional Intelligence Center (NCRIC), one of 72 federally run intelligence fusion organizations set up after 9/11. That’s where the photos are analyzed using software built by a company just across San Francisco Bay: Palantir.
In the business proposal that Palantir sent NCRIC, it offered customer references that included the Los Angeles and New York police departments, boasting that it enabled searches of the NYPD’s 500 million plate photos in less than five seconds. Katz-Lacabe contacted Palantir about his privacy concerns, and the company responded by inviting him to its headquarters for a sit-down meeting. When he arrived at the Shire, a pair of employees gave him an hourlong presentation on Palantir’s vaunted safeguards: its access controls, immutable logs and the Batphone.
Katz-Lacabe wasn’t impressed. Palantir’s software, he points out, has no default time limits–all information remains searchable for as long as it’s stored on the customer’s servers. And its auditing function? “I don’t think it means a damn thing,” he says. “Logs aren’t useful unless someone is looking at them.”
When Karp hears Katz-Lacabe’s story, he quickly parries: Palantir’s software saves lives. “Here’s an actual use case,” he says and launches into the story of a pedophile driving a “beat-up Cadillac” who was arrested within an hour of assaulting a child, thanks to NYPD license plate cameras. “Because of the license-plate-reader data they gathered in our product, they pulled him off the street and saved human children lives.”
“If we as a democratic society believe that license plates in public trigger Fourth Amendment protections, our product can make sure you can’t cross that line,” he says, adding that there should be time limits on retaining such data. Until the law changes, though, Palantir will play within those rules. “In the real world where we work–which is never perfect–you have to have trade-offs.”
And what if Palantir’s audit logs–its central safeguard against abuse–are simply ignored? Karp responds that the logs are intended to be read by a third party. In the case of government agencies, he suggests an oversight body that reviews all surveillance–an institution that is purely theoretical at the moment. “Something like this will exist,” Karp insists. “Societies will build it, precisely because the alternative is letting terrorism happen or losing all our liberties.”
Palantir’s critics, unsurprisingly, aren’t reassured by Karp’s hypothetical court. Electronic Privacy Information Center activist Amie Stepanovich calls Palantir “naive” to expect the government to start policing its own use of technology. The Electronic Frontier Foundation’s Lee Tien derides Karp’s argument that privacy safeguards can be added to surveillance systems after the fact. “You should think about what to do with the toxic waste while you’re building the nuclear power plant,” he argues, “not some day in the future.”
Some former Palantir staffers say they felt equally concerned about the potential rights violations their work enabled. “You’re building something that could absolutely be used for malice. It would have been a nightmare if J. Edgar Hoover had these capabilities in his crusade against Martin Luther King,” says one former engineer. “One thing that really troubled me was the concern that something I contribute to could prevent an Arab Spring-style revolution.”
Despite Palantir’s lofty principles, says another former engineer, its day-to-day priorities are satisfying its police and intelligence customers: “Keeping good relations with law enforcement and ‘keeping the lights on’ bifurcate from the ideals.”
He goes on to argue that even Palantir’s founders don’t quite understand the Palantiri seeing stones in The Lord of the Rings . Tolkien’s orbs, he points out, didn’t actually give their holders honest insights. “The Palantiri distort the truth,” he says. And those who look into them, he adds, “only see what they want to see.”
DESPITE WHAT any critic says, it’s clear that Alex Karp does indeed value privacy–his own.
His office, decorated with cardboard effigies of himself built by Palantir staff and a Lego fortress on a coffee table, overlooks Palo Alto’s Alma Street through two-way mirrors. Each pane is fitted with a wired device resembling a white hockey puck. The gadgets, known as acoustic transducers, imperceptibly vibrate the glass with white noise to prevent eavesdropping techniques, such as bouncing lasers off windows to listen to conversations inside.
He’s reminiscing about a more carefree time in his life–years before Palantir–and has put down his Rubik’s cube to better gesticulate. “I had $40,000 in the bank, and no one knew who I was. I loved it. I loved it. I just loved it. I just loved it!” he says, his voice rising and his hands waving above his head. “I would walk around, go into skanky places in Berlin all night. I’d talk to whoever would talk to me, occasionally go home with people, as often as I could. I went to places where people were doing things, smoking things. I just loved it.”
“One of the things I find really hard and view as a massive drag … is that I’m losing my ability to be completely anonymous.”
It’s not easy for a man in Karp’s position to be a deviant in the modern world. And with tools like Palantir in the hands of the government, deviance may not be easy for the rest of us, either. With or without safeguards, the “complete anonymity” Karp savors may be a 20th-century luxury.
Karp lowers his arms, and the enthusiasm drains from his voice: “I have to get over this.”
XIX. Does Palantir See Too Much- Oct. 29, 2020, New York Times
Does Palantir See Too Much?
The tech giant helps governments and law enforcement decipher vast amounts of data — to mysterious and, some say, dangerous ends.
By Michael Steinberger
On a bright Tuesday afternoon in Paris last fall, Alex Karp was doing tai chi in the Luxembourg Gardens. He wore blue Nike sweatpants, a blue polo shirt, orange socks, charcoal-gray sneakers and white-framed sunglasses with red accents that inevitably drew attention to his most distinctive feature, a tangle of salt-and-pepper hair rising skyward from his head.
Under a canopy of chestnut trees, Karp executed a series of elegant tai chi and qigong moves, shifting the pebbles and dirt gently under his feet as he twisted and turned. A group of teenagers watched in amusement. After 10 minutes or so, Karp walked to a nearby bench, where one of his bodyguards had placed a cooler and what looked like an instrument case. The cooler held several bottles of the nonalcoholic German beer that Karp drinks (he would crack one open on the way out of the park). The case contained a wooden sword, which he needed for the next part of his routine. “I brought a real sword the last time I was here, but the police stopped me,” he said matter of factly as he began slashing the air with the sword.
Those gendarmes evidently didn’t know that Karp, far from being a public menace, was the chief executive of an American company whose software has been deployed on behalf of public safety in France. The company, Palantir Technologies, is named after the seeing stones in J.R.R. Tolkien’s “The Lord of the Rings.” Its two primary software programs, Gotham and Foundry, gather and process vast quantities of data in order to identify connections, patterns and trends that might elude human analysts. The stated goal of all this “data integration” is to help organizations make better decisions, and many of Palantir’s customers consider its technology to be transformative. Karp claims a loftier ambition, however. “We built our company to support the West,” he says. To that end, Palantir says it does not do business in countries that it considers adversarial to the U.S. and its allies, namely China and Russia. In the company’s early days, Palantir employees, invoking Tolkien, described their mission as “saving the shire.”
The brainchild of Karp’s friend and law-school classmate Peter Thiel, Palantir was founded in 2003. It was seeded in part by In-Q-Tel, the C.I.A.’s venture-capital arm, and the C.I.A. remains a client. Palantir’s technology is rumored to have been used to track down Osama bin Laden — a claim that has never been verified but one that has conferred an enduring mystique on the company. These days, Palantir is used for counterterrorism by a number of Western governments. French intelligence turned to Palantir following the November 2015 terror attacks in Paris. Karp claims that Palantir has helped thwart several attacks, including one or two that he says could have had seismic political consequences. “I believe that Western civilization has rested on our somewhat small shoulders a couple of times in the last 15 years,” he told me in Paris, where he was hosting a conference for Palantir’s corporate clients.
A few months later, the world was being menaced by a novel coronavirus, and Palantir quickly joined that battle against Covid-19: By April, according to the company, approximately a dozen countries were using its technology to track and contain the virus. The speed with which Palantir transitioned to pandemic response ostensibly underscores the flexibility of its software, which can be put to any number of tasks. The U.S. Army uses it for logistics, among other things. The investment bank Credit Suisse uses it to guard against money laundering. The pharmaceutical company Merck, in Germany, uses it to expedite the development of new drugs. Ferrari Scuderia uses it to try to make its Formula 1 cars faster. To Palantirians, as some call themselves, these myriad applications are just further proof that many problems are data-integration problems.
Yet Palantir’s work on the coronavirus has also highlighted the mistrust that trails the company. In Europe, it is viewed with suspicion because of the C.I.A. connection. But the main source of apprehension is simply the nature of Palantir’s work. Although Palantir claims it does not store or sell client data and has incorporated into its software what it insists are robust privacy controls, those who worry about the sanctity of personal information see Palantir as a particularly malignant avatar of the Big Data revolution. Karp himself doesn’t deny the risk. “Every technology is dangerous,” he says, “including ours.” The fact that the health records of millions of people are now being funneled through Palantir’s software has only added to the unease.
That’s especially true in the United States, where the Department of Health and Human Services is using Palantir’s software to analyze virus-related data. Palantir’s work with H.H.S. has become bound up in the biggest controversy that the company has faced, over its relationship with United States Immigration and Customs Enforcement. Progressive activists and members of Congress have expressed fear that the information collected by H.H.S. could be used by the Trump administration to expand its immigration crackdown, in which Palantir’s technology has played a part. And the fact that Palantir was awarded a pair of no-bid contracts valued at nearly $25 million by H.H.S. has amplified concerns that it has benefited from Thiel’s support of President Trump. Thiel was one of his most prominent backers in 2016, even speaking at the Republican National Convention.
