Episode 6: Opening the Five Eyes: Deciphering UK’s JTRIG (Joint Threat Research Intelligence Group); Suzie Dawson Video (10/27/19); Transcription & Graphics
Epigraph Quotes from the Video:
Lissa K. Johnson, clinical psychologist: It is quite disturbing as a psychologist to discover that our psychological knowledge is being used to covertly deceive people, discredit people, abuse people, and covertly destroy people’s lives. They talk about false flags, spoofed blog sites, fake victim posts, forming online aliases to befriend people and deceive them. As far as their goals go; they talk about making something happen in the online world and the real world. From the point of ethics of the psychology profession, the abusiveness of the tactics are extremely disturbing. These practices are also deeply anti-democratic. People are being manipulated using the principles of social influence, social psychology, and persuasion.
For me, coming to this afresh, it’s quite shocking and unbelievable as well. I found myself thinking: “really, against activists?” People with absolutely no criminal records, no charges against them, nothing to do with terrorism or national security? GCHQ (Government Communication Headquarters, Britain’s NSA) talks about targeting “political radicals.” Historically, since 9/11, the term “domestic terrorist” has been applied to organizations and grass-roots activists, another term is “black identity extremist” that is used to go after people. When you look at what the terms “terrorist” and “national security” have come to mean, basically they are political opposition and non-violent activists.
For targets, it’s easy to become distrustful. So I’d encourage targets to: 1) become aware of these psychological tactics. And 2) be aware of your own psychological strengths and weaknesses that can be used against you in quite sophisticated techniques. They are mimicking real relationships. They are talk about exploiting people’s personalities. So be self-aware of how you behave under stress. These are very sophisticated techniques.
Suzie Dawson: While the targets are often dissidents, activists, or journalists, this really is affecting everybody. Because we know that everybody around a target is also targeted. And everybody around them in 2 concentric circles. It’s known as the “2 hops principle” at the NSA and 5 Eyes. And William Binney, the ex-NSA technical director has explained this and also James Clapper (ex Director of National Intelligence). So for every one person that is targeted, hundreds of people get drawn into that net just by association.
And you are absolutely correct that “terrorist” is an ever-expanding definition. In the “Terrorism Suppression and Control Orders” Bill recently introduced in New Zealand, it says that a “terrorist” doesn’t have to be a terrorist. A terrorist can be someone who supports or comforts a terrorist group or organization. AND that person doesn’t have to KNOW that they have given comfort or aid to a terrorist group or organization. AND the terrorist group or organization that they don’t know that they’ve given aid or comfort to doesn’t have to have actually committed a terrorist act or have actually done anything at all. So now, it’s now not just terrorists that are being targeted, it’s anybody vaguely associated with anything the that government doesn’t like or wants to brand as terrorism regardless of whether any actual terrorism has taken place. And the legislation specifically states that; that no terrorist act needs to have been committed and that the people who are being targeted don’t need to be aware that they are somehow associated with this.
We are seeing the secret courts, the secret legislation, the prosecution-only trials. The whole thing is just insane. And as far as I’m concerned what is driving that is the privatization of spying. It’s that they’ve introduced a profit model which means that you now have all these subcontractors and contractors. It’s not even the intelligence agencies themselves, as much it’s who they contract the work out to and who they contract the work out to. And when you expand the so-called intelligence community to encompass this behemouth strucuture of all of these private companies… Well, what do you need to make more profit? You need growth. And what does growth mean in the surveillance industry? It needs more targets. And if you need more and more targets, then what do you have to do get more targets. You have to expand the definitions of who you can target.
…Unfortunately, when you look at the real-world outcomes for targeted journalists and dissidents… For example, Jamal Kashoggi was a targeted journalist. He was targeted using private-sector NSO group spyware and was targeted through someone he knew. They came at him through a social connection. He was targeted and it cost him his life. He wasn’t in a war zone. He wasn’t a terrorist and he wasn’t an enemy combatant. He was just somebody who was politically opposed to a regime which had sufficient money and resources to be able to hire mercenary hacking companies to provide them with software to be able to target him in such a way. So this “capture and kill” operation premise from the war zone and NSA providing technical support to those operations does expand out to the targeting of people outside of war zones who are not terrorists but who can still wind up in jail or dead or having their lives destroyed in some manner or another.
Webmaster Introduction: “The Global Network” (aka “NSA Global Spy Network”) IS “the architecture of oppression” that rules and shapes the world. Drawing on her experience as a TI and a journalist-researcher, Suzie Dawson exposes this “architecture of oppression” in her 10-part series: “Opening the Five Eyes: Exposing the Spies.” The system is comprised of covert SIGINT (Signals Intelligence) and HUMINT (Human Intelligence) ops carried out by the NSA, CIA, DOD, FBI, DHS, and NATO, etc., in the US, the UK Ministry of Defense GCHQ, JTRIG, MI6, MI5, etc., in Britain, the IDF, Unit 8200, Mossad, Shin Bet, etc., in Israel, and their equivalents in over 100 other nations. Cooperating private security and intelligence contractors and their hired thugs (aka “surveillance role players,” “counterterrorism specialists”) execute street level operations and psychological attacks. The Global Network secretly surveilles, targets, and destroys honest, incorruptible activists, journalists, “dissidents,” scientists, truth-tellers, and innumerable others who have been secretly watchlisted and flagged as “potential terrorist threats” or considered “enemies of the state,” “enemy non-combatants,” “extremists,” “radicals,” or “persons of interest,” etc.
