Episode 8: Opening the Five Eyes: Deciphering UK’s JTRIG (Joint Threat Research Intelligence Group) Suzie Dawson, 11/10/19)
Epigraph Quote:
The level of sophistication (of these operations) is so high. And the expended resources is almost limitless. When I studied the Snowden documents, we studied the processes of the NSA targeting centers. It shows the work flows of these social media targeting qnd analysis centers, and you discover that every target has dozens of agents working through the life cycle of that target. So you’re not dealing with one person, you are dealing with teams of assholes who have brainstormed their assholeishness.
You are dealing with multiple layers of authority and multiple centers of specialization. There’s a whole team just for dealing with investigating your family and your friends and the people around you who are then producing reports on that for the people who are targeting you. There’s a team for the actual interactions with you. There’s a team for the CNA (computer network attacks), the intrusion of all your devices. It’s not just one person that is destroying your life. It’s coordinated teams of specialists destroying you life.
Once you come against that level of sophistication, anything that confronts you in your life could have anything behind it. And you would never know. So everything becomes untrustworthy.
Suzie Dawson
Webmaster Introduction: “The Global Network” (aka “NSA Global Spy Network”) IS “the architecture of oppression” that rules and shapes the world. Drawing on her experience as a TI and a journalist-researcher, Suzie Dawson exposes this “architecture of oppression” in her 10-part series: “Opening the Five Eyes: Exposing the Spies.” The system is comprised of covert SIGINT (Signals Intelligence) and HUMINT (Human Intelligence) ops carried out by the NSA, CIA, DOD, FBI, DHS, and NATO, etc., in the US, the UK Ministry of Defense GCHQ, JTRIG, MI6, MI5, etc., in Britain, the IDF, Unit 8200, Mossad, Shin Bet, etc., in Israel, and their equivalents in over 100 other nations. Cooperating private security and intelligence contractors and their hired thugs (aka “surveillance role players,” “counterterrorism specialists”) execute street level operations and psychological attacks. The Global Network secretly surveilles, targets, and destroys honest, incorruptible activists, journalists, “dissidents,” scientists, truth-tellers, and innumerable others who have been secretly watchlisted and flagged as “potential terrorist threats” or considered “enemies of the state,” “enemy non-combatants,” “extremists,” “radicals,” or “persons of interest,” etc.
This horrific, reprehensible, and criminal “social engineering” system, aka “The National Security Racketeering Network,” is a “growth industry.” It is the largest black and black-market op AND “Crime Against Humanity” in human history. It radically ramped up after 9/11 and continues to expand across the globe today as a for-profit enterprise.
In episodes 6 through 9, Dawson and guests analyze documents from JTRIG (Joint Threat Response Intelligence Group), a part of GCHQ (Government Communications Headquarters; the British equivalent of the NSA) and expose the manuals, psychological tricks, methodologies, and protocols deployed in these nefarious operations. My opinion is that these psychological warfare techniques derive mainly from government-military-intelligence agencies’ weaponization of psychology and other sciences conducted by Britain’s Tavistock Institute (1921 onward) and the US governments’ Macy Conferences-CIA MKULTRA+ mind control programs (1947 onward).
The satanic nature of these programs cannot be dismissed. The Christian ethos of “love thy neighbor,” the very underpinning of Western Christian civilization, is hereby replaced by a comprehensive system of psychological abuse, trauma, and torture which, in effect, is the overt expression of “hate, degrade, deceive, and destroy thy neighbor.”
‘Cursed is anyone who attacks (kills, strikes, smites down, smites) a neighbor in secret.’ And all the people will reply, ‘Amen.’
Deuteronomy 27:24
I believe this curse now extends to the agencies, police units, businesses, nations, scientists, academics, populations, and individuals that participate in, financially support, and/or tacitly acquiesce to this (beyond) despicable torture-murder system. Apparently, hell is now expanding exponentially both in this world and the next.
Suzi 3D
Courageous Kiwi journalist Suzie Dawson and a special guest take us to school on the GCHQ’s (UK NSA) infamous JTRIG – Joint Threat Response Intelligence Group that smears, infiltrates and sabotages the lives of targets online!
The existence of JTRIG was revealed in the Snowden documents and a 50 slide set was published by The Intercept in 2013. This Sunday we break down each of those slides and decipher the methodology employed within.