Palantir’s perceived links to the president have made it an object of suspicion among liberals, which frustrates Karp. In contrast to Thiel, the 53-year-old Karp is a self-described “progressive warrior” who says he voted for Hillary Clinton and who has expressed antipathy for Trump. His greatest fear, he says, is the rise of fascism. Although Karp’s political views are widely shared in Silicon Valley, he is one of the tech industry’s unlikeliest chief executives. He co-founded Palantir with no background in computer science or business. Instead, he holds a law degree from Stanford University and a doctorate in social theory from Goethe University in Frankfurt, where for a time his thesis adviser was Jürgen Habermas, possibly Europe’s most celebrated living social philosopher. On the corporate scene, Karp is a sui generis figure, a fact vividly on display that autumn afternoon in the Luxembourg Gardens.
Until recently, it could be argued that his intellectual pedigree and political leanings were a kind of shield for Palantir, deflecting criticism of its work — or at least keeping critics off balance. But fairly or not, Palantir has come to be regarded as an enabler and prime beneficiary of Trump’s presidency, which has rendered the company toxic in the eyes of many progressives. In response to the criticism of Palantir’s relationship with ICE, Karp has attacked the tech industry over what he sees as its insufficient patriotism. Palantir recently relocated its headquarters from Palo Alto to Denver, a move that seemed partly rooted in the contempt that Karp and Thiel have for Silicon Valley. The company, which has yet to turn a profit, went public last month amid concerns that its prospects in Washington could be diminished under a Biden administration. Palantir says that its software solves “the world’s hardest problems.” Removing the stain of Trumpism may prove to be an especially hard one.
Alex Karp, the chief executive of Palantir.Antoine d’Agata/Magnum Photos
Speaking at a tech conference in 2010, Eric Schmidt, Google’s chief executive at the time, made a startling observation. “There were five exabytes of information created by the entire world between the dawn of civilization and 2003. Now that same amount of information is created every two days,” he said. (An exabyte is equivalent to one billion gigabytes.) It was perhaps a slightly exaggerated claim in the service of an indisputable fact: Humanity is now awash in data. The premise of Big Data is that all of this information can yield powerful insights. But the difficulty is harnessing the data, which is where Palantir comes in. Although Palantir has glamorous clients and offices in upscale locales (the Marais in Paris, Soho Square in London, the Georgetown section of Washington), in tech circles, data integration is not considered particularly sexy. “It’s plumbing work, basically,” Louis Mosley, who runs Palantir’s London office, told me with a smile.
He was being modest. What Palantir does is a little more complex than unclogging a toilet. Essentially, Palantir’s software synthesizes the data that an organization collects. It could be five or six types of data; it could be hundreds. The challenge is that each type of information — phone numbers, trading records, tax returns, photos, text messages — is often formatted differently from the others and siloed in separate databases. Building virtual pipelines, Palantir engineers merge all the information into a single platform. They work quickly. According to Jose Arrieta, who was H.H.S.’s chief information officer until two months ago, Palantir merged around two billion data elements related to the Covid-19 outbreak in less than three weeks. Once the data has been integrated, it can be presented in the form of tables, graphs, timelines, heat maps, artificial-intelligence models, histograms, spider diagrams and geospatial analysis. It is a digital panopticon, and having sat through several Palantir demos, I can report that the interface is impressive — the search results are strikingly elegant and easy to understand.
Those appealing visuals were conceived in order to hunt and kill terrorists. In 1998, Thiel co-founded PayPal, then served as its chief executive from 2000 until it was acquired by eBay in 2002. Not long after 9/11 — Thiel can’t recall exactly when — it occurred to him that PayPal’s anti-fraud algorithms could possibly help the U.S. government combat terrorism. In 2003, Thiel asked a trio of software engineers, including two from PayPal, to create a prototype. His intuition plus their coding gave rise to Palantir. While Thiel provided most of the early money, the start-up secured an estimated $2 million from In-Q-Tel, a venture-capital firm that finances the development of technologies that can help the C.I.A.
Karp says the real value of the In-Q-Tel investment was that it gave Palantir access to the C.I.A. analysts who were its intended clients. According to Palantir, every two weeks, Aki Jain, one of the first engineers hired by Thiel, and Stephen Cohen, an engineer who had worked at Thiel’s hedge fund, Clarion Capital Partners, traveled from Palo Alto to Langley with an updated version of the software program. (Cohen recalls the C.I.A. guys’ referring to him as “Two Weeks.”) The C.I.A. analysts would test it out and offer feedback, and then Cohen and Jain would fly back to California to tweak it. Jain estimates that from 2005 to 2009, he and Cohen made around 200 trips to Virginia. The iterative approach became standard practice for Palantir — even now, it embeds what it calls “forward-deployed engineers” with clients to customize the software to their needs, which has led some observers to conclude that Palantir is as much a consultancy as it is a software maker.
Although Palantir is often depicted as a kind of omnipotent force, it is actually quite small, with around 2,400 employees. By contrast, Facebook, which seems to vie with Palantir for the worst headlines these days, has more than 50,000. (Thiel was the first outside investor in Facebook and remains a member of its board.) And while Palantir’s reach feels tentacular, the prospectus that it filed with the Securities and Exchange Commission before going public revealed that it has just 125 customers, a number that surprised some observers and raised questions about the company’s growth prospects. In mid-October, Palantir stock was trading around $10 per share, and its market capitalization was nearly $16 billion.
Palantir is pricey — customers pay $10 million to $100 million annually — and not everyone is enamored of the product. Home Depot, Hershey, Coca-Cola and American Express all dropped Palantir after using it. Even within the intelligence community, there seem to be mixed opinions. Three years ago, BuzzFeed obtained a leaked video in which Karp told Palantir employees that the company’s relationship with the National Security Agency had ended. Several former C.I.A. analysts told me that they and their colleagues were underwhelmed by Palantir. But the C.I.A. is a big place, and others who worked there extolled it.
Some clients seem to believe Palantir’s software is essential. One is the aerospace manufacturer Airbus, which hired Palantir in 2016 when it was ramping up production of its new A350 jet. Marc Fontaine, who until recently was Airbus’s digital-transformation officer, told me that when you go from a single plane on the assembly line to 10, “the complexity increases exponentially, and it kills you.” Missing parts, faulty parts, production mistakes, communications glitches — those and other problems inevitably slow down the assembly process and cause millions of dollars in cost overruns. They can also result in penalties and damages that have to be paid to airlines awaiting delivery.
In 2016, five Palantir engineers embedded in the Airbus factory in Toulouse, France. Using Foundry, Palantir’s commercial application — Gotham, its other flagship software program, is for national security and defense — they merged 25 data silos related to production of the A350 and integrated more than 400 sets of data. Palantir produced results immediately. Before it came on board, Fontaine says, it took an average of 24 days to fix production mistakes; Palantir helped cut that to 17. Airbus realized several hundred million dollars in cost savings.
These days, around 15,000 Airbus employees use Palantir, and its software has essentially wired the entire Airbus ecosystem through a venture called Skywise, which collects and analyzes data from around 130 airlines worldwide. The information is used for everything from improving on-time performance to preventive maintenance. Fontaine says that Airbus was always open to using other data-analytics tools, but “we didn’t find anything equivalent at the time to Palantir.” Its software, he says, “has unique capability.” His former boss, Tom Enders, who was Airbus’s chief executive from 2012 to 2019, echoes that praise. He calls bringing in Palantir “one of the best decisions of my career.”
Karp, standing, with Palantir employees: Dave Glazer, Sara Peletz and Mayer Schein. The portrait on the wall is Michel Foucault, the French philosopher.Antoine d’Agata/Magnum Photos
‘‘I still can’t believe I haven’t been shot and pushed out the window,” Karp told me. We were in Palantir’s New York office, located in the Meatpacking district. He wasn’t being literal, despite the office’s bulletproof windows and the bodyguards hovering nearby. Rather, he meant the feeling of inevitable doom that has plagued him since childhood. Karp grew up in the Philadelphia area. His parents are Dr. Robert Karp, a clinical pediatrician, and Leah Jaynes Karp, an artist. His father is Jewish; his mother is African-American. (Karp has a brother and two stepsiblings.) He told me that his parents were “hippies” and that he spent a lot of time as a kid at political protests. He intuited from a young age that his background made him vulnerable, he said. “You’re a racially amorphous, far-left Jewish kid who’s also dyslexic — would you not come up with the idea that you’re [expletive]?” Although he was now the head of a major corporation, neither time nor success had diminished the anxiety. If the far right came to power, he said, he would certainly be among its victims. “Who’s the first person who is going to get hung? You make a list, and I will show you who they get first. It’s me. There’s not a box I don’t check.” His fear, he said, “propels a lot of the decisions for this company.”
Given the political milieu in which he was raised, Haverford College, a school with Quaker roots near Philadelphia with a robust tradition of dissent (it was a hive of antiwar activity in the 1960s and 1970s), was a natural fit for Karp. We happened to be classmates there, but despite the college’s small size (currently around 1,200 students), he and I somehow never exchanged a word in four years. Karp was, by his own admission, somewhat introverted and also very studious. The library didn’t see much of me, which may go some way to explaining why he ended up a billionaire and I did not. Over conversations in New York, Washington, Paris and Vermont, we found that we had a lot to talk about, although I can’t say it is regrettable that we never connected at Haverford; I am not sure that 20-year-old me would have fully appreciated his bracing intelligence, and I suspect that my talent for procuring beer and organizing Roman-themed parties would have been of little use to him.