This horrific, reprehensible, and criminal “social engineering” system, aka “The National Security Racketeering Network,” is a “growth industry.” It is the largest black and black-market op AND “Crime Against Humanity” in human history. It radically ramped up after 9/11 and continues to expand across the globe today as a for-profit enterprise.
In episodes 6 through 9, Dawson and guests analyze documents from JTRIG (Joint Threat Response Intelligence Group), a part of GCHQ (Government Communications Headquarters; the British equivalent of the NSA) and expose the manuals, psychological tricks, methodologies, and protocols deployed in these nefarious operations. My opinion is that these psychological warfare techniques derive mainly from government-military-intelligence agencies’ weaponization of psychology and other sciences conducted by Britain’s Tavistock Institute (1921 onward) and the US governments’ Macy Conferences-CIA MKULTRA+ mind control programs (1947 onward).
The satanic nature of these programs cannot be dismissed. The Christian ethos of “love thy neighbor,” the very underpinning of Western Christian civilization, is hereby replaced by a comprehensive system of psychological abuse, trauma, and torture which, in effect, is the overt expression of “hate, degrade, deceive, and destroy thy neighbor.”
‘Cursed is anyone who attacks (kills, strikes, smites down, smites) a neighbor in secret.’ And all the people will reply, ‘Amen.’
Deuteronomy 27:24
I believe this curse now extends to the agencies, police units, businesses, nations, scientists, academics, populations, and individuals that participate in, financially support, and/or tacitly acquiesce to this (beyond) despicable torture-murder system. Apparently, hell is now expanding exponentially both in this world and the next.
Webmaster’s Transcription and Graphics From Video:
Suzie Dawson: My name is Suzie Dawson. I’m an activist, a journalist, and former President of New Zealand’s Internet Party. I’m also a “targeted individual.” In this series we look at the methodologies that the spy agencies use to target people all around the world. Tonight, we are going to talk about some really important documents leaked by Edward Snowden to the Intercept. This was a series of articles written by Glenn Greenwald in 2014 about the JTRIG (Joint Threat Response Intelligence Group) documents. This is also covered by NBC, CBS and some others. JTRIG is a unit of Britain’s GCHQ (Government Communication Headquarters), which is the UK’s version of the NSA. The JTRIG unit are basically cyber stalkers, or cyber warriors, as they would think of themselves, who use the online space to target people in war zones but also around the world, who the deep state or the intelligence agencies have beef with for whatever reason. This includes, with many verified cases, journalists, activists, and dissidents in the 5 Eyes nations of Australia, New Zealand, Canada, the United States, and the UK itself.
These documents are incredibly significant because they provide a road map, an architecture of oppression being meted out by these agencies. The documents themselves have been written from a psychological perspective; they are littered with psychology terms all the way through. And they explain and depict in a series of power point presentations precisely how they go about targeting people in online spaces to destroy their reputations.
The documents talk about the 5Ds; Deny, distract, degrade, destroy, and deter. And those are the goals of the spy agencies. They want to distract us and deny us refuge and the ability to communicate. They want to degrade our reputations and our lives. They want to deter us from our activism and from our research. And they use a variety of really insidious, immoral methods to do so.
The JTRIG documents are well known to most activists. But what is not known is the nitty-gritty of what these spies are doing to us. Obviously, my work has been pretty centered over the last few years around my experiences as a targeted individual, journalist and activist. And also, with other activists I’ve worked with. So I have a lot of practical experience from the perspective of a target. What I don’t have is the academic experience. I don’t have the expertise to decipher a lot of the terminology employed in the documents. So I wanted to fill that gap with bringing on a friend of mine tonight.
Lissa K. Johnson is a clinical psychologist. She can give us the theory behind how this program has been put together. And she can explain some of the terms to us.
Johnson: It is quite disturbing as a psychologist to discover that our psychological knowledge is being used to covertly deceive people, discredit people, abuse people, and covertly destroy people’s lives. They talk about false flags, spoofed blog sites, fake victim posts, forming online aliases to befriend people and deceive them. As far as their goals go; they talk about making something happen in the online world and the real world. From the point of ethics of the psychology profession, the abusiveness of the tactics are extremely disturbing. These practices are also deeply anti-democratic. People are being manipulated using the principles of social influence, social psychology, and persuasion.
For me, coming to this afresh, it’s quite shocking and unbelievable as well. I found myself thinking “really, against activists?” People with absolutely no criminal records, no charges against them, nothing to do with terrorism or national security? GCHQ talks about targeting “political radicals.” Historically, since 9/11, the term “domestic terrorist” has been applied to organizations and grass-roots activists, another term is “black identity extremist” that is used to go after people. When you look at what the terms “terrorist” and “national security” have come to mean, basically they are political opposition and non-violent activists.
For targets, it’s easy to become distrustful. So I’d encourage targets to: 1) become aware of these psychological tactics. And 2) be aware of your own psychological strengths and weaknesses that can be used against you in quite sophisticated techniques. They are mimicking real relationships. They are talk about exploiting people’s personalities. So be self-aware of how you behave under stress. These are very sophisticated techniques.