Watch the full first episode here: https://www.pscp.tv/1vs5i/1djxXRzPRBLGZ
This is a #1vs5i campaign event. Donate to support Suzie’s fight for justice and accountability at: https://gogetfunding.com/help-a-kiwi-…
Spread the word:
Movement hashtag: #1vs5i
Official website: http://1vs5i.com/
Official Twitter: @1vs5i
Official Facebook: https://www.facebook.com/1vs5i
Short #1vs5i Promo Vid: https://youtu.be/0-IlSOrVaiM
MEDIA INQUIRIES: [email protected]
GENERAL INQUIRIES: [email protected]
Other Twitter accounts to follow: @Suzi3D
@HelpSuzi3D
Multistreaming with https://restream.io/
Webmaster’s Transcription of Highlights of Video:
Suzie Dawson: I apologize for the delay in starting tonight’s episode, which is the third in the series on the JTRIG files. We’ve been digging into the Snowden files, the Wikileaks files, and some of the manuals of the intelligence agencies, and some of the egregious conduct they have been engaging in.
The JTRIG files employ a lot of psychological language and clinical psychologist, Lissa Johnson, has been helping us to understand what this terminology means. And I’ve been giving my personal experiences regarding the more practical side of how these tactics are employed against us.
We’ll pick up where we left off last time.
There was a major bit of progress this week regarding Martin Bradbury, an independent journalist in New Zealand. This week the police in New Zealand confirmed that he was targeted, that his bank accounts were interfered with, he was flagged as a person of interest, he was denied loans, information about him was taken without a warrant. He has fought a battle against them for 5 years. This week the police withdrew their case against him and issued a formal public apology to him. They had done this under the guise of computer fraud. Of course, this was a lie. He is now the third person who has successfully sued the police. The police are one of 5 agencies that I am in the process suing for their abuses against me and my family. The police have a confidential settlement with Martin that they have agreed to.
Lissa K. Johnson (clinical psychologist) please take it away:
Lissa: Last week were about 2/3 of the way through the JTRIG files.
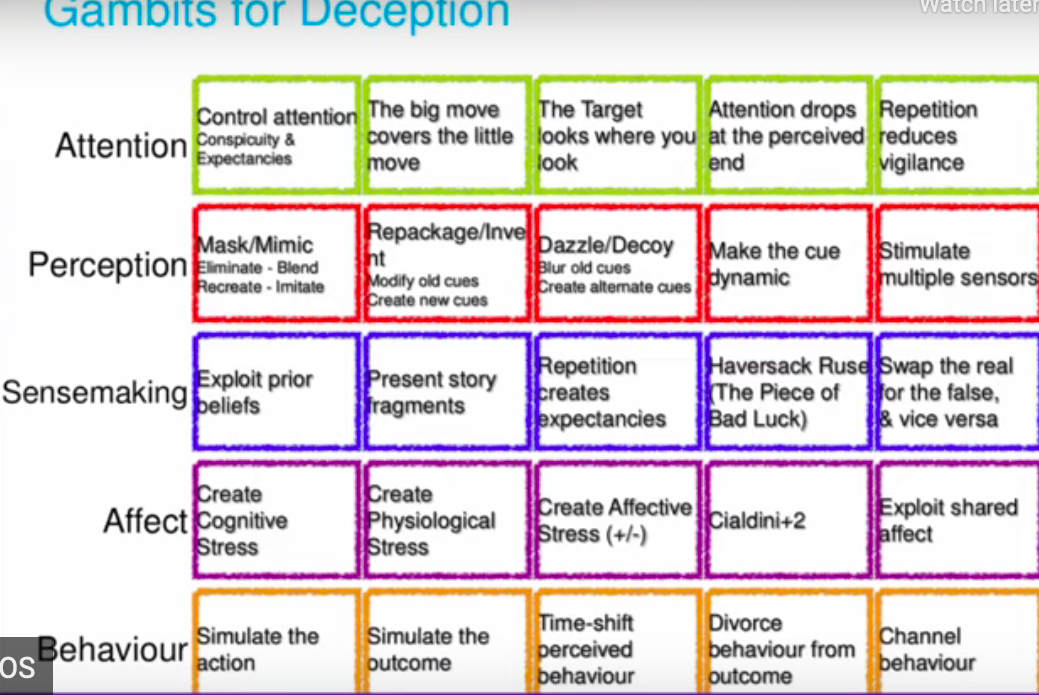
We have been talking through psychological strategies whose purpose is to deceive people, and discredit targets, and degrade and disrupt and destroy.