After graduating, Karp went to Stanford Law School, which he hated — “the worst three years of my adult life.” He says he knew within a week of enrolling that he had made a mistake. In his view, Stanford was just a glorified trade school; his classmates were mainly animated by a desire to land prestigious jobs, and the intellectual discourse was “highly performative,” as he puts it. What made Stanford bearable was his unlikely friendship with Thiel, a classmate. They bonded over their shared disdain for law school and a love of political debate. Thiel had already achieved some prominence for his libertarian views — as a Stanford undergraduate, he had helped found the right-leaning Stanford Review — and he and Karp spent much of their free time interrogating each other’s positions. “We argued like feral animals,” Karp recalled. According to Thiel, their conversations generally took place late at night in the law-school dorm. “It sounds too self-aggrandizing, but I think we were both genuinely interested in ideas,” he says. “He was more the socialist, I was more the capitalist. He was always talking about Marxist theories of alienated labor and how this was true
Karp didn’t even stick around for his Stanford graduation: As soon as classes ended, he left for Frankfurt to begin studying German. His aim was to earn a doctorate in Germany, an ambition kindled mainly by the fact that most of the writers and thinkers he was drawn to were German. After six months, he had mastered enough of the language — despite his dyslexia — to gain admission to Goethe University in Frankfurt. Having Jürgen Habermas as his Ph.D. thesis adviser was a big deal. Habermas was affiliated with the university’s Institute for Social Research, which had given rise to the so-called Frankfurt School, a neo-Marxist movement renowned for its critique of capitalism and culture. In Karp’s words, “If you can get Habermas to work with you for even two minutes, you can be a tenured professor at Columbia.”
But Karp says he had a falling out with Habermas over his dissertation topic and ended up switching advisers. When I first asked him to describe his thesis, which he wrote in German, he said that it “rebuilt the Parsonian framework to account for the somewhat irrational philosophy of Adorno, basically.” When I later asked for an explanation that I could perhaps understand, he told me that it was about the German writer Martin Walser’s controversial 1998 speech on the limits of wartime guilt and “a parochial form of fascism that occurs by purposely saying things that are incorrect in speech.” (“Parsonian” is a reference to the American sociologist Talcott Parsons; Theodor W. Adorno was a German philosopher and sociologist.) Karp said that although his collaboration with Habermas ended prematurely, it was clarifying. He realized that, however gifted a scholar he might have been, he could never attain the stature of Habermas. “Working with Habermas showed me that I couldn’t be him and didn’t want to be him,” he says.
While his second advanced degree also failed to yield a career path, it had an unexpected dividend: He developed a deep affinity for Germany. “I went for intellectual reasons,” he says. “The reason I stayed was emotional.” He found that he was good at what he calls “German conceptual thinking” but also felt a sense of belonging in Germany — that he fit in even as he recognized that his Jewishness would always set him apart. He still feels that way. “I have a second home, and it’s called Germany and the German-speaking world,” he told me. “I’m more naturally accepted there than anywhere else in the world.” The years that he spent in Germany are the touchstone of his life. “I only made two good decisions as an adult: going to Germany and starting Palantir,” he said. “Everything else was, I wouldn’t call it a mistake, but it was either preparation for these two decisions or a mistake.”
After finishing his dissertation, Karp founded a money-management firm. His goal was to accumulate a $250,000 nest egg and to settle in Berlin, where he planned to live as a highbrow dilettante, combining intellectual pursuits with various “forms of debauchery.” But then Thiel reached out to him. Thiel thought that Palantir might be a tough sell to potential clients, at least initially — there would be skepticism about the software, as well as bureaucratic resistance — and that the fledgling company needed a persuasive frontman with a sophisticated mind. “I am not sure that Alex was the perfect person for it, but he was by far the best person I knew,” Thiel told me. “You needed someone who was smart, scrappy, who — I think he has a terrific sense for people. I think he’s incredibly tenacious.”
Still, Karp was not an obvious choice to run a tech firm or any company, for that matter. Even though he has now been Palantir’s chief executive for 17 years and is a celebrity at Davos and other elite gatherings, in some ways he still seems ill suited to the task, a point he readily concedes. He is a lifelong bachelor who is drawn to solitary pursuits — his chief pastime is cross-country skiing (he will do 40 to 60 kilometers a day when time and weather permit). He doesn’t like to give speeches or do interviews, and you will never see him prowling a stage in the way that, say, Steve Jobs once did. Backslapping and small talk are not his thing, either. “Most businesspeople have a slight politician inside them,” Karp said. “I don’t have that inside me.”
He said it would be helpful to Palantir if he were more “norm-conforming.” I asked what norm-conforming looked like. “The way I see your life,” he said. (I had filled him in on the details during a previous conversation.) I was a little disappointed to learn that my conventionality — wife, kids, dog — was so obvious, but I kept that to myself and asked if he thought he could eventually marry. Karp shook his head. “I fantasized about being norm-conforming, but I don’t know how to do that,” he said. “I just don’t know how to do that, I don’t know how it works, I wouldn’t know how to be not transgressive. I try. I try really hard, really I do … but it’s not working out.” (He did tell me later that he had a girlfriend in Germany.) I suggested that his idiosyncratic personality didn’t seem to be hurting Palantir. He disagreed. “We are an enterprise company with enterprise clients,” he said. “You think it is helpful having a fluorescent praying mantis coming into their office, telling them about German philosophy? Do you think that’s helpful? I can tell you, it’s not helpful.”
On the other hand, Karp had no doubt that he was the right person to lead Palantir internally. “Once I stumbled on it,” he said, “it turned out that I was built for certain things that are really valuable, like managing very complex, sometimes difficult — highly in many cases — technical software engineers. There are just very few people in the world built for that.” Among Palantirians, “Dr. Karp,” as he is known, commands something approaching reverence. He appears to be a loyal and generous boss. I also had the impression that his employees serve a loco familia function for him, which may go some way to explaining why, before the pandemic, he spent roughly 300 days a year on the road, circulating among Palantir’s 22 offices. And if, as he insists, his distinctive manner is off-putting to clients, Karp believes it is crucial to his ability to lead Palantir. “I manage the most eclectic, creative group of 2,400 people perhaps in the world,” he told me. “You need a way you can bond, and my eccentric, nonstandard character is the bonding mechanism.”
Karp taking a break out of his temporary offices. He does at least one hour of hiking in the morning.Antoine d’Agata/Magnum Photos
Karp and Thiel say they had two overarching ambitions for Palantir early on. The first was to make software that could help keep the country safe from terrorism. The second was to prove that there was a technological solution to the challenge of balancing public safety and civil liberties — a “Hegelian” aspiration, as Karp puts it. Although political opposites, they both feared that personal privacy would be a casualty of the war on terrorism. When I met with Thiel at his Los Angeles office, in a conference room with a commanding view of the Hollywood Hills, he used a whiteboard to illustrate those concerns. With a black marker, he drew a graph. At the end of one axis he wrote “Dick Cheney” and at the other end he wrote “A.C.L.U.” Cheney, he explained, represented “lots of security and no privacy” while the A.C.L.U. was “lots of privacy but little security.” Post 9/11, Thiel said, it seemed inevitable that the Cheney view would prevail. He then drew another axis, this one with “low-tech” at one end and “high-tech” at the other. “Low-tech” was a catchall for crude, highly intrusive technology. “High-tech,” he said, was more effective but also less invasive. Thiel’s fear was that we would end up with a combination of low-tech and Cheney, in which case civil liberties would likely be crushed. He said that he and Karp wanted to make software that could help save lives but also preserve privacy. “Maybe there were still trade-offs, but they were at a very different level,” he said.
To that end, Palantir’s software was created with two primary security features: Users are able to access only information they are authorized to view, and the software generates an audit trail that, among other things, indicates if someone has tried to obtain material off-limits to them. But the data, which is stored in various cloud services or on clients’ premises, is controlled by the customer, and Palantir says it does not police the use of its products. Nor are the privacy controls foolproof; it is up to the customers to decide who gets to see what and how vigilant they wish to be. The potential for abuse seems vast, especially in the United States, where digital-privacy laws are not nearly as stringent as in Europe. In 2018, Bloomberg Businessweek broke the story of a rogue JP Morgan Chase employee who had used Palantir’s software to spy on colleagues, reading their emails and tracking their movements. Even some of the bank’s senior executives were unknowingly surveilled.
Over the years, Palantir has been embroiled in several controversies that have raised doubts about its own trustworthiness. In 2011, the hacker collective Anonymous released emails it had taken from a third party showing that Palantir employees were involved in a proposed misinformation campaign to discredit WikiLeaks and to smear some of its supporters, notably Glenn Greenwald. Though no one was fired, Karp personally apologized to Greenwald. (When I asked Karp about the episode, he chalked it up to “growing pains.”) Palantir was also implicated in the Cambridge Analytica scandal. Christopher Wylie, the former Cambridge Analytica employee-turned-whistle-blower, claimed that Palantir helped the firm harvest Facebook data that was then used on behalf of the Trump campaign. Palantir, which has a policy of not working on elections, said the matter involved just one employee in its London office and that the person was fired.