Dawson: While the targets are often dissidents, activists, or journalists, this really is affecting everybody. Because we know that everybody around a target is also targeted. And everybody around them; 2 concentric circles. It’s known as the “2 hops principle” at the NSA and 5 Eyes. And William Binney, the ex-NSA technical director has explained this and also James Clapper (ex NSA Chief). So for every one person that is targeted, hundreds of people get drawn into that net just by association.
And you are absolutely correct that “terrorist” is an ever-expanding definition. In the “Terrorism Suppression and Control Orders” Bill recently introduced in New Zealand, it says that a “terrorist” doesn’t have to be a terrorist. A terrorist can be someone who supports or comforts a terrorist group or organization. AND that person doesn’t have to KNOW that they have given comfort or aid to a terrorist group or organization. AND the terrorist group or organization that they don’t know that they’ve given aid or comfort to doesn’t have to have actually committed a terrorist act or have actually done anything at all. So now, it’s now not just terrorists that are being targeted, it’s anybody vaguely associated with anything the that government doesn’t like or wants to brand as terrorism regardless of whether any actual terrorism has taken place. And the legislation specifically states that; that no terrorist act needs to have been committed and that the people who are being targeted don’t need to be aware that they are somehow associated with this.
We are seeing the secret courts, the secret legislation, the prosecution-only trials. The whole thing is just insane. And as far as I’m concerned what is driving that is the privatization of spying. It’s that they’ve introduced a profit model which means that you now have all these subcontractors and contractors. It’s not even the intelligence agencies themselves, as much it’s who they contract the work out to and who they contract the work out to. And when you expand the so-called intelligence community to encompass this behemouth strucuture of all of these private companies… Well, what do you need to make more profit? You need growth. And what does growth mean in the surveillance industry? It needs more targets. And if you need more and more targets, then what do you have to do get more targets. You have to expand the definitions of who you can target.
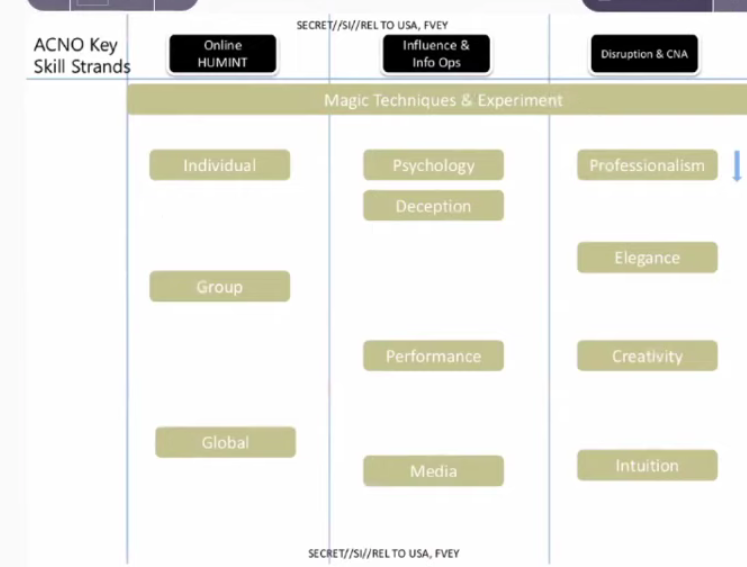
That leads me to the first slide of the JTRIG files.
This is the title slide, JTRIG. It says Online Human Intelligence. This tells me that HUMINT has traditionally been the practice of espionage between nations, in state-vs.-state, spying on diplomats, negotiations, etc. That the practice of human intelligence, that practice of actually dispatching teams of spies that has been going on for centuries… they’ve taken that discipline and decided that they don’t actually have to dispatch spies to other countries around the world to achieve their aims of targeting people. They can take this into the online and create teams of digital human intelligence spies. This ties into what we know colloquially as trolls.
I don’t think it’s accurate to call them trolls. The word, “trolls,” makes it sound like it’s some kid in his basement. What they really are is politically motivated and politically funded teams of operatives who are professionally trained. And they work according to these manuals. This JTRIG manual is a classic example of one of those training manuals for these teams of operatives. We see that trolls are actually a professional discipline. And they lead straight back to the government and the security agencies ultimately.
Even if the hundreds of other revelations from the Edward Snowden files, even if these had never come to public awareness, just this JTRIG manual alone that we are are studying here is such a significant contribution to the historical record. These documents alone prove his (Snowden’s) veracity.
From my perspective, having been subjected to techniques like this and then seeing these psychological techniques all neatly laid out in this training manuals in black and white…. This is the greatest gift that could ever have been given to me as an activist. So it’s our obligation to take the knowledge we have and spread this information to as wide an audience as possible. This is the only way we can hope to defend ourselves and our nations against this multi-billion dollar industry of interfering in our lives and manipulating us is to educate ourselves and others.
Back to the slide: They are also hoping to attain “Strategic Influence.” Strategic Influence tells me two things. To me, the fact that it’s strategic suggests this is a long-term view and undertaking. I know from studying other NSA files, that these guys do 20-year planning documents; they have long-term plans to manipulate society. What infrastructure do they want to have in place in 20 years? They are not just trying to influence targets, they are trying to influence populations and nations, so it’s actually the entire society they are trying to influence.