We talked about how they are able to trick people into seeing things. Instructing GCHQ staff in how to create stress. Here we see how the knowledge of psychology is misused to create stress and harm targets.
Cialdini came up with the 6 principles of persuasion. In the next slide they combine these 6 principles with the 7 principles of scams. They are saying that when you create stress in someone, people are more manipulable and susceptible…. Group belonging becomes a more powerful force to exploit. When people are frightened they are more likely to look for authority figures to make them feel safe. The next slide talks about exploiting. One principle is that people say yes to what to what they like. Conformity and herding are desired goals. Exploiting emotions…
Mostly it’s self-explanatory. They talk about faking things. They talk about befriending a target to get them to behave in a certain way. To make certain things happen in the real world or the online world. Fake book chapters, fake texts or emails. They talk about fake victim posts… It’s all about mimicry. They want to alter the sequence of events.
Suzie: What you were saying about war propaganda. There was a US Air Force operation where they dropped 36 tons of bombs on what they said was an ISIS island… They had photographs of the island- you couldn’t see any structures. There was a nice music playing and you see these bombs going off like a fireworks show. I’m pretty sure carpet bombing this island would have killed many, many women and children. So this is classic war propaganda. This is legitimization of violence.
In the slides we see the cross-over between the digital targeting and real world impacts. Their language is so passive…. Making something happen. That something could be driving someone to suicide. Really what they are doing is creating a tsunami in someone’s life.
Lissa: They are faceless, masked people. This slide is about conformity, I guess.
(Webmaster comment: Under Covid-19 restrictions, all the masked people in the world today are similarly rendered faceless! Probably this is not about health at all! It is psychological abuse!)
Suzie: It seems like they are using some kind of Islamophobia to make it appear that their targets are terrorists. They have to “otherize” their targets.
Lissa: We see this slide: Online Covert Action: Strand 2: Influence and Information Operations
The definition of Information Operations from a Joint Chiefs of Staff document is: Information Operations (IO) = “The integrated employment of information-related capabilities in concert with other lines of operations to influence, disrupt, corrupt, or to usurp the decision-making of adversaries and potential adversaries.”
Suzie: On this slide, they also talk about online covert action accreditation. So you get a little certificate once you’ve learned how to destroy people’s lives.
Lissa: They are talking about cognitive infiltration of people’s minds and covertly influencing people’s minds. These are the 10 principles of influence. In the psychological literature there are 7 principles of scams and 6 principles of persuasion. And they’ve kind of combined them here into 10 principles.
The time principle is that when you put people under time pressure they are much more manipulable because they take mental shortcuts. If you want to exploit people’s psychological vulnerabilities it’s much easier if they under time pressure. The “need and greed principle” is from the 7 principles of scams. It was put together by a guy who does cyber security. Need and greed is about exploiting people’s emotional needs, needs for status, accolades, and achievement. They can use that as a way to exploit someone.
The “deception principle” is basically using all these principles to deceive people- which is what these slides are all about. The honey trap (honeypot) is an example of the “dishonesty principle.” It’s luring someone into doing something dishonest and using that to elicit their compliance. It’s kind of blackmail. It’s used in scams. Social compliance to authority. The “herd principle” is conformity; the tendency to look to others in your own group to guide your own behavior, thinking, and attitudes. The “consistency principle:” people like to behave in ways they’ve already behaved. A tactic is to make a small request, and then build on that. The “distraction principle” includes misdirection, dazzle. Russia-gate is an example. While people were being distracted, our freedoms and rights were lost.
“Reciprocity principle.”
Suzie: The time principle I seen the other way around. There is a short time frame and they have to act to counter you in that short time frame. Sabotage is revealed to you at the crucial moment. You don’t see it coming. I have seen that many times.
Lissa: Personality can be fairly accurately assessed by online activities thanks to Cambridge Analytica. Adoption of new products slide. Here they are talking about selling a deception rather than a product.
Suzie: The motivation of the innovator is they are looking at what will this be in 10 years.
If we sum this up, this is the industrialization of manipulation.