For those made nervous by Palantir, the company’s work with police departments has been a source of particular worry. Of all the ways that Big Data can be used, perhaps none generates greater attention than predictive policing, in which quantitative analyses are used to identify places that seem especially prone to crime and individuals who are likely to commit or fall victim to a crime. To critics, data-driven policing encourages overly aggressive tactics and reinforces racial biases that have long plagued the criminal-justice system. Palantir’s effort to market its software to police departments can also be regarded as an example of how weapons originally meant for the war on terrorism are now being deployed on American streets. “This is a tool designed to enhance government surveillance now being redirected on the domestic population,” says Andrew Guthrie Ferguson, a professor of law at American University who has written extensively about policing and technology.
That said, Palantir has struggled to drum up business from police departments. The New York Police Department stopped using Palantir a few years ago, as did the New Orleans Police Department. Not long before, concerns had been raised about how the N.O.P.D. was using the data. These days, the only major metropolitan force using Palantir is the Los Angeles Police Department. Before traveling to Los Angeles last December, I reached out to the L.A.P.D., asking to interview officials about Palantir. My request was turned down. But Sarah Brayne, now an assistant professor of sociology at the University of Texas at Austin, had better luck.
In 2013, when Brayne was a doctoral candidate at Princeton researching the use of data in policing, members of the L.A.P.D. allowed her to study their deployment of new technologies. Over the next two years, she enjoyed considerable access to the department, interviewing dozens of officers and going on ride-alongs in patrol cars. It became apparent to her that Palantir’s software was having a significant impact. For instance, Palantir’s network analysis — its ability to identify a person’s friends, relatives, colleagues and other relations — was pulling people into the L.A.P.D.’s surveillance system who otherwise wouldn’t have been.
Brayne’s findings will be included in a book coming out next month called “Predict and Surveil.” In it, she quotes one L.A.P.D. captain who inadvertently confirmed the worst suspicions about the use of data analytics in policing. “Let’s say I have something going on with the medical-marijuana clinics where they’re getting robbed,” he told Brayne. “I can put in an alert to Palantir that says anything that has to do with medical marijuana plus robbery, plus male, Black, six foot. I like throwing the net out there, you know?” Racial profiling was just one obvious risk. Among the many data streams available to the L.A.P.D. via Palantir were automatic license-plate readers, and it was easy enough to conjure nightmare scenarios. A detective could conceivably use that information to squeeze a reluctant witness — say, by finding out he was having an affair. Someone in the L.A.P.D. could possibly keep tabs on his ex-wife’s comings and goings. Brayne told me that what most troubled her about the L.A.P.D.’s use of data was its opaqueness. “Digital surveillance is invisible,” she said. “How are you supposed to hold an institution accountable when you don’t know what they are doing?”
A great deal of the controversy that dogs Palantir can also be attributed to Thiel, whose activities have raised some doubt about his commitment to democratic society and fair play. In the past, Thiel has argued that democracy and economic freedom are incompatible and suggested that giving women the vote had undermined the latter. After Gawker reported that he was gay, he secretly financed the Hulk Hogan lawsuit that bankrupted the website. Last year, The Wall Street Journal reported that Thiel had been urging Mark Zuckerberg not to censor political ads on Facebook. Thiel’s comments and activities occasionally get in the way of Palantir’s messaging. Karp gave a talk in Washington in September last year in which he said that the only justifiable use of facial-recognition technology by law enforcement was to exonerate people. A few months later, The Times reported that Thiel had helped finance a start-up called Clearview AI, whose facial-recognition app was being used by police departments around the country to charge individuals with crimes. Thiel’s investment in Clearview seemed to contradict Karp’s position and also raised questions about the sincerity of the views he had expressed regarding civil liberties and privacy.
When I asked Thiel about the risk of abuse with Palantir, he answered by referring to the company’s literary roots. “The Palantir device in the Tolkien books was a very ambiguous device in some ways,” he said. “There were a lot of people who looked into it and saw more than they should see, and things went badly wrong when they did.” But that didn’t mean the Palantir itself was flawed. “The Tolkien point I always make is that at the end of the day, it was actually a good device that was critical to the plot of the whole story. The way it worked was that Aragorn looked into the Palantir, and he showed Sauron the sword with which the One Ring had been cut off Sauron’s fingers at the end of the Second Age. This convinced Sauron that Aragorn had the One Ring and caused Sauron to launch a premature attack that emptied out Mordor and enabled the hobbits to sneak in to destroy the One Ring.” He continued: “The plot action was driven by the Palantir being used for good, not for evil. This reflected Tolkien’s cosmology that something that was made by the good elves would ultimately be used for good.”
A moment later, he added: “That’s roughly how I see it, that it is ultimately good and still very dangerous. In some ways, I think that was reflected in the choice of the name.”
In the late aughts, Palantir began pitching its technology to the U.S. military. The Army had equipped its troops with a battlefield-intelligence platform that was doing a poor job of protecting them, but it had sunk billions of dollars into the system and was unreceptive to Palantir. So Palantir started offering its software directly to individual battalions in Iraq and Afghanistan. By the end of 2011, about three dozen units across the military were using Palantir, and some were raving about its ability to steer them clear of ambushes and roadside bombs. According to Fortune magazine, a few senior military figures had become fans, too, among them Gen. James Mattis, Lt. Gen. H.R. McMaster and Lt. Gen. Michael Flynn.
In 2012, the Army commissioned an assessment of Palantir. According to a draft of the report that Palantir produced during litigation, 96 percent of military personnel surveyed deemed Palantir’s software to be effective. But rather than embracing Palantir, officials appeared to ignore the report. Two years later, the Army finally conceded that the intelligence system it was providing to troops was inoperable and began soliciting bids to develop a replacement. It refused, however, to allow Palantir to take part because its software was an off-the-shelf product, and the Army was only willing to entertain proposals for building a new system from scratch. In June 2016, Palantir sued the Army, and three months later, a federal court ruled in its favor. The judge said the Army had acted in “an arbitrary and capricious manner” and ordered it to open up the competition to Palantir.
The protracted battle with the Army is now corporate lore at Palantir, a story that encapsulates how the company sees itself — the scrappy outsider, dedicated to ensuring that good software triumphs over bad. In truth, the saga was slightly more complicated than that. For one thing, Palantir hired lawyers and lobbyists to plead its case and cultivated some prominent allies, such as Senator John McCain. Jonathan Wong, a former Marine and now a policy researcher at the RAND Corporation, says that the Army wasn’t necessarily acting out of malice toward Palantir. It wanted a more comprehensive battlefield-intelligence system than Palantir was offering at the time, one that could be used against “what we are fighting today and what we will be facing tomorrow,” as he puts it. But Wong, whose dissertation at RAND focused in part on the early relationship between Palantir and the Pentagon, says that Palantir’s software was better for the counterinsurgency and counterterrorism challenges that the military was facing at the time.
The federal court’s decision was handed down eight days before Trump was elected president. Depending on how you see it, the timing was either merely coincidental or portentous. With Trump’s victory, Palantir was suddenly among the best-connected companies in Washington. Thiel had been one of Trump’s most prominent supporters, and Mattis, McMaster and Flynn all ended up with senior positions in the new administration. The Trump years have been a bonanza for Palantir. Since Trump took office, it has won military contracts worth billions, including an $800 million contract to build the replacement battlefield-intelligence system. Palantir also has contracts with a number of civilian departments and agencies, among them the I.R.S., the S.E.C. and the C.D.C. The U.S. government now accounts for around half its business.
There appear to have been no allegations of impropriety around the military contracts that Palantir has won under Trump. But the military procurement process has not been immune to the ethical concerns that have swirled around his presidency. Last year, Amazon filed a lawsuit claiming that it had been passed over for a $10 billion defense contract because the Pentagon had yielded to pressure from Trump, who had repeatedly attacked the company’s founder and chief executive, Jeff Bezos, and who had also publicly stated that he did not want Amazon to get the deal.
Karp told me the idea that Palantir had benefited from Thiel’s support of Trump was “completely ludicrous,” and he bemoaned “the unfairness it creates toward us.” Whatever good will Thiel enjoyed with Trump, he said, was offset by his own opposition. “I think they already know my views at the White House,” he said. “It’s true Peter is chairman, [but] I’m running the company, I don’t have close ties with the Trump administration.” Still, he acknowledged that he was worried about “the guilt by association thing” — the possibility that Palantir could be tarnished by its perceived links to Trump. Even so, he refused to back away from the most damaging connection, Palantir’s work with ICE.
Palantir’s client relationships are sometimes born in moments of crisis. That was true with French intelligence, and it was also the case with ICE, which sought Palantir’s assistance after one of its agents was assassinated by a Mexican drug cartel. According to the company, it took Palantir’s engineers 11 hours to merge all of the relevant data, and within two weeks the killers were identified and arrested. ICE subsequently awarded Palantir a contract to help manage the data of Homeland Security Investigations, or H.S.I., the ICE subdivision that handles drug smuggling, human trafficking, financial crimes and cybercrimes. Palantir’s relationship with ICE attracted little notice before Trump’s presidency. But it became deeply controversial as Trump made good on his campaign pledge to curb illegal immigration.
Initially, Palantir tried to deflect criticism by pointing out that its contracts were with H.S.I., not Enforcement and Removal Operations, or E.R.O., the subdivision that was spearheading Trump’s policy. “We do not work for E.R.O,” the company said in a statement to The Times in 2018. That may have been technically true, but it wrongly implied that Palantir was playing no part in the crackdown. In the years before, H.S.I. had supported E.R.O. in a continuing operation to arrest and possibly deport family members of undocumented children who were caught trying to cross the border. And last year, H.S.I. led a raid on food-processing plants in Mississippi in which nearly 700 people were arrested. Interviewed by CNBC at Davos in January, Karp appeared to concede that Palantir’s previous disavowals were no longer operative. “It’s a de minimis part of our work, finding people in our country who are undocumented,” he said.