Here we see “Disruption and CNA (Computer Network Attacks). This to me is the method. So Online Human Intelligence is “who.” Strategic Influence is “what.” And Disruption and CNA is “how.” CNA is a computer network attack. This is about technical intrusion of devices. Where they are actually compromising hardware, manipulating your ability to communicate, and violating your privacy. Disruption is what they are wanting to do to groups or disrupting activities that they don’t like. And CNA is a primary method they use to achieve that.
Lissa: They also call strategic influence “information operations” (IO). It’s the manipulation of perception. Disruption is the technical skill of how to do it.
Dawson: next slide:
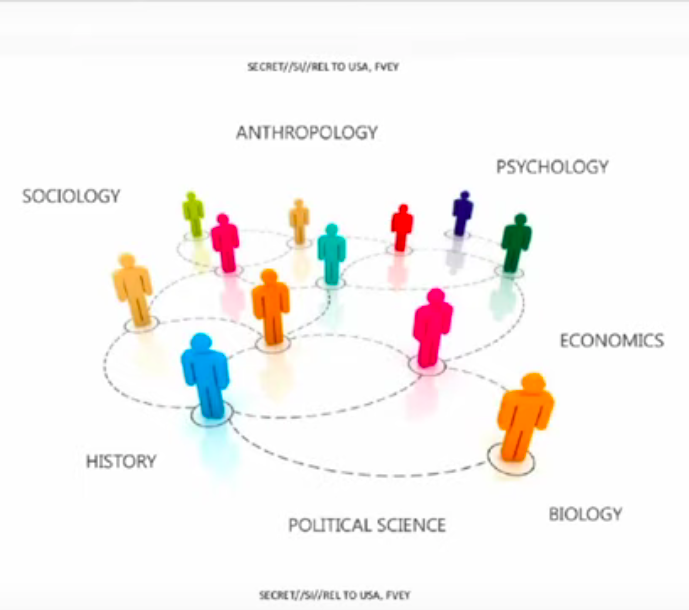
Johnson: These are the academic disciplines and principles they are bringing together to execute their strategy. We have anthropology, sociology, psychology, history, political science, economics, and biology. Economics looks at societies as a giant human experiment. They are all linked together in various ways.
Dawson: 1) These are the disciplines they are bringing together against targets. Psychological has to do with the profiling of the individuals involved. Economics, they absolutely go after the finances of targets and groups of targets, or organizations. They use economics to influence, undermine, suppress competition; they seek to control the flow of money. Biology to me says bio-metrics. Because we know they collect bio-metrics on targets and increasingly they collect bio-metrics on entire populations.
History- I know that one of the first things they do when they identify a target is they go back as far as back as they can and build a historical profile of an individual. They seek to know the history and control the present and future of every human on earth.
This slide is a lead in to the rest of the presentation. This slide also tells me it is a good depiction of the priorities for the information gathering of the intelligence agencies as a whole. We saw in the Snowden documents- NSA has what they call “selectors”- this could be a key word or email address…. In that, they would ID certain strands of DNA as selectors to be spied on and they would search every email of every scientist on the planet regarding that strand of DNA. R&D, institutions, the whole nine years. They were looking for biological findings. The have the global economic security day…. They are using these to better target individuals.
Each of these terms relate to priority areas of the intelligence agencies.
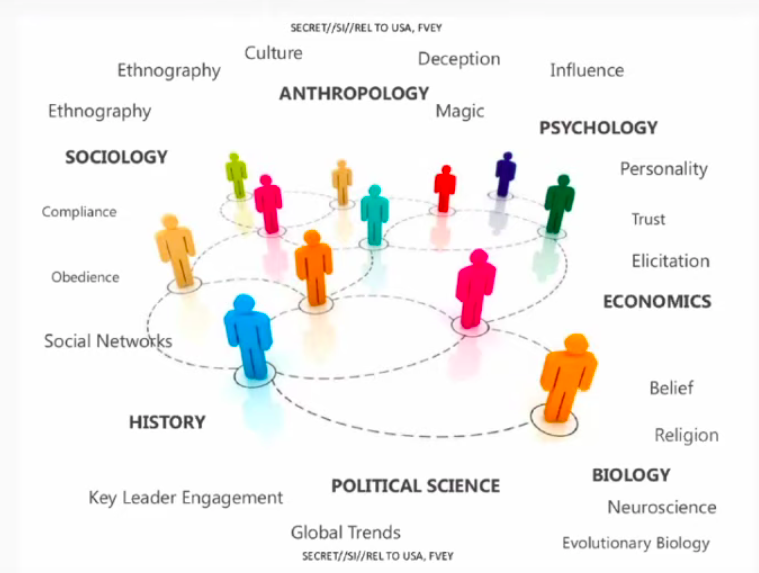
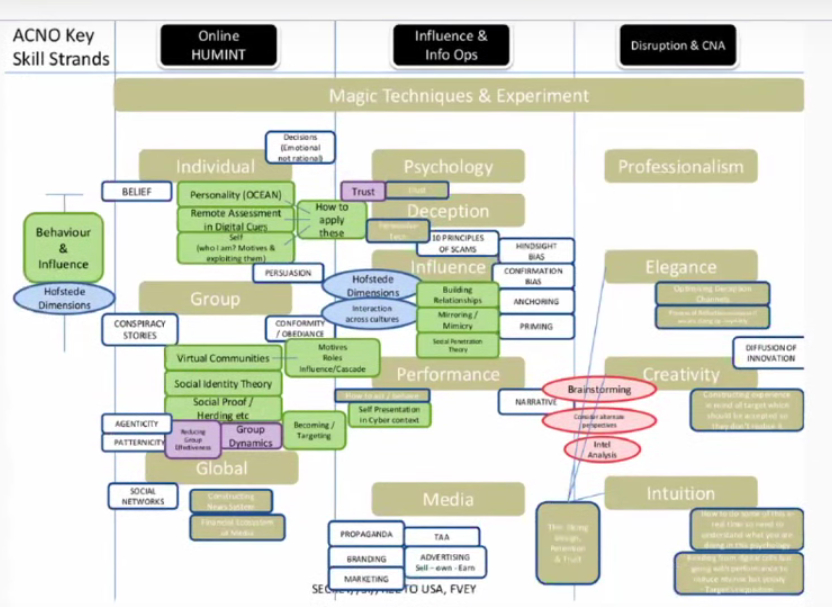
In this slide they have given us a helpful breakdown of their methods relating to these areas.