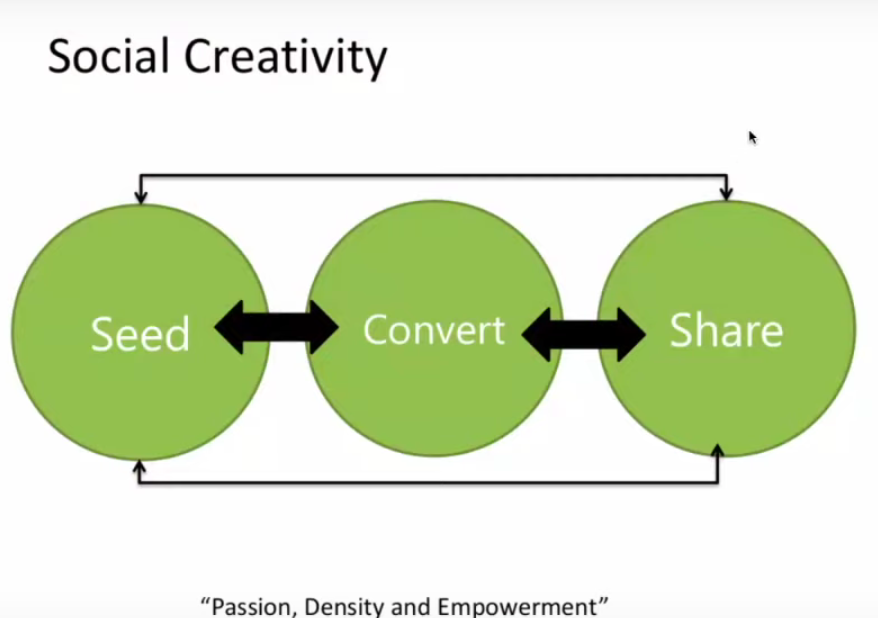
Lissa: Social Creativity. It fits into what we were talking about brand acceptance.
Suzie: I saw a lot of this. They would seed disinformation about people to as broad an audience as possible to discredit them. And then would wait for the feedback and then reference that. The Chinese whisper gets seeded… it’s the “laundering” smear process. They’ll seed the smear, they’ll wait for it to reverberate through the group, and then take the reverberated version and repeat that.
They seed the smear, they convert the smear, and then they share it as if they just heard it.
Lissa: Online HUMINT: About assessing people’s personalities by remote assessment of digital cues. Cambridge Analytica in 2016 used 5 factors of personality- manipulable voters.
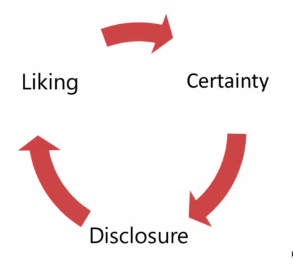
In order for relationships to progress, people need to get to know them better. Disclosure ties in with social penetration theory. As relationships progress, people gradually disclose to a greater extent. This is used as a tactic for befriending targets.
How can I use this to exploit and deceive people? How can I game this?
Suzie: The mimicry and mirroring is not just digital, it’s also physical. If they want to pretend to be an activist, it will be the guy with dreadlocks and funny spectacles who smokes weed. They’ll take their stereotypes of how they see activists and adopt those characteristics in the people they infiltrate into the group. In New Zealand, the spycops are always the people with the funny hats, the funny wigs, funny hair; there’s always exaggerated characteristics. I think that is part of this magician stuff. They want to draw your attention. It’s part of the guise, part of the mask. They have physical characteristics that are unmissable.
They do take on these personnas that they think activists will be least likely to be suspicious of.