But Jacinta González of the advocacy group Mijente contends that even that comment was “totally false” and that Palantir’s software has played an integral role. She notes that ICE itself describes Palantir’s software as “mission critical,” underscoring its importance to the government agency. She claims that in recent years, ICE raids on undocumented individuals became much more targeted — agents seem to know exactly whom they are looking for and where to find them, which had not always been the case. González says it was clear to her and her colleagues that ICE had somehow obtained access to a wealth of personal information about those individuals and had also acquired data-analytics capabilities that allowed it to operate with greater precision. With the help of a research firm that examined government documents, Mijente concluded that Palantir’s software was helping to power ICE’s crackdown. “[Palantir] created something tailor-made for ICE to be able to run the kind of raids it wants,” González says. “To say that they are not included in enforcement is kind of laughable.”
Last year, Mijente and other groups held protests outside Palantir’s offices in New York and Palo Alto, as well as outside Karp’s Palo Alto home (Mijente also organized demonstrations in the lead-up to Palantir’s recent public listing). Student organizations at colleges and universities across the country also spoke out against Palantir. For years, the company had sponsored a conference on privacy law held at the University of California, Berkeley. But the organizers dropped Palantir after participants pressured them to cut ties to the firm. There was also dissent within Palantir: More than 200 employees sent a letter to Karp expressing their concern over ICE. Thiel’s political activities weren’t helping. On one of the days that I was with Karp in Paris, Thiel co-hosted a fund-raiser for a former Kansas secretary of state, Kris Kobach, known for his hard-line anti-immigration position.
“Every technology is dangerous,” Karp says, “including ours.” Antoine d’Agata/Magnum Photos
A few weeks after I saw Karp in Paris, I visited him at a home that he owns in Vermont. When I drove up the dirt road leading to the cabin-style house, a couple of bodyguards greeted me. Karp’s personal assistant then came out and took me into the house, where Karp was waiting at the dining-room table. Suitcases were lined up against a wall. Karp had spent the morning roller skiing. He arrived the night before, and I assumed he was staying for the weekend. But he was going to Boston later that afternoon for a meeting and then heading to Europe. After lunch, we spent a couple of hours hiking. Two of Karp’s bodyguards trailed us by a few feet while two others waited in the parking lot. We talked at length about ICE. He noted that other tech companies had contracts with ICE, yet activists seemed to be directing most of their ire at Palantir, which he took as a backhanded compliment. “People understand we have these powerful platforms and that the platforms actually work,” he said, adding that maybe the protesters were ignoring the other companies because their technology was “not as effectual.”
Karp made clear that he was opposed to Trump’s immigration policies: “There are lots of reasons I don’t support the president; this is actually also one of them.” He told me that he was “personally very OK with changing the demographics of our country” but that a secure border was something that progressives should embrace. “I’ve been a progressive my whole life,” he said. “My family’s progressive, and we were never in favor of open borders.” He said borders “ensure that wages increase. It’s a progressive position.” When the left refuses to seriously address border security and immigration, he said, the right inevitably wins. To the extent that Palantir was helping to preserve public order, it was “empirically keeping the West more center-left.”
But he claimed that if ICE had sought Palantir’s services after Trump took office, he probably would have balked. “I’m not sure I would feel strongly about doing it,” he said. “We probably wouldn’t do the contract. But that’s different than pulling the plug.” Karp said that Palantir couldn’t break with ICE because doing so would mark it as an unreliable partner in the eyes of the military. If Palantir walked away from ICE, he said, it would send a horrible message to soldiers who depend on Palantir’s software. “Why would a war fighter believe you aren’t going to do the same thing to them when they’re in the middle of a battle?” he asked.
He told me that Palantir has rejected some potential clients because it was worried about how they might use its software. It had spurned a lucrative offer from the Saudi government because of Riyadh’s human rights record, he said, and had likewise turned down a major tobacco company. Karp said that he found it hard personally to see Palantir accused of facilitating racism. But he told me that he had been reluctant to talk about his mother because “I don’t want to instrumentalize her” and also because “I don’t think the emotional argument is as persuasive as people think.”
Instead, Karp was trying to initiate a broader debate about Silicon Valley and U.S. national security. He had a convenient cudgel at his disposal: In 2018, Google withdrew from Project Maven, the Pentagon’s artificial-intelligence program, after facing resistance from some employees, who didn’t think the company should be involved in the development of potentially lethal weapons. Karp had elsewhere criticized Google’s decision as “borderline craven” and had sarcastically called the Google employees “super-woke engineers.” In his view, Project Maven was nothing less than the Manhattan Project of the 21st century, and, as with the atomic bomb, the country that gained a military edge with artificial intelligence would “determine the world order tomorrow.” What he didn’t say publicly was that Palantir had replaced Google on parts of the project. (Karp couldn’t confirm that, but I confirmed it, and it has been reported elsewhere.)
Karp insisted that Palantir was more in step with public opinion in the United States than Google and other Silicon Valley giants were. “We’re making Western institutions strong and, in some cases, dominant,” he said. “That’s our narrative. Now, that’s probably not a popular narrative in the Valley. It’s a very popular narrative in the rest of America. What’s Google’s narrative? ‘We destroy the media, we divide the country, we take away your job, we get rich, and by the way, when the country needs you, we’re nowhere to be found.’” He added that if the “Google standard takes hold, the single biggest strategic asset America has, which is our ability to produce software platforms, will be taken out of the hands of our war fighters. And that de facto means our adversaries are in a much stronger position.”
But if Karp’s broadsides against Google were meant to ease public pressure on Palantir, it didn’t seem to work. When it was announced in April that Palantir had been awarded the H.H.S. contracts, a backlash ensued. Progressive groups, human rights organizations and members of Congress criticized the deals. The main concern was that the Trump administration might use information collected by H.H.S. to target immigrants. In a six-page letter sent in July to the H.H.S. secretary, Alex Azar, Senator Elizabeth Warren and 15 other congressional Democrats cited the immigration issue and said that their reservations about the deal were “compounded by the fact that Palantir has a history of contracting with ICE.” (An H.H.S. spokesperson says that the data it collects as part of its Covid response does not include personally identifiable information and is not being shared with ICE.) Last month, Representatives Alexandria Ocasio-Cortez and Jesús García, pointing to Palantir’s contracts with H.H.S. and other aspects of its business, asked the S.E.C. to investigate the company before allowing it to go public. Their request evidently had no effect, but it was an indication of how Palantir has come to be viewed in progressive circles.
Palantir is not without Democratic allies. James Carville is an informal adviser to the company, and Palantir’s technology was used extensively by the Obama administration. When Senator Kamala Harris, the Democratic vice-presidential nominee, was California’s attorney general, her office turned to Palantir for help creating a statewide law-enforcement database. But living down the controversy over ICE may not be easy. Perhaps an interesting analogue, raised in a column last year by the Times writer Kevin Roose, is Dow Chemical, which produced the napalm that the U.S. military used in Vietnam — a fact that would gut its reputation for decades to come. Even if Palantir’s business ultimately doesn’t suffer, its image has unquestionably been harmed.
In June, Palantir filed to go public, and its stock debuted on Sept. 30. The company eschewed an initial public offering in favor of a direct listing, in which no new shares were created or issued. In the prospectus that it submitted to the Securities and Exchange Commission, Palantir announced that it had moved its headquarters from Palo Alto to Denver, formalizing its break from Silicon Valley. Karp used his introductory letter to drive home the point. He slammed what he called “the engineering elite of Silicon Valley,” said that Palantir had found itself increasingly alienated from the values of the tech industry and reaffirmed the company’s commitment to working with the U.S. military and to defending the West. “We have chosen sides,” Karp wrote, a comment that seemed to imply that Silicon Valley had chosen the opposite side.
The decision to go public represented an about-face for a company that had resisted doing so even as it was being hyped as a next-generation Silicon Valley unicorn. Just before I saw Karp in Paris, he had announced to employees that the company would be remaining private for awhile longer. Karp told me that Palantir had never had trouble raising money and that he worried about the effect a public listing might have on its culture. Thiel just didn’t think that the time was right. He said that “it still feels to me like we’re nowhere near the point where this is the kind of ubiquitous platform” that would, in his view, have justified taking Palantir public.
A few days after Palantir’s stock debuted, I spoke to Karp via video link. He was in Switzerland. He had spent the first few months of the pandemic at a house he owns in New Hampshire, not far from his place in Vermont, before leaving for Europe in July. He was in good spirits, as you would expect of someone who had officially just become a billionaire (he owns at least 6 percent of Palantir). He said that, as an introvert, the lockdown had been no great burden for him. He missed, however, seeing his parents (both reside in the Philadelphia area) and his colleagues.