Johnson: Overall they are talking about examining the literature on magic and deception- to create perceptual illusions, to get people to not see what they are looking at, but to see something else. Influence, trust, obedience, compliance, relating to the social psychological literature. These concepts are here used to exploit people.
Since 2011, at Cambridge Analytica, they have 5000 data points on 240 million Americans based on research at Cambridge, that show that a very accurate personality profile can be gathered just from what a person clicks on online.
The relationship between personality and behavior- mass experiments have been performed on Americans already. They hope to tailor their approach to you; how to befriend you, how to deceive, influence you, etc.
The whole point of this is to get you to change your behavior…. Join a movement or leave a movement. Beliefs and religion, they are talking about changing changing your beliefs. To make people believe in things that aren’t real.
Dawson: Here we see the word “neuroscience”- there has been a tremendous amount of work and resources poured into the exploitation of neuroscience. The intelligence agencies have maintained an obsessive interest in this. Evolutionary biology is another term here.
Johnson: Re: magic. Attention is absolutely everything. Because attention is like a spotlight. Your brain sees what you attend to- only. So they manipulate attention.
Dawson: I would argue that the entire political election cycle is a spectacle of mass distraction. And of course the results of elections do nothing to change the power structure.
Compliance and obedience seem to be goals of the intelligence agencies. I would guess it also refers to what the preconditions of compliance and obedience.
Johnson: They are probably referencing the literature on these topics.
Dawson: The intelligence agencies are obsessed with studying and measuring and manipulating leadership. They are looking at the big picture, global social trends under political science. Next slide:
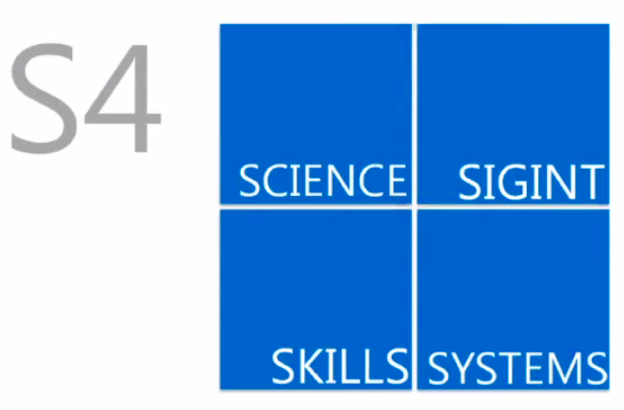
S4. The 4 S’s. Science, SIGINT, Skills, and Systems. Science refers to a lot of what we just discussed and also all the things in this document. The SIGINT (Signals Intelligence) is the electronic spying. So this is the actual invasions of our privacy that they perpetrate in order to gather their intelligence about us in order to fill out that social profile of us. Skills is the methods by which they exploit us at a human intelligence (HUMINT) level so arguably it would also refer to technical skills and performing the online human intelligence they need some kind of technical capability. And systems would refer to their information systems within the intelligence agencies. The systems they use to gather the information, analyze the information, and report on the information.
There you go: “we want to build cyber magicians.”