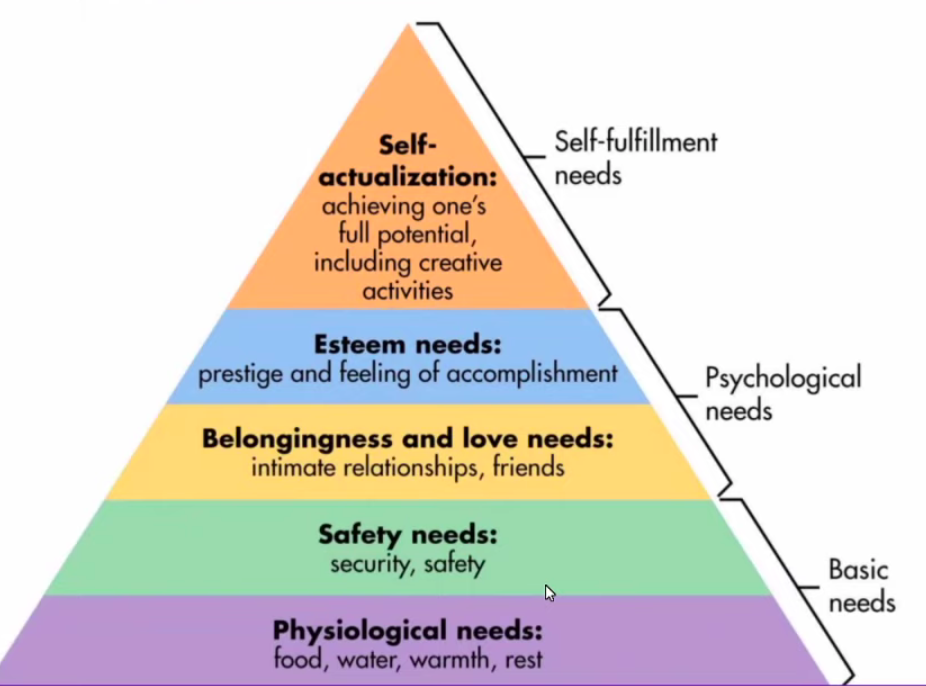
Lissa: This is Maslow’s hierarchy of needs. This is a bit old fashioned in psychology.
When they talk about exploiting people, these are the basic emotions and needs.
Suzie: From the perspective of a manipulator wanting to build trust with a target or activist, to convince someone you love them and care about them, you have to exhibit concern. I’m thinking about the camp mother at Occupy Auckland…. each of these needs can be exploited by a manipulator who mimics the behaviors and signals of someone who really cares about you or who genuinely loves you. This is why this is so criminal. They play on this for nefarious means and in damaging ways. This causes the breaking of trust. Then when someone genuine comes along you can’t trust them. This causes genuine long term psychological damage to the victim.
Meanwhile, the perps get these certificates of award and I’m sure they get morning tea.
Lissa: You can target all these needs to befriend somebody.
Suzie: The first thing they will figure out, they will exploit whatever needs people have. Most people need love. It is most common to exploit people’s needs for love and intimacy.
Lissa: They talk about how to discredit a target. They talk about honey traps. These things are potentially incredibly damaging emotionally. You don’t know what someone’s childhood history is… You don’t know what you are doing to somebody when you pretend to create emotional intimacy and then betray someone.
Suzie: The level of sophistication is so high. And the expended resources for these operations is almost limitless.
When I studied the Snowden documents, we studied the processes of the NSA targeting centers (I highly recommend you look at some of those videos). And it shows the work flows of these social media targeting qnd analysis centers, and you discover that every target has dozens of agents working through the life cycle of that target. So you’re not dealing with one person, you are not dealing one twisted person, like you might in the real world…. you have a bad relationship with someone who is a narcissist or whatever. When you are dealing with these people, you are dealing with teams of assholes who have brainstormed their assholishness. Sorry, I can’t come up with a better word for it because it’s so immoral and egregious.
You are dealing with multiple layers of authority and multiple centers of specialization. There’s a whole team just for dealing with investigating your family and your friends and the people around you who are then producing reports on that for the people who are targeting you. There’s a team for the actual interactions with you. There’s a team for the CNA (computer network attacks), the intrusion of all your devices. It’s not just one person that is destroying your life. It’s coordinated teams of specialists destroying you life. I think that’s one thing that is really hard for people to get their head around.
Once you come up with the level of sophistication, anything is possible. Because once you come against that level of sophistication, anything that confronts you in your life could have anything behind it. And you would never know. So everything becomes untrustworthy. And how I discovered to deal with that is:
1) To study the methodologies employed in all the people, and
2) to go the opposite way and give everybody a chance.
So when I run campaigns, I let strangers join my social media by the hundreds or thousands. I deliberately make myself open to large numbers of people rather than try to attempt to protect myself in small environments which are inevitably penetrated by these highly sophisticated actors. So I dilute their effectiveness by using mass numbers.
Lissa: Yes, one of their goals is to make people mistrustful, so that you don’t get a support network.
Suzie: Yes, their agenda is always isolation, so anything that combats that is a win in my book.
I really want to get into the group dynamics slide and how they fracture groups when we continue this series next week. This is key to how they destroy movements.