Some observers had suggested that Palantir’s decision to go public had been driven in part by the prospect of a Trump loss; it was cashing in while its government business was still flourishing. But Karp insisted the election had nothing to do with it — federal contracts, he said, were largely apolitical, and a change in the White House was unlikely to affect Palantir. He also noted that he was supporting Biden and was about to make a donation to his campaign. He told me that Palantir had gone public because its business had matured to the point that it now made sense. Despite the pandemic, he said, the company’s revenue had been up 49 percent during the first six months of the year. More important, he added, Palantir had tweaked its Foundry software so that it could now be installed and updated remotely, which would make it easier to win new business. “Out of nowhere,” he said, “the company was in a technical and financial position” to go public.
Investors weren’t so sure. In its prospectus, Palantir reported that it was still losing hundreds of millions of dollars: $580 million in 2019, following a similar loss the year before. It also disclosed that just three customers accounted for roughly 30 percent of its revenue. (Palantir’s governance structure was another concern: Karp, Thiel and Stephen Cohen will retain just under 50 percent of the voting power, as long as their holdings of securities meet a certain minimum.) For years, Palantir had often been portrayed as a colossus. But its financials appeared to tell a different story, and some critics went so far as to suggest that Palantir was barely a viable business. The day before the company’s stock started trading, CNBC interviewed Scott Galloway, a professor at New York University’s Stern School of Business, who was caustic. Palantir, he said, was “crap being flung at tourists to the unicorn zoo.”
To Galloway, Palantir is just more Silicon Valley smoke and mirrors (even if it is no longer based in the valley). To Karp, Palantir is nothing less than a bulwark of liberal democracy — and maybe all that stands between him and the realization of his worst fear, a world succumbing to fascism. To Ben Wizner, the director of the American Civil Liberties Union’s Speech, Privacy and Technology project, Palantir’s business model is predicated on an assumption that its clients should have “legitimate access to every detail of our lives,” and the company’s software is a mechanism by which the government can keep an ever closer watch on us. To Airbus, Palantir is a tool that enhances efficiency and profitability. To Mijente, Palantir is an accessory to human rights violations. To the United Nations World Food Program, which earlier this month was awarded the Nobel Peace Prize for its work on Covid-19 relief, Palantir’s technology has played a key role in its effort to get food and supplies distributed amid the pandemic.
What Palantir does is complicated and mysterious. As with the magical stones for which it is named, people seem to see in it what they want to see. I thought Karp put it pretty nicely. “Palantir,” he said, “is the convergence of software and difficult positions.”
Michael Steinberger is a regular contributor to the magazine. His last feature was about the resiliency of the stock market despite the global pandemic.
Type animation by Nikita Iziev.
The All-Seeing Eye (of Sauron): Data integration software firm Palantir, says CEO Alex Karp, is the convergence of software and difficult positions.
On a bright Tuesday afternoon in Paris last fall, Alex Karp was doing tai chi in the Luxembourg Gardens. He wore blue Nike sweatpants, a blue polo shirt, orange socks, charcoal-gray sneakers and white-framed sunglasses with red accents that inevitably drew attention to his most distinctive feature, a tangle of salt-and-pepper hair rising skyward from his head.
Under a canopy of chestnut trees, Karp executed a series of elegant tai chi and qigong moves, shifting the pebbles and dirt gently under his feet as he twisted and turned. A group of teenagers watched in amusement. After 10 minutes or so, Karp walked to a nearby bench, where one of his bodyguards had placed a cooler and what looked like an instrument case. The cooler held several bottles of the nonalcoholic German beer that Karp drinks (he would crack one open on the way out of the park). The case contained a wooden sword, which he needed for the next part of his routine. “I brought a real sword the last time I was here, but the police stopped me,” he said matter of factly as he began slashing the air with the sword.
Those gendarmes evidently didn’t know that Karp, far from being a public menace, was the chief executive of an American company whose software has been deployed on behalf of public safety in France. The company, Palantir Technologies, is named after the seeing stones in J.R.R. Tolkien’s “The Lord of the Rings.” Its two primary software programs, Gotham and Foundry, gather and process vast quantities of data in order to identify connections, patterns and trends that might elude human analysts. The stated goal of all this “data integration” is to help organizations make better decisions, and many of Palantir’s customers consider its technology to be transformative. Karp claims a loftier ambition, however. “We built our company to support the West,” he says. To that end, Palantir says it does not do business in countries that it considers adversarial to the U.S. and its allies, namely China and Russia. In the company’s early days, Palantir employees, invoking Tolkien, described their mission as “saving the shire.”
Comments to Does Palantir See Too Much? – The New York Times
Frptwenty
2 yr. ago
At least the Palantir I have at home always keeps reminding me that: I see you…. The Age of Men is ending, the Age of the Orc has come.
Dont know if its broken or something.
Million2026
This was a great article and well worth a read. On balance, I’m a supporter of Palantir (though not yet impressed enough with it as a business to invest). I think using our technological ends to identify people and situations that are dangerous to the public results in us having MORE freedom, not less. Palantir is an unobtrusive means of keeping us safe.
XV. How Peter Thiel’s Palantir Helped the NSA Spy on the Whole World
Documents provided by NSA whistleblower Edward Snowden reveal Palantir’s role in creating the U.S. government’s international spy machine.
Sam Biddle
February 22 2017, 4:06 a.m.
Donald Trump has inherited the most powerful machine for spying ever devised. How this petty, vengeful man might wield and expand the sprawling American spy apparatus, already vulnerable to abuse, is disturbing enough on its own. But the outlook is even worse considering Trump’s vast preference for private sector expertise and new strategic friendship with Silicon Valley billionaire investor Peter Thiel, whose controversial (and opaque) company Palantir has long sought to sell governments an unmatched power to sift and exploit information of any kind. Thiel represents a perfect nexus of government clout with the kind of corporate swagger Trump loves. The Intercept can now reveal that Palantir has worked for years to boost the global dragnet of the NSA and its international partners, and was in fact co-created with American spies.
Peter Thiel became one of the American political mainstream’s most notorious figures in 2016 (when it emerged he was bankrolling a lawsuit against Gawker Media, my former employer) even before he won a direct line to the White House. Now he brings to his role as presidential adviser decades of experience as kingly investor and token nonliberal on Facebook’s board of directors, a Rolodex of software luminaries, and a decidedly Trumpian devotion to controversy and contrarianism. But perhaps the most appealing asset Thiel can offer our bewildered new president will be Palantir Technologies, which Thiel founded with Alex Karp and Joe Lonsdale in 2004.
Palantir has never masked its ambitions, in particular the desire to sell its services to the U.S. government — the CIA itself was an early investor in the startup through In-Q-Tel, the agency’s venture capital branch. But Palantir refuses to discuss or even name its government clientele, despite landing “at least $1.2 billion” in federal contracts since 2009, according to an August 2016 report in Politico. The company was last valued at $20 billion and is expected to pursue an IPO in the near future. In a 2012 interview with TechCrunch, while boasting of ties to the intelligence community, Karp said nondisclosure contracts prevent him from speaking about Palantir’s government work.
Alexander “Alex” Karp, co-founder and chief executive officer of Palantir Technologies Inc., speaks during the WSJDLive Global Technology Conference in Laguna Beach, California, U.S., on Wednesday, Oct. 26, 2016. The conference brings together an unmatched group of top CEOs, founders, pioneers, investors and luminaries to explore tech opportunities emerging around the world. Photographer: Patrick T. Fallon/Bloomberg via Getty Images
Alex Karp, co-founder and CEO of Palantir Technologies, speaks during the WSJDLive Global Technology Conference in Laguna Beach, Calif., on Oct. 26, 2016.
Photo: Patrick T. Fallon/Bloomberg/Getty Images
“Palantir” is generally used interchangeably to refer to both Thiel and Karp’s company and the software that company creates. Its two main products are Palantir Gotham and Palantir Metropolis, more geeky winks from a company whose Tolkien namesake is a type of magical sphere used by the evil lord Sauron to surveil, trick, and threaten his enemies across Middle Earth. While Palantir Metropolis is pegged to quantitative analysis for Wall Street banks and hedge funds, Gotham (formerly Palantir Government) is designed for the needs of intelligence, law enforcement, and homeland security customers. Gotham works by importing large reams of “structured” data (like spreadsheets) and “unstructured” data (like images) into one centralized database, where all of the information can be visualized and analyzed in one workspace. For example, a 2010 demo showed how Palantir Government could be used to chart the flow of weapons throughout the Middle East by importing disparate data sources like equipment lot numbers, manufacturer data, and the locations of Hezbollah training camps. Palantir’s chief appeal is that it’s not designed to do any single thing in particular, but is flexible and powerful enough to accommodate the requirements of any organization that needs to process large amounts of both personal and abstract data.
A Palantir promotional video.
Despite all the grandstanding about lucrative, shadowy government contracts, co-founder Karp does not shy away from taking a stand in the debate over government surveillance. In a Forbes profile in 2013, he played privacy lamb, saying, “I didn’t sign up for the government to know when I smoke a joint or have an affair. … We have to find places that we protect away from government so that we can all be the unique and interesting and, in my case, somewhat deviant people we’d like to be.” In that same article, Thiel lays out Palantir’s mission with privacy in mind: to “reduce terrorism while preserving civil liberties.” After the first wave of revelations spurred by the whistleblower Edward Snowden, Palantir was quick to deny that it had any connection to the NSA spy program known as PRISM, which shared an unfortunate code name with one of its own software products. The current iteration of Palantir’s website includes an entire section dedicated to “Privacy & Civil Liberties,” proclaiming the company’s support of both:
Palantir Technologies is a mission-driven company, and a core component of that mission is protecting our fundamental rights to privacy and civil liberties. …
Some argue that society must “balance” freedom and safety, and that in order to better protect ourselves from those who would do us harm, we have to give up some of our liberties. We believe that this is a false choice in many areas. Particularly in the world of data analysis, liberty does not have to be sacrificed to enhance security. Palantir is constantly looking for ways to protect privacy and individual liberty through its technology while enabling the powerful analysis necessary to generate the actionable intelligence that our law enforcement and intelligence agencies need to fulfill their missions.