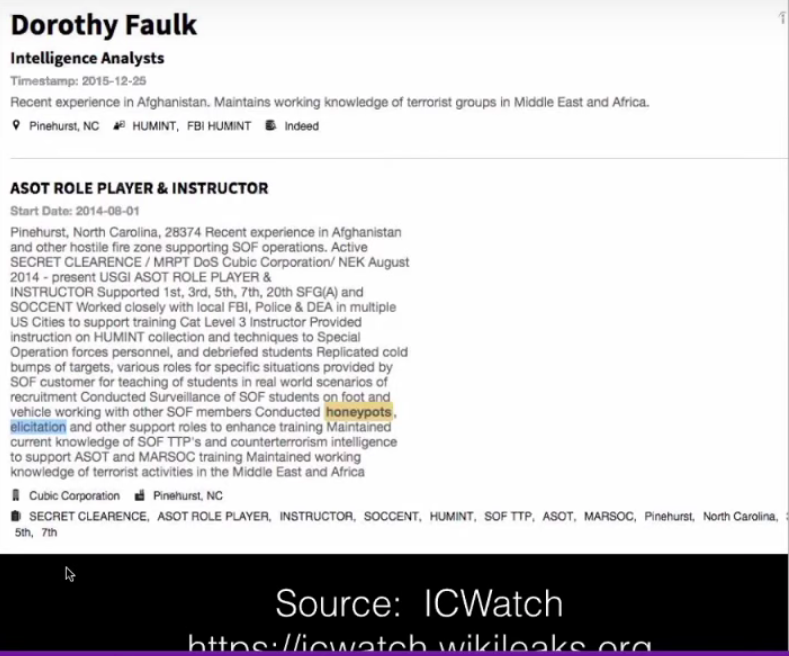
In our second episode of this series, we talked about ICWatch- the Intelligence Community watch data base that WikiLeaks published. This is a humungous file of open source information about intelligence operatives. A very savvy teenager developer was able to download all the CVs from Linkedin so researchers could study those CVs. Because in the CVs the operatives bragged about the operations they were involved in and who they were targeting. There is one I was sent tonight that is relevant to what we are talking about here. This slide from the CV of an intelligence analyst (Dorothy Faulk), she “conducted honey pots according to her and elicitation and here we go, she was an interrogator and used social networking sites, operating in both urban and rural environments. She staged questions in a manner that would lead students to give up information by the use of elicitation, sleep deprivation, deception, friendship, or unconventional methods.”
I absolutely think that elicitation is them attempting to bait someone with some method into taking an action that they otherwise would not have taken.
I wanted to quickly show this slide to bring it home to people that this isn’t just theory in a power point presentation. There are people who make a career out of doing this. There are people who wake up every single day and go to work and destroy people’s lives. And collect a paycheck and go home and then wake up and do it all over again. That’s something that just floors me. Because I can’t imagine even doing that.
Johnson: It’s difficult to believe. On that point, there will soon be a merger of GCHQ and the Ministry of Defense whose purpose is to quadruple staff dedicated to offensive as opposed to defensive online covert actions such as this and they are seeking psychologists and they have called it an online SAS.
Dawson: The reason they can call it an online SAS is first: because it is literally cyber warfare. They call it cyber warfare. And there’s a cyber warfare doctrine. And the second point is that they are not spying and information gathering as a passive exercise. They act on the information that they gain through the spying. It is an active enterprise not a passive enterprise. And in terms of the war zones, they openly state in the NSA documents about how “we are working in support of “capture and kill missions.”” Someone is going to die or be detained at some CIA black site or have whatever other unpleasant run-in with law enforcement of some variety as a result of the spying and targeting that we are undertaking.
Unfortunately, when you look at the real-world outcomes for targeted journalists and dissidents… For example, Jamal Kashoggi was a targeted journalist. He was targeted using private-sector NSO group spyware and was targeted through someone he know. They came at him through a social connection. He was targeted and it cost him his life. He wasn’t in a war zone. He wasn’t a terrorist and he wasn’t an enemy combatant. He was just somebody who was politically opposed to a regime which had sufficient money and resources to be able to hire mercenary hacking companies to provide them with software to be able to target him in such a way. So this “capture and kill” operation premise from the war zone and NSA providing technical support to those operations does expand out to the targeting of people outside of war zones who are not terrorists but who can still wind up in jail or dead or having their lives destroyed in some manner or another.
Fear is a tactic they use to induce inaction. They want you to be afraid. Personally, I think the unknown is much more scary than the known. I can say that as a target, when I didn’t understand what was happening to me or why it was it was happening, I was far more afraid, in fact I was terrified in those days, than after I learned about the targeting process. The more that I gained this information, I don’t have that cognitive dissonance. So I would think that learning information like this would empower TIs to not be scared.
We are using the magic analogy. We are showing people: oh, that’s how the magician did it. That’s how they do it. We are lifting that veil on the Wizard of Oz. At the end of the day, it’s just a bunch of dodgy old guys and whoever they can hire with a bunch of money. These people who are doing it are just cogs in a wheel that they themselves are intimidated by. And that’s why they comply with it. It’s them who are obedient and being coerced to comply within an immoral and arguably illegal system.
Can you imagine how trapped they feel? These agents know full well what will happen to them if they don’t toe the line? They are vetted for employment. They are spied on, they have to talk about their sex lives and their parents, they are exposed in the same way targets are… And even though there is the idea that this a voluntary system, they know deep down that they themselves could become the target. And that is living in a state of fear.
When you understand that you are compliant with the “architecture of oppression” you have to feel trapped.
The second thing is that…. every single person is a target, that’s what mass surveillance is. Massive surveillance is the wholesale targeting of a population. The question is to what extent are you individually or personally targeted. Individual targeting is a different kettle of fish.
The FBI came to New Zealand and raided Kim Dotcom’s mansion and then Occupy Auckland.
The fundamental reason that they targeted me, I’ve learned this from their own documentation, is that they deem me to be a “radical.” When they first look at people they classify them into four different categories.
1) Opportunist- they can give you some bribe or career opportunity and lead you away from activism that way.
2) Idealist- utopian- therefor you can be disillusioned and go after your idealism and dissuade you
3) Realist- they use pessimism and deter you that way
4) Radicals- those they determine will not stop or sell out, they are incorruptible, people like Julian Assange.
I was working in the software industry and walked away from it for a job that made no money, as a journalist. I figured I owe this to this planet.
The radicals are a minority. What we need is to be a bit more radical as a society. And not have individuals who are martyred and hung out to dry. We have to take some responsibility en masse.
What I tell people is: You don’t have to do everything, just do something. Just do one thing.
Johnson: The spectrum of targeting. Most of the targeting is to try to disrupt the movement.
Dawson: These influence operations are being applied to millions of people. It’s not about capture and kill at all. It’s just about change your opinion about something.
Johnson: Since 9/11, the definition of terrorism is someone who seeks to alter or influence government policy. That’s anybody. So then the term “criminal” could be used to encompass activists.
In their documents, the perps were expressing some concerns about the ethics of what they are doing.
Dawson: You talk about social pressure creating compliance. I think a large portion of the work force of these intelligence agencies that are in a social pressure cooker feel they have to comply but they know full well that what they are doing is wrong. They know they are not targeting terrorists.
This is mind boggling to me. I am not a violent person. No criminal history. No violence or intention of violence whatsoever. A single mother from the suburbs. And to have military agencies and military resources used to target me is the just the most egregious abuse of the public contract. And we are seeing that on a wide scale here. Because ultimately this is military grade targeting, whether its farmed to contractors or whatnot, on civilian populations. And that is not what the military is for. I’ve often said that these guys need to be shut down.
I’m not OK with them spying and targeting people who are engaged in protected democratic activities that we’ve always been told we have the right to do and with us being different and better than non-democratic countries. It’s not that I’m anti-spy, per se. I’m anti-abuse by spies.
CIA is supposed to be a foreign intelligence service. A foreign intelligence agency does not spy on its own citizens. They are creating a system of control- of totally controlling the population and the society. And restricting our ability to progress as a society. And it’s anti-democratic and deeply offensive. They have created their own opposition. It’s despicable. Next slide:
Here’s their slide and manual for “online covert action:” First column is online human intelligence, second column is influence and information operations, and third column is disruption and CNA attacks.
Magic techniques and experiments- targets can be an individual, the group, and global.
NSA calls their behemoth operation in over 100 countries the “Global Network.” They always use the world global. They talk about our global awareness. Global, global, global. They want total global control. We see that right here.
Lissa: Very broad scope… scalable.
Dawson: We see the words “elegance,” we’ve seen that these guys are absolutely focused on not getting caught. I think what they are talking about is deniability. They want to be able to dress it up as being something other than it is. For example, “Occupy Auckland” Twitter account got hacked…. then they deleted all the tweets and it started tweeting out tweets in the Russian language. What is the likelihood that the Russian intelligence services were behind this? So this was a method of distraction, a cover and method of deniability to mask who did it. It could have been any of the 5 Eyes or Israel. We’ll never know.
So they would regard this as a “creative,” “elegant” operation. They successfully masked the source of the intrusion and attack and they achieved the outcome they wanted which was to deny us access to our account and the ability to communicate our messages. “Professionalism” probably means the way they operate in their team structures. Like the NSA run actual development teams… They just happen to be building systems for the military that do nasty things. They use the same kind of dynamics.
Intelligence agencies refer to themselves as businesses. They call themselves “the Business” and “The Corporation”. There actually is an NSA Corporation. They function just as if they are private enterprise business even though they are actually not supposed to be.
Johnson: These documents commonly talk about conducting “false flag operations.” So this is not at all a conspiracy theory.
Dawson: Absolutely. In the CVs of these intelligence operatives you can find hundreds of people saying they conducted false flag operations in the ICWatch documents.
So here is our next slide: It is massive; they are breaking it down for us.
Johnson: This slide gets into the nitty gritty of the psychological tactics. Re: Personality- OCEAN is at the heart of the Cambridge Analytica system. It is commonly used in personality measure and way to understand personality research along 5 dimensions, where O = openess; C = consciensciousness, E = extraversion; A = agreeableness; and N = neuroticism (emotional stability). NSA remote assessment uses digital cues… there is a large literature, some public, some private, it’s possible to put together personality profiles based on their digital footprint.
So this system gives the NSA and their partners the information they need to determine how best to exploit your personality, based on your remotely acquired personality profile.
Dawson: There is a spectrum, so that infers that there must be different methods of targeting used on TIs.
Suzi 3D
Courageous Kiwi journalist Suzie Dawson and a special guest take us to school on the GCHQ’s (UK NSA) infamous JTRIG – Joint Threat Response Intelligence Group that smears, infiltrates and sabotages the lives of targets online!
The existence of JTRIG was revealed in the Snowden documents and a 50 slide set was published by The Intercept in 2013. This Sunday we break down each of those slides and decipher the methodology employed within.