It’s hard to square this purported commitment to privacy with proof, garnered from documents provided by Edward Snowden, that Palantir has helped expand and accelerate the NSA’s global spy network, which is jointly administered with allied foreign agencies around the world. Notably, the partnership has included building software specifically to facilitate, augment, and accelerate the use of XKEYSCORE, one of the most expansive and potentially intrusive tools in the NSA’s arsenal. According to Snowden documents published by The Guardian in 2013, XKEYSCORE is by the NSA’s own admission its “widest reaching” program, capturing “nearly everything a typical user does on the internet.” A subsequent report by The Intercept showed that XKEYSCORE’s “collected communications not only include emails, chats, and web-browsing traffic, but also pictures, documents, voice calls, webcam photos, web searches, advertising analytics traffic, social media traffic, botnet traffic, logged keystrokes, computer network exploitation targeting, intercepted username and password pairs, file uploads to online services, Skype sessions, and more.” For the NSA and its global partners, XKEYSCORE makes all of this as searchable as a hotel reservation site.
But how do you make so much data comprehensible for human spies? As the additional documents published with this article demonstrate, Palantir sold its services to make one of the most powerful surveillance systems ever devised even more powerful, bringing clarity and slick visuals to an ocean of surveillance data.
An office building occupied by the technology firm Palantir in McLean, Virginia on October 11, 2014. Photo Credit: Kristoffer Tripplaar/ Sipa USA
An office building occupied by the technology firm Palantir in McLean, Va., on Oct. 11, 2014.
Photo: Kristoffer Tripplaar/Sipa USA/AP
Palantir’s relationship with government spy agencies appears to date back to at least 2008, when representatives from the U.K.’s signals intelligence agency, Government Communications Headquarters, joined their American peers at VisWeek, an annual data visualization and computing conference organized by the Institute of Electrical and Electronics Engineers and the U.S. National Institute of Standards and Technology. Attendees from throughout government and academia gather to network with members of the private sector at the event, where they compete in teams to solve hypothetical data-based puzzles as part of the Visual Analytics Science and Technology (VAST) Challenge. As described in a document saved by GCHQ, Palantir fielded a team in 2008 and tackled one such scenario using its own software. It was a powerful marketing opportunity at a conference filled with potential buyers.
In the demo, Palantir engineers showed how their software could be used to identify Wikipedia users who belonged to a fictional radical religious sect and graph their social relationships. In Palantir’s pitch, its approach to the VAST Challenge involved using software to enable “many analysts working together [to] truly leverage their collective mind.” The fake scenario’s target, a cartoonishly sinister religious sect called “the Paraiso Movement,” was suspected of a terrorist bombing, but the unmentioned and obvious subtext of the experiment was the fact that such techniques could be applied to de-anonymize and track members of any political or ideological group. Among a litany of other conclusions, Palantir determined the group was prone to violence because its “Manifesto’s intellectual influences include ‘Pancho Villa, Che Guevara, Leon Trotsky, [and] Cuban revolutionary Jose Martí,’ a list of military commanders and revolutionaries with a history of violent actions.”
The delegation from GCHQ returned from VisWeek excited and impressed. In a classified report from those who attended, Palantir’s potential for aiding the spy agency was described in breathless terms. “Palantir are a relatively new Silicon Valley startup who are sponsored by the CIA,” the report began. “They claim to have significant involvement with the US intelligence community, although none yet at NSA.” GCHQ noted that Palantir “has been developed closely internally with intelligence community users (unspecified, but likely to be the CIA given the funding).” The report described Palantir’s demo as “so significant” that it warranted its own entry in GCHQ’s classified internal wiki, calling the software “extremely sophisticated and mature. … We were very impressed. You need to see it to believe it.”
The report conceded, however, that “it would take an enormous effort for an in-house developed GCHQ system to get to the same level of sophistication” as Palantir. The GCHQ briefers also expressed hesitation over the price tag, noting that “adoption would have [a] huge monetary … cost,” and over the implications of essentially outsourcing intelligence analysis software to the private sector, thus making the agency “utterly dependent on a commercial product.” Finally, the report added that “it is possible there may be concerns over security — the company have published a lot of information on their website about how their product is used in intelligence analysis, some of which we feel very uncomfortable about.”
A page from Palantir’s “Executive Summary” document, provided to government clients.
However anxious British intelligence was about Palantir’s self-promotion, the worry must not have lasted very long. Within two years, documents show that at least three members of the “Five Eyes” spy alliance between the United States, the U.K., Australia, New Zealand, and Canada were employing Palantir to help gather and process data from around the world. Palantir excels at making connections between enormous, separate databases, pulling big buckets of information (call records, IP addresses, financial transactions, names, conversations, travel records) into one centralized heap and visualizing them coherently, thus solving one of the persistent problems of modern intelligence gathering: data overload.
A GCHQ wiki page titled “Visualisation,” outlining different ways “to provide insight into some set of data,” puts succinctly Palantir’s intelligence value:
Palantir is an information management platform for analysis developed by Palantir Technologies. It integrates structured and unstructured data, provides search and discovery capabilities, knowledge management, and collaborative features. The goal is to offer the infrastructure, or ‘full stack,’ that intelligence organizations require for analysis.
Bullet-pointed features of note included a “Graph View,” “Timelining capabilities,” and “Geo View.”
A GCHQ diagram indicates how Palantir could be used as part of a computer network attack.
Under the Five Eyes arrangement, member countries collect and pool enormous streams of data and metadata collected through tools like XKEYSCORE, amounting to tens of billions of records. The alliance is constantly devising (or attempting) new, experimental methods of prying data out of closed and private sources, including by hacking into computers and networks in non-Five Eyes countries and infecting them with malware.
A 2011 PowerPoint presentation from GCHQ’s Network Defence Intelligence & Security Team (NDIST) — which, as The Intercept has previously reported, “worked to subvert anti-virus and other security software in order to track users and infiltrate networks” — mentioned Palantir as a tool for processing data gathered in the course of its malware-oriented work. Palantir’s software was described as an “analyst workspace [for] pulling together disparate information and displaying it in novel ways,” and was used closely in conjunction with other intelligence software tools, like the NSA’s notorious XKEYSCORE search system. The novel ways of using Palantir for spying seemed open-ended, even imaginative: A 2010 presentation on the joint NSA-GCHQ “Mastering the Internet” surveillance program mentioned the prospect of running Palantir software on “Android handsets” as part of a SIGINT-based “augmented reality” experience. It’s unclear what exactly this means or could even look like.
Above all, these documents depict Palantir’s software as a sort of consolidating agent, allowing Five Eyes analysts to make sense of tremendous amounts of data that might have been otherwise unintelligible or highly time-consuming to digest. In a 2011 presentation to the NSA, classified top secret, an NDIST operative noted the “good collection” of personal data among the Five Eyes alliance but lamented the “poor analytics,” and described the attempt to find new tools for SIGINT analysis, in which it “conducted a review of 14 different systems that might work.” The review considered services from Lockheed Martin and Detica (a subsidiary of BAE Systems) but decided on the up-and-comer from Palo Alto.
Palantir is described as having been funded not only by In-Q-Tel, the CIA’s venture capital branch, but furthermore created “through [an] iterative collaboration between Palantir computer scientists and analysts from various intelligence agencies over the course of nearly three years.” While it’s long been known that Palantir got on its feet with the intelligence community’s money, it has not been previously reported that the intelligence community actually helped build the software. The continuous praise seen in these documents shows that the collaboration paid off. Under the new “Palantir Model,” “data can come from anywhere” and can be “asked whatever the analyst wants.”
Along with Palantir’s ability to pull in “direct XKS Results,” the presentation boasted that the software was already connected to 10 other secret Five Eyes and GCHQ programs and was highly popular among analysts. It even offered testimonials (TWO FACE appears to be a code name for the implementation of Palantir):
[Palantir] is the best tool I have ever worked with. It’s intuitive, i.e. idiot-proof, and can do a lot you never even dreamt of doing.
This morning, using TWO FACE rather than XKS to review the activity of the last 3 days. It reduced the initial analysis time by at least 50%.
Enthusiasm runs throughout the PowerPoint: A slide titled “Unexpected Benefits” reads like a marketing brochure, exclaiming that Palantir “interacts with anything!” including Google Earth, and “You can even use it on a iphone or laptop.” The next slide, on “Potential Downsides,” is really more praise in disguise: Palantir “Looks expensive” but “isn’t as expensive as expected.” The answer to “What can’t it do?” is revealing: “However we ask, Palantir answer,” indicating that the collaboration between spies and startup didn’t end with Palantir’s CIA-funded origins, but that the company was willing to create new features for the intelligence community by request.
On GCHQ’s internal wiki page for TWO FACE, analysts were offered a “how to” guide for incorporating Palantir into their daily routine, covering introductory topics like “How do I … Get Data from XKS in Palantir,” “How do I … Run a bulk search,” and “How do I … Run bulk operations over my objects in Palantir.” For anyone in need of a hand, “training is currently offered as 1-2-1 desk based training with a Palantir trainer. This gives you the opportunity to quickly apply Palantir to your current work task.” Palantir often sends “forward deployed engineers,” or FDEs, to work alongside clients at their offices and provide assistance and engineering services, though the typical client does not have access to the world’s largest troves of personal information. For analysts interested in tinkering with Palantir, there was even a dedicated instant message chat room open to anyone for “informally” discussing the software.
The GCHQ wiki includes links to classified webpages describing Palantir’s use by the Australian Defence Signals Directorate (now called the Australian Signals Directorate) and to a Palantir entry on the NSA’s internal “Intellipedia,” though The Intercept does not have access to copies of the linked sites. However, embedded within Intellipedia HTML files available to The Intercept are references to a variety of NSA-Palantir programs, including “Palantir Classification Helper,” “[Target Knowledge Base] to Palantir PXML,” and “PalantirAuthService.” (Internal Palantir documents obtained by TechCrunch in 2013 provide additional confirmation of the NSA’s relationship with the company.)
One Palantir program used by GCHQ, a software plug-in named “Kite,” was preserved almost in its entirety among documents provided to The Intercept. An analysis of Kite’s source code shows just how much flexibility the company afforded Five Eyes spies. Developers and analysts could ingest data locally using either Palantir’s “Workspace” application or Kite. When they were satisfied the process was working properly, they could push it into a Palantir data repository where other Workspace users could also access it, almost akin to a Google Spreadsheets collaboration. When analysts were at their Palantir workstation, they could perform simple imports of static data, but when they wanted to perform more complicated tasks like import databases or set up recurring automatic imports, they turned to Kite.
Kite worked by importing intelligence data and converting it into an XML file that could be loaded into a Palantir data repository. Out of the box, Kite was able to handle a variety of types of data (including dates, images, geolocations, etc.), but GCHQ was free to extend it by writing custom fields for complicated types of data the agency might need to analyze. The import tools were designed to handle a variety of use cases, including static data sets, databases that were updated frequently, and data stores controlled by third parties to which GCHQ was able to gain access.
This collaborative environment also produced a piece of software called “XKEYSCORE Helper,” a tool programmed with Palantir (and thoroughly stamped with its logo) that allowed analysts to essentially import data from the NSA’s pipeline, investigate and visualize it through Palantir, and then presumably pass it to fellow analysts or Five Eyes intelligence partners. One of XKEYSCORE’s only apparent failings is that it’s so incredibly powerful, so effective at vacuuming personal metadata from the entire internet, that the volume of information it extracts can be overwhelming. Imagine trying to search your Gmail account, only the results are pulled from every Gmail inbox in the world.
Making XKEYSCORE more intelligible — and thus much more effective — appears to have been one of Palantir’s chief successes. The helper tool, documented in a GCHQ PDF guide, provided a means of transferring data captured by the NSA’s XKEYSCORE directly into Palantir, where presumably it would be far easier to analyze for, say, specific people and places. An analyst using XKEYSCORE could pull every IP address in Moscow and Tehran that visited a given website or made a Skype call at 14:15 Eastern Time, for example, and then import the resulting data set into Palantir in order to identify additional connections between the addresses or plot their positions using Google Earth.
Palantir was also used as part of a GCHQ project code-named LOVELY HORSE, which sought to improve the agency’s ability to collect so-called open source intelligence — data available on the public internet, like tweets, blog posts, and news articles. Given the “unstructured” nature of this kind of data, Palantir was cited as “an enrichment to existing [LOVELY HORSE] investigations … the content should then be viewable in a human readable format within Palantir.”
Palantir’s impressive data-mining abilities are well-documented, but so too is the potential for misuse. Palantir software is designed to make it easy to sift through piles of information that would be completely inscrutable to a human alone, but the human driving the computer is still responsible for making judgments, good or bad.
A 2011 document by GCHQ’s SIGINT Development Steering Group, a staff committee dedicated to implementing new spy methods, listed some of these worries. In a table listing “risks & challenges,” the SDSG expressed a “concern that [Palantir] gives the analyst greater potential for going down too many analytical paths which could distract from the intelligence requirement.” What it could mean for analysts to distract themselves by going down extraneous “paths” while browsing the world’s most advanced spy machine is left unsaid. But Palantir’s data-mining abilities were such that the SDSG wondered if its spies should be blocked from having full access right off the bat and suggested configuring Palantir software so that parts would “unlock … based on analysts skill level, hiding buttons and features until needed and capable of utilising.” If Palantir succeeded in fixing the intelligence problem of being overwhelmed with data, it may have created a problem of over-analysis — the company’s software offers such a multitude of ways to visualize and explore massive data sets that analysts could get lost in the funhouse of infographics, rather than simply being overwhelmed by the scale of their task.
If Palantir’s potential for misuse occurred to the company’s spy clients, surely it must have occurred to Palantir itself, especially given the company’s aforementioned “commitment” to privacy and civil liberties. Sure enough, in 2012 the company announced the formation of the Palantir Council of Advisors on Privacy and Civil Liberties, a committee of academics and consultants with expertise in those fields. Palantir claimed that convening the PCAP had “provided us with invaluable guidance as we try to responsibly navigate the often ill-defined legal, political, technological, and ethical frameworks that sometimes govern the various activities of our customers,” and continued to discuss the privacy and civil liberties “implications of product developments and to suggest potential ways to mitigate any negative effects.” Still, Palantir made clear that the “PCAP is advisory only — any decisions that we make after consulting with the PCAP are entirely our own.”
What would a privacy-minded conversation about privacy-breaching software look like? How had a privacy and civil liberties council navigated the fact that Palantir’s clientele had directly engaged in one of the greatest privacy and civil liberties breaches of all time? It’s hard to find an answer.
Palantir wrote that it structured the nondisclosure agreement signed by PCAP members so that they “will be free to discuss anything that they learn in working with us unless we clearly designate information as proprietary or otherwise confidential (something that we have rarely found necessary except on very limited occasions).” But despite this assurance of transparency, all but one of the PCAP’s former and current members either did not return a request for comment for this article or declined to comment citing the NDA.
The former PCAP member who did respond, Stanford privacy scholar Omer Tene, told The Intercept that he was unaware of “any specific relationship, agreement, or project that you’re referring to,” and said he was not permitted to answer whether Palantir’s work with the intelligence community was ever a source of tension with the PCAP. He declined to comment on either the NSA or GCHQ specifically. “In general,” Tene said, “the role of the PCAP was to hear about client engagement or new products and offerings that the company was about to launch, and to opine as to the way they should be set up or delivered in order to minimize privacy and civil liberties concerns.” But without any further detail, it’s unclear whether the PCAP was ever briefed on the company’s work for spy agencies, or whether such work was a matter of debate.
There’s little detail to be found on archived versions of Palantir’s privacy and civil liberties-focused blog, which appears to have been deleted sometime after the PCAP was formed. Palantir spokesperson Matt Long told The Intercept to contact the Palantir media team for questions regarding the vanished blog at the same email address used to reach Long in the first place. Palantir did not respond to additional repeated requests for comment and clarification.
A GCHQ spokesperson provided a boilerplate statement reiterating the agency’s “longstanding policy” against commenting on intelligence matters and asserted that all its activities are “carried out in accordance with a strict legal and policy framework.” The NSA did not provide a response.
Anyone worried that the most powerful spy agencies on Earth might use Palantir software to violate the privacy or civil rights of the vast number of people under constant surveillance may derive some cold comfort in a portion of the user agreement language Palantir provided for the Kite plug-in, which stipulates that the user will not violate “any applicable law” or the privacy or the rights “of any third party.” The world will just have to hope Palantir’s most powerful customers follow the rules.
Documents published with this article:
GCHQ VisWeek 2008 Conference Report
Palantir Executive Summary
NDIST Cyber Defence
Mastering the Internet
The Tale of Two Sources
TWO FACE on GCHQ Wiki
XKEYSCORE Helper Notes
SDSG Integrated Analytics Workshop
Listen to Jeremy Scahill’s interview with Sam Biddle on Episode 4 of Intercepted (begins at 32:05).
CIA Superspy, James Jesus Angleton, summed up his career in a mid 1980’s interview with author, Joseph Trento:
“You know how I got to be in charge of counterintelligence? I agreed not to polygraph or require detailed background checks on (Wall Street lawyer and spy) Allen Dulles and 60 of his closest friends. The real problem, Angleton concluded, was that “there was no accountability. And without real accountability everything turned to xxxx.
You know, the CIA got tens of thousands of brave people killed… (ETK: Actually, the figure is estimated in the range of 6 to 30 million). We played with lives as if we owned them. We gave false hope. We – I – so misjudged what happened.
Fundamentally, the founding fathers of U.S. intelligence were liars. The better you lied and the more you betrayed, the more likely you would be promoted. These people attracted and promoted each other. Outside of their duplicity, the only thing they had in common was a desire for absolute power.
Allen Dulles, Richard Helms, Carmel Offie, and Frank Wisner were the grand masters. If you were in a room with them you were in a room full of people that you had to believe would deservedly end up in hell. I guess I will see them there soon.”
From Joseph Trento’s “The Secret History of the CIA,” (2001) pp. 478-479