Watch the full first episode here: https://www.pscp.tv/1vs5i/1djxXRzPRBLGZ
This is a #1vs5i campaign event. Donate to support Suzie’s fight for justice and accountability at: https://gogetfunding.com/help-a-kiwi-…
Spread the word:
Movement hashtag: #1vs5i
Official website: http://1vs5i.com/
Official Twitter: @1vs5i
Official Facebook: https://www.facebook.com/1vs5i
Short #1vs5i Promo Vid: https://youtu.be/0-IlSOrVaiM
MEDIA INQUIRIES: media@1vs5i.com
GENERAL INQUIRIES: contact@1vs5i.com
Other Twitter accounts to follow: @Suzi3D
@HelpSuzi3D
Multistreaming with https://restream.io/
20 Comments
humanidee
1 year ago
I am so grateful for this episode. My Twitter (at/humanidee) has been targeted by trolls, and reported as using hate speech. I was not given evidence of the post(s) that brought about my permanent ban, and I can’t create another account.
I have been expelled from the most active space to have discourse and keep updated about the things that matter to me, like WikiLeaks and Julian Assange.
Donald Flett
7 months ago
Very informative and well documented discussion. Thank you.
JT
10 months ago
The eye of sauron. Perfect.
Hollis Hurlbutt
1 year ago
If there’s anything you can do to un muddy the guest vocals id love to hear the full statements but her flare makes the sound sort of trail off every statement
David Jonathan Allan
1 year ago
The terrorist watch list is s scam made up mostly of non investigative persons of interest. I haven’t met a single real terrorist in it yet. Needs to be said.
John Mastroligulano
1 year ago
Well the Q thing should be seen for what it is hence the use of 17/AG/Q. Then again most people have no idea of the functional meaning of letters-words-shapes-numbers.. So :-/ Knowing hieroglyphs helps since they(the “elite”) use those symbols quite frequently hence your $. Q in hieroglyph means HILL or infinity/8 ILL meaning dead or the grave or the Q or Kurgan as they used Hills as burial mounds like a pyramid but a DUN HILL which is what HAMILTON means the name it says on my birth cert which is from the Hamilton’s of Alexander $10 fame the one who helped the bankers here originally hence his position as the 1st Secretary of the Treasury. I changed my last name since they never really said anything to me & my father left when I was little, ok enough about me. What is above a grave= SKULL & BONES, where was one of the places Snowden said he worked in that interview=he said it was called HILL. Much like how they use Krypton many movies-stories-shows are using all of this symbolism you just don’t know it you can’t decipher data like some of us can likely because of genetics more precisely “cursed with knowledge” of Infinity(H-8) war meaning. Q is also used in Star Trek & is the basis if the first episode of the original & the first/last of the second series STNG where if you actually think they are saying that you/I/we never really leave the Q/cage/test/cube/prison for your mind hence the character Q saying the trial never ended, it never does end. This is also what those sphere within sphere mean at Vatican & elsewhere which is what HitchHiker’s Guide is showing hence Deep Thought it’s also what CERN means to do as ER is the symbol of to do or double you the Chick in Hieroglyph & also the Queens symbol ER/ERll & it means to do that within CN which CN=CAD=314 means creation hence ABRA CAD ABRA meaning so it means to within creation within AI constructs to build another or like what they say that project is for= to find & usurp the god particle or that which imparts mass======CHOICE hence that Matrix NEO saying. Hence ORDO AB CHAO meaning you think you have choice but it doesn’t exist. Order through entropy through building things to break so you scream out for government to do this or that & then they do what they always intended & nothing gets better not for good conscious people that is. Good luck you deserve it I really do not appreciate rigged games especially involving life. If there ever is something substantial I can do to help when that time comes I will for now I’m compartmentalized to prevent me doing so this is what is meant by red dress people who are human shields preventing what I am or the like from ending this or like what NEO says in the phone booth.
humanidee
1 year ago
Advertising can affect biology – sonic attacks and sublime suggestions to consume sugar, caffeine, fats, nicotine and salt, combined elicits biological processes that induce stress.
cat whatever
1 year ago
I always watch but the audio from your guest was poor. I saw her with Elizabeth Vos today on another interview and the audio was also very poor….which means it’s on her end. She might want to know this feedback as she has such interesting things to say….which I could not hear…..on either interview. Also, speaking in low mumbling tones does not help either. Just friendly feedback; had to turn off the podcast after a short time. And I wanted to hear her. Thanks for all you do…you’re great!
Daniel Johnson
1 year ago
The first hour is gone.
wdpk837
1 year ago (edited)
Someone in the live chat mentioned compiling a database of possible spooks. This already exists in the form of Cryptocomb (a project of the website Cryptome, which compiles national security literature). It can be found at cryptocomb.org and I would encourage anyone to contribute.
Jonathan Plumber
1 year ago
Look up the invention of the Neurophone an invention where a voice can be transmitted into a targets head to influence and directly speak to a target this can be used to influence all religious and political targets
A J
1 year ago (edited)
2:13:54 Who’s voice is that? Sounds like a man’s voice or is it the poor quality of sound??
A third voice can be heard saying: Oh wow!
Anybody else on the call?
johnba291972
10 months ago
Ok well its starting to sound interesting now at 11:30ish, but I very nearly turned off. Can’t you cut the first 6 and a half minutes from this video and reup it? I can imagine a lot of people are not watching because they’re thinking it has no content after a couple of minutes or so.



Have you guys checked out “Wikifreaks” on Bing/Google dig around and you will find UK siyes!